
This the multi-page printable view of this section. Click here to print.
Documentation
- 1: Getting Started
- 2: Usage
- 2.1: Command Line Options
- 2.2: Server mode
- 2.3: In-file Instrumentation
- 2.4: Configuration File
- 3: Integrations
- 3.1: Kubernetes Admission Controller
- 3.2: Argo CD
- 3.3: Atlantis PR Automation
- 3.4: GitHub and GitLab
- 3.5: Pre-commit hook
- 4: Architecture
- 5: Policies
- 5.1: Policy Overview
- 5.2: AWS Policies
- 5.3: Azure Policies
- 5.4: GCP Policies
- 5.5: GitHub Policies
- 5.6: Docker Policies
- 5.7: Kubernetes Policies
- 6: Contribution Guidelines
- 7: Changelog
1 - Getting Started
Terrascan is a static code analyzer for Infrastructure as Code. It can be installed and run in a number of different ways, and is most commonly used in automated pipelines to identify policy violations before insecure infrastructure is provisioned.
Running Terrascan for the First Time
Quickly get started with these common first tasks:
Installing Terrascan
Terrascan is a portable executable that does not strictly require installation, and is also available as a container image in Docker Hub. You can use Terrascan in two different methods based on your preference:
Native executable
Terrascan’s release page includes latest version of builds for common platforms. Download and extract the package for your platform. Follow instructions that apply to your platform:
macOS and Linux
Download the latest version of builds for macOS and enter the following command.
Note: for linux, replace Darwin with Linux
$ curl -L "$(curl -s https://api.github.com/repos/tenable/terrascan/releases/latest | grep -o -E "https://.+?_Darwin_x86_64.tar.gz")" > terrascan.tar.gz
$ tar -xf terrascan.tar.gz terrascan && rm terrascan.tar.gz
$ install terrascan /usr/local/bin && rm terrascan
$ terrascan
If you want to use this executable for the rest of this quickstart, it will help to create an alias or install the executable onto your path. For example with bash you could do something like this:
$ sudo install terrascan /usr/local/bin
or:
$ alias terrascan="`pwd`/terrascan"
Windows
Download the latest version of builds for Windows and enter the following command:
tar -zxf terrascan_<version number>_Windows_x86_64.tar.gz
Using a Docker Container
Terrascan is also available as a Docker image in Docker Hub and can be used as follows (assuming you have Docker installed):
$ docker run --rm tenable/terrascan version
If you want to use the Docker image for the rest of this “Getting Started” guide, please refer to the following command. Note the volume (-v) that is being mapped to the docker, and modify it if necessary to suit your environment.
$ alias terrascan="docker run --rm -it -v "$(pwd):/iac" -w /iac tenable/terrascan"
Note: This command includes a few extra options to enable Terrascan has access to the current directory when it is run.
Scanning with Terrascan
Example of interactive scan or using CLI
In this example, the KaiMonkey project contains some vulnerable Terraform files to scan. To run a scan, follow these steps:
$ git clone https://github.com/tenable/KaiMonkey
...
$ cd KaiMonkey/terraform/aws
$ terrascan scan
By default Terrascan will output its findings in human friendly format:
Violation Details -
Description : S3 bucket Access is allowed to all AWS Account Users.
File : modules/storage/main.tf
Line : 104
Severity : HIGH
-----------------------------------------------------------------------
Description : S3 bucket Access is allowed to all AWS Account Users.
File : modules/storage/main.tf
Line : 112
Severity : HIGH
-----------------------------------------------------------------------
Description : Ensure that your RDS database has IAM Authentication enabled.
File : modules/storage/main.tf
Line : 45
Severity : HIGH
-----------------------------------------------------------------------
Description : Ensure VPC flow logging is enabled in all VPCs
File : modules/network/main.tf
Line : 4
Severity : MEDIUM
-----------------------------------------------------------------------
Description : EC2 instances should disable IMDS or require IMDSv2
File : modules/compute/main.tf
Line : 124
Severity : MEDIUM
-----------------------------------------------------------------------
Description : http port open to internet
File : modules/network/main.tf
Line : 102
Severity : HIGH
-----------------------------------------------------------------------
Description : Enabling S3 versioning will enable easy recovery from both unintended user actions, like deletes and overwrites
File : modules/storage/main.tf
Line : 104
Severity : HIGH
-----------------------------------------------------------------------
Description : Enabling S3 versioning will enable easy recovery from both unintended user actions, like deletes and overwrites
File : modules/storage/main.tf
Line : 112
Severity : HIGH
-----------------------------------------------------------------------
Description : AWS CloudWatch log group is not encrypted with a KMS CMK
File : modules/compute/main.tf
Line : 115
Severity : HIGH
-----------------------------------------------------------------------
Scan Summary -
File/Folder : /var/folders/2g/9lkfm6ld2lv350svwr15fdgc0000gn/T/x9wqg4/terraform/aws
IaC Type : terraform
Scanned At : 2021-01-15 03:11:31.869816 +0000 UTC
Policies Validated : 571
Violated Policies : 9
Low : 0
Medium : 2
High : 7
You should see a total of 9 violations, which are detailed in the output.
Now that you understand how to run Terrascan, you can explore various options available. The usage page covers the options in detail. For more information, see Related resources.
If you do not want terrascan to use os.TempDir() for downloading/cloning of remote repository, terraform module or template files you can specify the directory to use by setting TERRRASCAN_CUSTOM_TEMP_DIR environment variable.
Related resources
- The usage guide explains general usage, how to scan other types of IaC (such as: Kubernetes, Helm, and Kustomize), List of other IaC providers (e.g. Kubernetes, Helm, etc.), instructions to limit the scan to specific directories or files, and generating the output in different formats.
- The CI/CD page explains how to integrate Terrascan on CI/CD pipelines.
- Terrascan Policy Reference
2 - Usage
For steps to install locally, or run Terrascan from docker, see this section.
Building Terrascan
Terrascan is a Go binary that you can build locally. This is useful if you want to be on the latest version, or when modding Terrascan.
$ git clone git@github.com:tenable/terrascan.git
$ cd terrascan
$ make build
$ ./bin/terrascan
Using Terrascan
This section provides an overview of the different ways you can use Terrascan:
- Command line mode provides list of Terrascan commands with descriptions.
- Server mode using Terrascan as API server
See Configuring Terrascan to learn more about Terrascan’s configuration file.
See In-File Instrumentation to learn how to granularly customize your scan based on particular resources and rules. For example, by skipping certain rules or resources.
Integrations
Terrascan can be integrated into various platforms and configured to validate policies to provide run time security. Currently Terrascan supports the following integrations:
2.1 - Command Line Options
This section contains the following information:
The following is a description of all the commands available. Terrascan’s interface is divided into subcommands as follows:
init= Initializes Terrascan by downloading the latest Rego policies into ~/.terrascan. The scan command will implicitly run this before a scan if it detects that there are no policies found.scan= scans Infrastructure as code files based on the policies contained within the “.terrascan” directoryserver= Starts the Terrascan’s API serverhelp= You can view the usage menu by typinghelpor using the-hflag on any subcommand (e.g.terrascan init -h). You can also view this by typingterrascanwithout flags or other arguments.
Terrascan Commands
$ terrascan
Terrascan
Detect compliance and security violations across Infrastructure as Code to mitigate risk before provisioning cloud native infrastructure.
For more information, please visit https://runterrascan.io/
Usage:
terrascan [command]
Available Commands:
help Provides usage info about any command
init Initialize Terrascan
scan Start scan to detect compliance and security violations across Infrastructure as Code.
server Run Terrascan as an API server
version Shows the Terrascan version you are currently using.
Flags:
-c, --config-path string config file path
-h, --help help for terrascan
-l, --log-level string log level (debug, info, warn, error, panic, fatal) (default "info")
--log-output-dir string directory path to write the log and output files
-x, --log-type string log output type (console, json) (default "console")
-o, --output string output type (human, json, yaml, xml, junit-xml, sarif, github-sarif) (default "human")
--temp-dir string temporary directory path to download remote repository,module and templates
Use "terrascan [command] --help" for more information about a command.
Initializing (optional)
The initialization process downloads the latest policies from the repository into ~/.terrascan.
By default the policies are installed here: ~/.terrascan/pkg/policies/opa/rego and are fetched while scanning an IaC.
Use the following command to start the initialization process if you are updating the policies:
$ terrascan init
Note: The
initcommand is implicitly executed if thescancommand does not find policies while executing.
Scanning
If the scan command is used with no arguments (as shown below), the scan will include all supported cloud providers on Terraform HCL files:
$ terrascan scan
The scan command supports flags to configure the following:
- Specify a directory to be scanned
- Specify a particular IaC file to be scanned
- Configure IaC provider type
- Directory path to policies
- Specify policy type
- Retrieve vulnerability scanning results from docker images referenced in IaC
The full list of flags for the scan command can be found by typing
terrascan scan -h
Scanning current directory containing terraform files for AWS Resources
The following will scan the current directory containing Terraform HCL2 files for AWS resources:
$ terrascan scan -t aws
Scanning for a specific IaC provider
By default, Terrascan defaults to scanning Terraform HCL files. Use the -i flag to change the IaC provider. Here’s an example of scanning kubernetes yaml files:
$ terrascan scan -i k8s
Scanning code remotely
Terrascan can be installed remotely to scan remote repositories or code resources using the -r and -u flags. Here’s an example:
$ terrascan scan -t aws -r git -u git@github.com:tenable/KaiMonkey.git//terraform/aws
Important: The URLs for the remote repositories should follow similar naming conventions as the source argument for modules in Terraform. For more details, see this article.
Scanning private Terraform module repositories
When scanning Terraform code, Terrascan checks for the environment variable TF_CLI_CONFIG_FILE. If found uses the credential file provided in that environment variable to authenticate a private terraform module registry. If the env variable is not found then checks for the availability of the file ~/.terraformrc. This file contains credential information to authenticate a private terraform module registry. If this file is present, Terrascan will attempt to use the credentials when authenticating the private repository. For more details on the format of this file, please see Terraform’s config file documentation.
Configuring the output format for a scan
By default, Terrascan output is displayed in a human friendly format. Use the -o flag to change this to YAML, JSON, XML, JUNIT-XML and SARIF formats.
Note: Terrascan will exit with an error code if any errors or violations are found during a scan.
List of possible Exit Codes
Scenario Exit Code scan summary has errors and violations 5 scan summary has errors but no violations 4 scan summary has violations but no errors 3 scan summary has no violations or errors 0 scan command errors out due to invalid inputs 1
Terrascan’s output is a list of security violations present in the scanned IaC files. The example below is terrascan’s output in YAML.
$ terrascan scan -t aws
results:
violations:
- rule_name: scanOnPushDisabled
description: Unscanned images may contain vulnerabilities
rule_id: AWS.ECR.DataSecurity.High.0578
severity: MEDIUM
category: Data Security
resource_name: scanOnPushDisabled
resource_type: aws_ecr_repository
file: ecr.tf
line: 1
count:
low: 0
medium: 1
high: 0
total: 1
Scanning a Helm Chart
Helm chart can be scanned by specifying “helm” on the -i flag as follows:
$ terrascan scan -i helm
This command will recursively look for Chart.yaml files in the current directory and scan rendered .yaml, .yml, .tpl template files found under the corresponding /templates directory.
A specific directory to scan can be specified using the -d flag. The Helm IaC provider does not support scanning of individual files using the -f flag.
Scanning a Kustomize Chart
A Kustomize chart can be scanned by specifying “kustomize” on the -i flag as follows:
$ terrascan scan -i kustomize
This command looks for a kustomization.yaml file in the current directory and scans rendered .yaml or .yml template files.
Terrascan considers Kustomize v4 as the default version. Other supported versions (v2 and v3) of Kustomize could be scanned by specifying –iac-version flag as follows:
$ terrascan scan -i kustomize --iac-version v2
Scanning v2 and v3 requires the corresponding Kustomize binary and the path to the binary must be specified in the KUSTOMIZE_<VERSION> ENV variable.
e.g: For –iac-version v2, we need to have:
KUSTOMIZE_V2=path/to/kustomize/v2/binary
To install Kustomize one can use this script
A specific directory to scan can be specified using the -d flag. The Kustomize IaC provider does not support scanning of individual files using the -f flag.
Scanning a Dockerfile
A Dockerfile can be scanned by specifying “docker” on the -i flag as follows:
$ terrascan scan -i docker
This command looks for a Dockerfile in the current directory and scans that file.
A specific directory to scan can be specified using the -d flag. With the -d flag, it will check for all the docker files (named as Dockerfile) in the provided directory recursively. A specific dockerfile can be scanned using -f flag by providing a path to the file.
Retrieve Container Image Vulnerabilities
Terrascan can display vulnerabilities for container images present in the IaC files being scanned by specifying the --find-vuln flag along with the scan command as follows:
$ terrascan scan -i <IaC Provider> --find-vuln
This command looks for container images referenced in the IaC files and retrieves any vulnerabilities as reported by its container registry.
Supported container registries: AWS Elastic Container Registry (ECR), Azure Container Registry, Google Container Registry, Google Artifact Registry, and Harbor Container Registry.
The following environment variables are required when connecting to the container registries:
AWS Elastic Container Registry (ECR)
ECR requires your environment to be configured similar to the requirements of AWS’s SDK. For example, the AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY, AWS_REGION environment variables can be set when connecting to AWS using API keys for an AWS user. More information here.
Google Container Registry and Artifact Registry
Terrascan requires a service account with access to the Container Analysis and Container Registry permissions. The GOOGLE_APPLICATION_CREDENTIALS environment variable can be set to the path of the service account’s key when scanning. More information about GCP authentication available here.
Azure Container Registry
When integrating vulnerability results from Azure, Terrascan requires the AZURE_AUTH_LOCATION, and AZURE_ACR_PASSWORD environment variables.
The AZURE_AUTH_LOCATION should contain the path to your azure authentication json. You can generate this as follows:
az ad sp create-for-rbac --sdk-auth > azure.auth
After generating the file, set the azure.auth file path as the AZURE_AUTH_LOCATION environment variable. More information about using file based authentication for the Azure SDK available here.
Terrascan also requires the password to the registry set into the AZURE_ACR_PASSWORD environment variable. This can be fetched using the az cli as follows:
az acr credential show --name RegistryName
Harbor Container Registry
When integrating vulnerability results from Harbor, Terrascan requires the HARBOR_REGISTRY_USERNAME, HARBOR_REGISTRY_PASSWORD,HARBOR_REGISTRY_CACERT, HARBOR_SKIP_TLS, and HARBOR_REGISTRY_DOMAIN environment variables.
The HARBOR_REGISTRY_DOMAIN environment variable helps Terrascan identify the registry’s domain.
The HARBOR_SKIP_TLS environment variable can be set to true to avoid TLS errors when Harbor is using a non-trusted TLS certificate. This is not recommended for production use.
Resource Config
While scanning a IaC, Terrascan loads all the IaC files, creates a list of resource configs and then processes this list to report violations. For debugging purposes, you can print this resource configs list as an output by using the --config-only flag to the terrascan scan command.
$ terrascan scan -i terraform -t aws -f elb.tf --config-only -o json
{
"aws_elb": [
{
"id": "aws_elb.public_elb",
"name": "public_elb",
"module_name": "root",
"source": "elb.tf",
"line": 1,
"type": "aws_elb",
"config": {
"connection_draining": true,
"health_check": [
{
"healthy_threshold": 2,
"interval": 15,
"target": "HTTP:80/index.html",
"timeout": 3,
"unhealthy_threshold": 2
}
],
"instances": "${aws_instance.web.*.id}",
"listener": [
{
"instance_port": 80,
"instance_protocol": "http",
"lb_port": 80,
"lb_protocol": "http"
}
],
"name": "${local.prefix.value}-public-elb",
"security_groups": [
"${aws_security_group.public_internet.id}"
],
"subnets": "${aws_subnet.public.*.id}",
"tags": {
"Name": "${local.prefix.value}-public-elb"
}
},
"line_config": {
"connection_draining": 16,
"health_check": [
{
"healthy_threshold": 9,
"interval": 13,
"target": 12,
"timeout": 11,
"unhealthy_threshold": 10
}
],
"instances": 6,
"listener": [
{
"instance_port": 18,
"instance_protocol": 19,
"lb_port": 20,
"lb_protocol": 21
}
],
"name": 2,
"security_groups": 5,
"subnets": 4,
"tags": {
"Name": 25
}
},
"skip_rules": null,
"max_severity": "",
"min_severity": ""
}
]
}
More details on scan command
List of options for scan command:
| Flag | Description | Options (default highlighted ) |
|---|---|---|
| -h | Help for scan command | See a list of all flags supported and descriptions. The default options for all commands are highlighted in bold |
| -d | Use this to scan a specific directory. Use “.” for current directory | AWS, GCP, Azure, and GitHub |
| -f | Use this command to scan a specific file | <tbd any formats/limitations for example file size> |
| -i type | Use this to change the IaC provider | arm, cft, docker, helm, k8s, kustomize, terraform |
| –iac-version version | Use this in conjunction with - i type to specify the version of IaC provider |
Supported versions of each IaC are: arm: v1, cft: v1, docker: v1, helm: v3, k8s: v1, kustomize: v2, v3, v4, terraform: v12, v13, v14, v15 |
| -p | Use this to specify directory path for policies | By default policies are installed here: |
| -t | Use this to specify individual cloud providers | all, aws, azure, gcp, github, k8s |
| -r | Use this to specify directory path for remote backend | git, s3, gcs, http |
| -u | Use this to specify directory URL for remote IaC repositories | see options below |
| scan-rules | Specify rules to scan, example: –scan-rules=“ruleID1,ruleID2” | |
| skip-rules | Specify one or more rules to skip while scanning. Example: –skip-rules=“ruleID1,ruleID2” | |
| use-colors | Configure the color for output (auto, t, f) | |
| –non-recursive | Use this for non recursive directories and modules scan | By default directory is scanned recursively, if this flag is used then only provided root directory will be scanned |
| –webhook-token string | Optional token used when sending authenticated requests to the notification webhook | This flag is optional when using the notification webhook |
| –webhook-url | A webhook URL where Terrascan will send JSON scan report and normalized IaC JSON | This overrides any notification webhook URLs configured in config TOML file specified with the -c flag |
| –use-terraform-cache | Use this to refer terraform remote modules from terraform init cache rather than downloading | By default remote module will be downloaded in temporary directory. If this flag is set then modules will be refered from terraform init cache if module is not present in terraform init cache it will be downloaded. Directory will be scanned non recurively if this flag is used.(applicable only with terraform IaC provider) |
| –find-vuln | find vulnerabilities | Use this to fetch vulnerabilities identified on the registry for docker images present in IaC the files scanned |
| –repo-url | repository url | This flag can be used to include the repository URL as part of scan results and notifications |
| –repo-ref | repository branch name | This flag can be used to include the repository branch name as part of scan results and notifications |
| -v | verbose | Displays violations with all details |
| Global flags | Description | Options |
|---|---|---|
| -c | Use this to specify config file settings | Format supported is *.TOML |
| -l | Use this to specify what log settings | debug, info, warn, error, panic, fatal |
| –log-output-dir | Use this to specify the directory path for writing the scan output to files along with console output. Using this flag will generate two files in the directory path provided, terrascan.log and scan-result.<ext>. The scan-result file extension will be in sync with -o flag (e.g. -o json will create scan-result.json). In case the directory could not be resolved, the scan logs and results will be printed on console only. |
|
| -x | Use this to specify the log file format | console, json |
| -o | Use this to specify the scan output type | human, json, yaml, xml, junit-xml, sarif, github-sarif |
| –temp-dir | Use this to specify temporary directory path to download remote repository,module and templates |
Full help for scan command:
$ terrascan scan -h
Terrascan
Detect compliance and security violations across Infrastructure as Code to mitigate risk before provisioning cloud native infrastructure.
Usage:
terrascan scan [flags]
Flags:
--categories strings list of categories of violations to be reported by terrascan (example: --categories="category1,category2")
--config-only will output resource config (should only be used for debugging purposes)
--find-vuln fetches vulnerabilities identified in Docker images
-h, --help help for scan
-d, --iac-dir string path to a directory containing one or more IaC files (default ".")
-f, --iac-file string path to a single IaC file
-i, --iac-type string iac type (arm, cft, docker, helm, k8s, kustomize, terraform, tfplan)
--iac-version string iac version (arm: v1, cft: v1, docker: v1, helm: v3, k8s: v1, kustomize: v2, v3, v4, terraform: v12, v13, v14, v15, tfplan: v1)
--non-recursive do not scan directories and modules recursively
--webhook-token string the auth token to call the notification webhook URL
--webhook-url string the URL where terrascan will send the scan report and normalized config json
-p, --policy-path stringArray policy path directory
-t, --policy-type strings policy type (all, aws, azure, docker, gcp, github, k8s) (default [all])
-r, --remote-type string type of remote backend (git, s3, gcs, http, terraform-registry)
-u, --remote-url string url pointing to remote IaC repository
--repo-ref string branch of the repo being scanned
--repo-url string URL of the repo being scanned, will be reflected in scan summary
--scan-rules strings one or more rules to scan (example: --scan-rules="ruleID1,ruleID2")
--severity string minimum severity level of the policy violations to be reported by terrascan
--show-passed display passed rules, along with violations
--skip-rules strings one or more rules to skip while scanning (example: --skip-rules="ruleID1,ruleID2")
--use-colors string color output (auto, t, f) (default "auto")
--use-terraform-cache use terraform init cache for remote modules (when used directory scan will be non recursive, flag applicable only with terraform IaC provider)
-v, --verbose will show violations with details (applicable for default output)
Global Flags:
-c, --config-path string config file path
-l, --log-level string log level (debug, info, warn, error, panic, fatal) (default "info")
--log-output-dir string directory path to write the log and output files
-x, --log-type string log output type (console, json) (default "console")
-o, --output string output type (human, json, yaml, xml, junit-xml, sarif, github-sarif) (default "human")
--temp-dir string temporary directory path to download remote repository,module and templates
2.2 - Server mode
Server mode will execute Terrascan’s API server. This is useful when using Terrascan to enforce a unified set of policies and configuration in multiple parts of the software development pipelines. It also simplifies programmatically interacting with Terrascan. By default the http server listens in port 9010 and supports the following routes:
Note: URL placeholders are equivalent to the command line flags in the scan command
API Routes
Check health of server
GET - /health
Scan IaC File
POST - /v1/{iac}/{iacVersion}/{cloud}/local/file/scan
POST Parameter: file - Content of the file to be scanned
Example:
curl -i -F "file=@aws_cloudfront_distribution.tf" localhost:9010/v1/terraform/v14/aws/local/file/scan
Scan Remote IaC
POST - /v1/{iac}/{iacVersion}/{cloud}/remote/dir/scan
Run Terrascan in Server Mode
You can launch server mode by executing the Terrascan binary, or with a Docker container. Use the following to execute the Terrascan CLI:
$ terrascan server
Use this command to launch Terrascan server mode using Docker:
$ docker run --rm --name terrascan -p 9010:9010 tenable/terrascan
Example of how to send a request to the Terrascan server using curl:
$ curl -i -F "file=@aws_cloudfront_distribution.tf" localhost:9010/v1/terraform/v14/aws/local/file/scan
HTTP/1.1 100 Continue
HTTP/1.1 200 OK
Date: Sun, 16 Aug 2020 02:45:35 GMT
Content-Type: text/plain; charset=utf-8
Transfer-Encoding: chunked
{
"results": {
"violations": [
{
"rule_name": "cloudfrontNoGeoRestriction",
"description": "Ensure that geo restriction is enabled for your Amazon CloudFront CDN distribution to whitelist or blacklist a country in order to allow or restrict users in specific locations from accessing web application content.",
"rule_id": "AWS.CloudFront.Network Security.Low.0568",
"severity": "LOW",
"category": "Network Security",
"resource_name": "s3-distribution-TLS-v1",
"resource_type": "aws_cloudfront_distribution",
"file": "terrascan-492583054.tf",
"line": 7
},
{
"rule_name": "cloudfrontNoHTTPSTraffic",
"description": "Use encrypted connection between CloudFront and origin server",
"rule_id": "AWS.CloudFront.EncryptionandKeyManagement.High.0407",
"severity": "HIGH",
"category": "Encryption and Key Management",
"resource_name": "s3-distribution-TLS-v1",
"resource_type": "aws_cloudfront_distribution",
"file": "terrascan-492583054.tf",
"line": 7
},
{
"rule_name": "cloudfrontNoHTTPSTraffic",
"description": "Use encrypted connection between CloudFront and origin server",
"rule_id": "AWS.CloudFront.EncryptionandKeyManagement.High.0407",
"severity": "HIGH",
"category": "Encryption and Key Management",
"resource_name": "s3-distribution-TLS-v1",
"resource_type": "aws_cloudfront_distribution",
"file": "terrascan-492583054.tf",
"line": 7
},
{
"rule_name": "cloudfrontNoLogging",
"description": "Ensure that your AWS Cloudfront distributions have the Logging feature enabled in order to track all viewer requests for the content delivered through the Content Delivery Network (CDN).",
"rule_id": "AWS.CloudFront.Logging.Medium.0567",
"severity": "MEDIUM",
"category": "Logging",
"resource_name": "s3-distribution-TLS-v1",
"resource_type": "aws_cloudfront_distribution",
"file": "terrascan-492583054.tf",
"line": 7
},
{
"rule_name": "cloudfrontNoSecureCiphers",
"description": "Secure ciphers are not used in CloudFront distribution",
"rule_id": "AWS.CloudFront.EncryptionandKeyManagement.High.0408",
"severity": "HIGH",
"category": "Encryption and Key Management",
"resource_name": "s3-distribution-TLS-v1",
"resource_type": "aws_cloudfront_distribution",
"file": "terrascan-492583054.tf",
"line": 7
}
],
"count": {
"low": 1,
"medium": 1,
"high": 3,
"total": 5
}
}
}
2.3 - In-file Instrumentation
Today, Terrascan supports these instrumentations:
- Rule Skipping
- Resource Prioritization
Rule Skipping
Rule skipping allows you to specify a rule that should not be applied to a particular resource.
Note: In-file instrumentation will skip the rule only for the resource it is defined in. The
skip_rulesparameter in the config file will skip the rule for the entire scan.
In Terraform
Use the syntax #ts:skip=RuleID optional_comment inside a resource to skip the rule for that resource.
Example
resource "aws_db_instance" "PtShGgAdi4" {
#ts:skip=AWS.RDS.DataSecurity.High.0414 Reason to skip this rule
allocated_storage = 20
storage_type = "gp2"
engine = "mysql"
engine_version = "5.7"
instance_class = "db.t2.micro"
.
.
.
}
In Kubernetes
Use the annotation
runterrascan.io/skip:[{\"rule\": \RuleID\", \"comment\": \"reason to skip the rule\"}] inside a resource to skip the rule for that resource.
Example
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: ingress-demo-disallowed
annotations:
runterrascan.io/skip: "[{\"rule\": \"AC-K8-NS-IN-H-0020\", \"comment\": \"reason to skip the rule\"}]"
spec:
rules:
- host: example-host.example.com
http:
paths:
- backend:
serviceName: nginx
servicePort: 80
In Dockerfile
Use the syntax #ts:skip=RuleID optional_comment inside the dockerfile to skip the rule for that resource.
Example
FROM runatlantis/atlantis:v0.16.1
#ts:skip=AC_DOCKER_0001 skip this rule.
ENV DEFAULT_TERRASCAN_VERSION=1.5.1
RUN terrascan init
ENTRYPOINT ["/bin/bash", "entrypoint.sh"]
CMD ["server"]
Resource Prioritization
Resource prioritization allows you set maximum and minimum severities for violations in a given resource. Are you configuring a very sensitive resource? Set the minimum severity to High, so low and medium violations will be escalated. Need to suppress all violations from a particular resource? Set the maximum severity to None.
For maximum severity, meaningful options are Medium, Low, and None.
For minimum severity, meaningful options are High and Medium.
In Terraform
Use the syntax #ts:maxseverity=SEVERITY, or #ts:minseverity=SEVERITY inside a resource to skip the rule for that resource.
Example
resource "aws_db_instance" "PtShGgAdi4" {
#ts:maxseverity=Low
allocated_storage = 20
storage_type = "gp2"
engine = "mysql"
engine_version = "5.7"
instance_class = "db.t2.micro"
.
.
.
}
In Kubernetes
Use the annotation
runterrascan.io/minseverity: SEVERITY, or runterrascan.io/maxseverity: SEVERITY inside a resource to skip the rule for that resource.
Example
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: ingress-demo-disallowed
annotations:
runterrascan.io/minseverity: Low
spec:
rules:
- host: example-host.example.com
http:
paths:
- backend:
serviceName: nginx
servicePort: 80
In Dockerfile
Use the syntax #ts:maxseverity=SEVERITY, or #ts:minseverity=SEVERITY inside a dockerfile to skip the rule for that resource.
Example
#ts:maxseverity=None
FROM runatlantis/atlantis:v0.16.1
ENV DEFAULT_TERRASCAN_VERSION=1.5.1
RUN terrascan init
ENTRYPOINT ["/bin/bash", "entrypoint.sh"]
CMD ["server"]
2.4 - Configuration File
You can provide a configuration file in TOML format to configure the Terrascan.
Command to specify config File
Use the -c or --config-path flag provide a TOML configuration file for Terrascan.
$ terrascan scan -c <config file path>
Here’s an example config file:
[notifications]
[notifications.webhook]
url = "https://httpbin.org/post"
token = "my_auth_token"
[severity]
level = "medium"
[rules]
skip-rules = [
"accurics.kubernetes.IAM.107"
]
[k8s-admission-control]
denied-categories = [
"Network Ports Security"
]
denied-severity = "high"
dashboard=true
[policy]
environment = "<environment_url>"
access_token = "<access_token>"
You can specify the following configurations:
- scan-rules - Specify one or more rules to scan. All other rules in the policy pack will be skipped.
- skip-rules - Specify one or more rules to skip while scanning. All other rules in the policy pack will be applied.
- severity - the minimal level of severity of the policies to be scanned and displayed. Options are high, medium and low
- category - the list of type of categories of the policies to be scanned and displayed
- notifications - This configuration can be used, as seen in the example above, to send the output of scans as a webhook to a remote server. Note that the
--notification-webhook-urlCLI flag will override any URLs configured through a configuration file.
k8s-admission-control - Config options for K8s Admission Controllers and GitOps workflows:
- denied-severity - Violations of this or higher severity will cause and admission rejection. Lower severity violations will be warnings. Options are high, medium. and low
- denied-categories - Violations from these policy categories will lead to an admission rejection. Policy violations of other categories will lead to warnings.
- dashboard=true - enable the
/logsendpoint to log and graphically display K8s admission requests and violations. Default isfalse
policy - Config options for policy source and destination path information
-
path - Sets the local path for terrascan files including policies
-
rego_subdir - Sub directory within the base path for caching policies
-
repo_url - Repository from which all the policies must be downloaded
-
branch - Specific branch out of the repository to pull the policies
-
environment - Authenticated environment URL for downloading policies. Supercedes any other source if its set along with a valid access token
-
access_token - Authentication token to download policies from authenticated environment
Logging
Logging can be configured by using the -l or --log-level flags with possible values being: debug, info, warn, error, panic, or fatal. This defaults to “info”.
In addition to the default “console” logs, the logs can be configured to be output in JSON by using the -x or --log-type flag with the value of json.
3 - Integrations
Terrascan can be integrated into many tools in the development pipeline. When integrated into a tool, vulnerability scanning is automated as part of the commit or build process. It can run on a developer’s laptop, a SCM (e.g. GitHub), and CI\CD servers (e.g. ArgoCD and Jenkins). It also has a built in Admission Controller for Kubernetes.
Please see the following guides for integrating Terrascan in different use cases. If the product you want to integrate with is not listed, do not fret. Terrascan supports many output formats (YAML, JSON, XML, JUNIT-XML and SARIF) to suit the variety of tools in the ecosystem. For example, it’s straightforward to integrate with Jenkins using the JUNIT-XML format.
Go to the Usage page for more details.
Community Guides and Blogs:
- Azure DevOps Credit to @lrgulliver (Liam Gulliver)
- Static Code Analyses - Terrascan, Terraform and Azure DevOps. Credit to James Cook
Our Integration Guides:
3.1 - Kubernetes Admission Controller
Overview
Terrascan can be integrated with K8s admissions webhooks. Admission controllers help you control resources created on a kubernetes cluster. By using Terrascan as an admission controller, resources violating security policies can be prevented from getting created in a Kubernetes cluster.
Note on SSL certificates: You can use valid SSL certificates or create self signed certificates and have your Kubernetes cluster trust it.
Installation Guide
To configure Terrascan as an admission controller, follow these steps:
- Create an instance of Terrascan which meets specified requirements as detailed below. Ensure Terrascan is accessible via HTTPS from the kubernetes API server.
- Create Terrascan config file.
- Run Terrascan in server mode.
- Configure a ValidatingWebhookConfiguration resource in kubernetes cluster pointing to the Terrascan server.
- Test your set up.
Step 1: Create an instance of Terrascan
Create an instance of Terrascan. To scan K8s configurations, your Terrascan instance must meet the following requirements.
- Make sure Terrascan is accessible via HTTPS. Ensure your cloud firewall is configured to allow this.
- Have a valid SSL certificate for the served domain name using one of the suggested methods below:
- Use a subdomain of your choice (e.g dev-terrascan-k8s.tenable.com) and create a valid certificate for this subdomain through your SSL certificate provider. You can use Let’s Encrypt which is a free, simple to use certificate authority.
- Use a reverse-proxy to serve SSL requests; for example, use Cloudflare Flexible to get a certificate by a trusted-CA to your self-signed certificate.
- Generate a self-signed certificate and configure your K8s cluster to trust it. To add a trusted CA to ca-pemstore, as demonstrated in paraspatidar’s blog post.
- Use the Terrascan docker as demonstrated in this document, or run it from the sources.
Step 2: Create a Terrascan config file
For instructions to create a config file, see Usage . You can create a config file that specifies which policies to use in the scan and which violations should be rejected during admission.
- Policies below the [severity] level will be ignored.
- Policies below the [k8s-admission-control] denied-severity will be logged and displayed by Terrascan, but will not lead to a rejected admission response to the k8s API server.
Sample config file
A config file example: config.toml
[severity]
level = "medium"
[rules]
skip-rules = [
"accurics.kubernetes.IAM.107"
]
[k8s-admission-control]
denied-categories = [
"Network Ports Security"
]
denied-severity = "high"
dashboard=true
You can specify the following configurations:
- scan-rules - one or more rules to scan
- skip-rules - one or more rules to skip while scanning
- severity - the minimal level of severity of the policies to be scanned and displayed. Options are high, medium and low
- category - the list of type of categories of the policies to be scanned and displayed
k8s-admission-control - Config options for K8s Admission Controllers and GitOps workflows:
- denied-severity - Violations of this or higher severity will cause and admission rejection. Lower severity violations will be warnings. Options are high, medium. and low
- denied-categories - violations from these policy categories will lead to an admission rejection. Policy violations of other categories will lead to warnings.
- dashboard=true - enable the
/logsendpoint to log and graphically display admission requests and violations. Default isfalse
Step 3: Run Terrascan in Server Mode
Run Terrascan docker image in your server using the following command:
sudo docker run -p 443:9443 -v <DATA_PATH>:/data -u root -e K8S_WEBHOOK_API_KEY=<API_KEY> tenable/terrascan server --cert-path /data/cert.pem --key-path /data/key.pem -c /data/config.toml
Where,
<API_KEY>is a key used for authentication between your K8s environment and the Terrascan server. Generate your preferred key and use it here.<DATA_PATH>is a directory path in your server where both the certificate and the private key .pem files are stored. This directory is also used to save the webhook logs. (Logs are in saves in SQLite file format)
Step 4: Configure a ValidatingWebhookConfiguration Resource in Kubernetes Cluster
Configure a new ValidatingWebhookConfiguration in your Kubernetes environment and specify your Terrascan server endpoint.
Example:
cat <<EOF | kubectl apply -f -
apiVersion: admissionregistration.k8s.io/v1
kind: ValidatingWebhookConfiguration
metadata:
name: my.validation.example.check
webhooks:
- name: my.validation.example.check
rules:
- apiGroups:
- ""
apiVersions:
- v1
operations:
- CREATE
- UPDATE
resources:
- pods
- services
failurePolicy: Fail
clientConfig:
url: https://<SERVER_ADDRESS>/v1/k8s/webhooks/<API_KEY>/scan
sideEffects: None
admissionReviewVersions: ["v1"]
EOF
- You can modify the
rulesthat trigger the webhook according to your preferences. - Update the
clientConfigURL with your terrascan server address and the API key you generated before.
Step 5: Test your settings
Try to run a new pod / service. For example:
kubectl run mynginx --image=nginx
Go to https://<SERVER_ADDRESS>/k8s/webhooks/<API_KEY>/logs and verify your request is logged.
3.2 - Argo CD
Terrascan can be integrated with Argo CD in two ways
- Use terrascan as a pre-sync hook to scan remote repositories
- Use terrascan’s k8s admission controller along with a pre-sync that scans a configured repository with the admission controller webhook
Method 1. Configure terrascan as a PreSync hook and scan the remote repository.
Configure a PreSync hook
The following example of a hook yaml is nearly ready to be added to an existing kubernetes configuration. To complete the configutation, you need to:
- Ensure that the secrets,
known_hosts, andssh_configvolume are relevant for your specific environment. - Specify a terrascan image.
You can also map a slack notification script to the container which will send notifications to your Slack webhook endpoint after the embedded script scans the repo.
apiVersion: batch/v1
kind: Job
metadata:
generateName: terrascan-hook-
annotations:
argocd.argoproj.io/hook: PreSync
spec:
ttlSecondsAfterFinished: 3600
template:
spec:
securityContext:
seccompProfile:
type: RuntimeDefault
volumes:
#add a configmap for the slack notification scripts
- name: notification-scripts
configMap:
name: slack-notifications
#add all required ssh keys need to clone your repos
- name: ssh-key-secret
secret:
secretName: ssh-key-secret
#add a secret for git config file
- name: ssh-config
secret:
secretName: ssh-config-secret
#add a configmap for the ssh known_hosts file
- name: ssh-known-hosts
configMap:
name: known-hosts-config
containers:
- name: terrascan-argocd
image: <terrscan-image>
resources:
requests:
cpu: "1"
memory: "256Mi"
limits:
cpu: "1"
memory: "256Mi"
command: ["/bin/sh", "-c"]
args:
- >
cp /etc/secret-volume/ssh-private-key /home/terrascan/.ssh/id_ed25519_github &&
cp /etc/ssh-config-secret/ssh-config /home/terrascan/.ssh/config &&
cp /etc/ssh-known-hosts-secret/ssh-known-hosts /home/terrascan/.ssh/known_hosts &&
chmod -R 400 /home/terrascan/.ssh/* &&
/go/bin/terrascan scan -r git -u <YOUR REPOSITORY PATH>-i k8s -t k8s | /data/notify_slack.sh webhook-tests argo-cd https://hooks.slack.com/services/TXXXXXXXX/XXXXXXXXXXX/0XXXXXXXXXXXXXXXXXX
securityContext:
seccompProfile:
type: RuntimeDefault
allowPrivilegeEscalation: false
runAsNonRoot: true
runAsUser: 101
livenessProbe:
exec:
command:
- /go/bin/terrascan
- version
periodSeconds: 10
initialDelaySeconds: 10
readinessProbe:
exec:
command:
- /go/bin/terrascan
- version
periodSeconds: 10
#if want to use private repo
volumeMounts:
- mountPath: /etc/secret-volume
name: ssh-key-secret
readOnly: true
- mountPath: /etc/ssh-config-secret
name: ssh-config
readOnly: true
- mountPath: /etc/ssh-known-hosts-secret
name: ssh-known-hosts
readOnly: true
- mountPath: /data
name: notification-scripts
readOnly: true
restartPolicy: Never
backoffLimit: 1
Note: As shown above, the PreSync requires access to the repository where IaC is stored, using the same branch (default) as the ArgoCD application pipeline.
To allow users to check for violations in the web interface, configure the job to delete after the specified time, using the parameter ttlSecondsAfterFinished. In addition, violation can be reported as webhook notifications, as shown below.
Example slack notification script
#!/bin/sh
function send_slack_notificaton {
channel=$1
username=$2
slack_hook=$3
curl -X POST --data-urlencode payload="{\"channel\": \"#${channel}\", \"username\": \"${username}\", \"text\": \" \`\`\` $(cat results.out) \`\`\` \", \"icon_emoji\": \":ghost:\"}" ${slack_hook}
}
if [ -p /dev/stdin ]; then
echo "processing terrascan results"
while IFS= read line; do
echo "${line}" | tr '\\"' ' ' >> results.out
done
cat results.out
send_slack_notificaton $1 $2 $3
echo "notification exit code: $?"
else
echo "no response skipping"
fi
For private repositories, the private following keys must be added as kubernetes secret:
private keyand sshconfigas Secretknown_hostsas ConfigMap
kubectl create secret generic ssh-key-secret \
--from-file=ssh-privatekey= < path to your private key > \
--from-file=ssh-publickey=< path to your public key >
Config-map:
kubectl create configmap ssh-known-hosts --from-file=< path to your known hosts file >
kubectl create configmap slack-notifications --from-file=< path to your notification script >
ssh config secret
kubectl create secret generic ssh-config-secret \
--from-file=< path to your ssh config file >
Example ssh config file
Host github.com
HostName github.com
IdentityFile ~/.ssh/id_ed25519_github
After configuring the presynchook yaml file, add the file to the relevant repository folder to configure Argo CD.
Method 2. Use PreSyncHook to trigger the Terrascan Server Service
You can use a pre-deployed terrascan server service in K8s cluster to scan the remote repository from Argo CD PreSync hook. To configure, follow these steps:
Step 1: Configure Terrascan Server webhook deployment yaml file with required keys and volumes and service to expose the controller pod.
apiVersion: apps/v1
kind: Deployment
metadata:
name: terrascan-server
labels:
app: terrascan
spec:
replicas: 1
selector:
matchLabels:
app: terrascan
template:
metadata:
labels:
app: terrascan
spec:
containers:
- name: terrascan
image: <TERRASCAN LATEST IMAGE>
resources:
limits:
memory: "256Mi"
cpu: "1"
ports:
- containerPort: 443
livenessProbe:
initialDelaySeconds: 30
periodSeconds: 10
timeoutSeconds: 5
httpGet:
path: /health
port: 443
scheme: HTTPS
env:
- name: K8S_WEBHOOK_API_KEY
value: yoursecretapikey
volumeMounts:
- mountPath: /data/certs
name: terrascan-certs-secret
readOnly: true
- mountPath: /data/config
name: terrascan-config
readOnly: true
- mountPath: /etc/secret-volume
name: ssh-key-secret
readOnly: true
- mountPath: /etc/ssh-config-secret
name: ssh-config
readOnly: true
- mountPath: /etc/ssh-known-hosts-secret
name: ssh-known-hosts
readOnly: true
command: ["/bin/sh", "-c"]
args:
- >
cp /etc/secret-volume/ssh-private-key /home/terrascan/.ssh/id_ed25519_github &&
cp /etc/ssh-config-secret/ssh-config /home/terrascan/.ssh/config &&
cp /etc/ssh-known-hosts-secret/ssh-known-hosts /home/terrascan/.ssh/known_hosts &&
chmod -R 400 /home/terrascan/.ssh/* &&
terrascan server --cert-path /data/certs/server.crt --key-path /data/certs/server.key -p 443 -l debug -c /data/config/config.toml
volumes:
#add all required ssh keys need to clone your repos
- name: ssh-key-secret
secret:
secretName: ssh-key-secret
#add a secret for git config file
- name: ssh-config
secret:
secretName: ssh-config-secret
#add a configmap for the ssh known_hosts file
- name: ssh-known-hosts
configMap:
name: known-hosts-config
#add a configmap for the terrascan config.toml file
- name: terrascan-config
configMap:
name: terrascan-config
#add a secret for the tls certificates
- name: terrascan-certs-secret
secret:
secretName: terrascan-certs-secret
Service example
apiVersion: v1
kind: Service
metadata:
name: terrascan-service
spec:
selector:
app: terrascan
ports:
- port: 443
targetPort: 443
For private repositories, the following private keys needs to be added as a kubernetes secret:
private keyand sshconfigas Secretknown_hostsas ConFigmap
kubectl create secret generic ssh-key-secret \
--from-file=ssh-privatekey= < path to your private key > \
--from-file=ssh-publickey=< path to your public key >
kubectl create secret generic terrascan-certs-secret \
--from-file= < path to your .key file > \
--from-file= < path to your .crt file >
Config-map:
kubectl create configmap ssh-known-hosts --from-file=< path to your known hosts file >
kubectl create configmap terrascan-config --from-file=<path to your config.toml file >
ssh config secret
kubectl create secret generic ssh-config-secret \
--from-file=< path to your ssh config file >
Example ssh config file
Host github.com
HostName github.com
IdentityFile ~/.ssh/id_ed25519_github
After making changes to the webhook deployment file, apply this yaml in your cluster.
You can also run terrascan admission controller server outside cluster, for more information and instructions on configuring terrascan as an admission controller webhook, see https://runterrascan.io/docs/integrations/k8s/.
Step 2: Create a Dockerfile
Create a Dockerfile for the container. This container will run the script that triggers the remote Terrascan API server. The template for the script is below, after the Dockerfile. Please fill the values in the template to match your environment.
# Dockerfile with a script to use terrascan's validating webhook
# configured in the kubernetes cluster, to scan a repo for violations
FROM alpine:3.12.0
#curl to send request to terrascan validating webhook
RUN apk add --no-cache curl
WORKDIR /home/terrascan
RUN mkdir bin
COPY scripts/argocd-terrascan-remote-scan.sh bin/terrascan-remote-scan.sh
# create non root user
RUN addgroup --gid 101 terrascan && \
adduser -S --uid 101 --ingroup terrascan terrascan && \
chown -R terrascan:terrascan bin && \
chmod u+x bin/terrascan-remote-scan.sh
USER 101
CMD ["sh"]
The terrascan-remote-scan script
#!/bin/sh
set -o errexit
TERRASCAN_SERVER="https://${SERVICE_NAME}"
IAC=${IAC_TYPE:-"k8s"}
IAC_VERSION=${IAC_VERSION:-"v1"}
CLOUD_PROVIDER=${CLOUD_PROVIDER:-"all"}
REMOTE_TYPE=${REMOTE_TYPE:-"git"}
if [ -z ${SERVICE_NAME} ]; then
echo "Service Name Not set"
exit 6
fi
if [ -z ${REMOTE_URL} ]; then
echo "Remote URL Not set"
exit 6
fi
SCAN_URL="${TERRASCAN_SERVER}/v1/${IAC}/${IAC_VERSION}/${CLOUD_PROVIDER}/remote/dir/scan"
echo "Connecting to the service: ${SERVICE_NAME} to scan the remote url: ${REMOTE_URL} \
with configurations { IAC type: ${IAC}, IAC version: ${IAC_VERSION}, remote type: ${REMOTE_TYPE} , cloud provider: ${CLOUD_PROVIDER}}"
RESPONSE=$(curl -s -w \\n%{http_code} --location -k --request POST "$SCAN_URL" \
--header 'Content-Type: application/json' \
--data-raw '{
"remote_type":"'${REMOTE_TYPE}'",
"remote_url":"'${REMOTE_URL}'"
}')
echo "$RESPONSE"
HTTP_STATUS=$(printf '%s\n' "$RESPONSE" | tail -n1)
if [ "$HTTP_STATUS" -eq 403 ]; then
exit 3
elif [ "$HTTP_STATUS" -eq 200 ]; then
exit 0
else
exit 1
fi
Step 3: Configure PreSync hook to use container created in step 2
The following example hook yaml is mostly ready to be added to an existing kubernetes configuration.
apiVersion: batch/v1
kind: Job
metadata:
generateName: terrascan-hook-
namespace: <YOUR APP NAMESPACE>
annotations:
argocd.argoproj.io/hook: PreSync
spec:
ttlSecondsAfterFinished: 3600
template:
spec:
securityContext:
seccompProfile:
type: RuntimeDefault
containers:
- name: terrascan-argocd
image: <IMAGE FROM STEP TWO>
resources:
requests:
cpu: "1"
memory: "256Mi"
limits:
cpu: "1"
memory: "256Mi"
env:
- name: SERVICE_NAME
value: <Name of service exposed for terrascan controller pod>
- name: REMOTE_URL
value: <YOUR PRIVATE REPOSITORY PATH>
- name: IAC_TYPE
value: <IAC TYPE YOU WANT SCAN> # If not provided default value is 'k8s'
- name: IAC_VERSION
value: <VERSION OF IAC TYPE SELECTED> # If not provided default value is 'v1'
- name: CLOUD_PROVIDER
value: <TYPE OF CLOUD PROVIDER> #If not provided default value is 'all'
- name: REMOTE_TYPE
value: <TYPE OF REMOTE> #If not provided default value is 'git'
args:
- sh
- /home/terrascan/bin/terrascan-remote-scan.sh
securityContext:
seccompProfile:
type: RuntimeDefault
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
runAsUser: 101
livenessProbe:
exec:
command:
- cat
- /home/terrascan/bin/terrascan-remote-scan.sh
periodSeconds: 10
initialDelaySeconds: 10
readinessProbe:
exec:
command:
- cat
- /home/terrascan/bin/terrascan-remote-scan.sh
periodSeconds: 10
initialDelaySeconds: 10
restartPolicy: Never
backoffLimit: 1
To allow users to check for violations in the web interface, configure the job to delete after the specified time, using the parameter ttlSecondsAfterFinished. In addition, violation can be reported as webhook notifications, as shown in Method 1.
After configuring the presynchook yaml file, add the file to the relevant repository folder to configure Argo CD.
Note: All the example yaml configuration files present in documentation are tested with k8s 1.19.7 version.
3.3 - Atlantis PR Automation
You can integrate Terrascan into an Atlantis setup using one of the two ways:
- Method 1: Atlantis Workflow-based integration which sends scan requests to an independently running terraform server
- Method 2: Custom Atlantis container image which has an integrated Terrascan
In either scenario, the configuration of Atlantis varies from installation to installation. For instructions to install, configure, and use Atlantis, see the Atlantis documentation.
Method 1: Workflow-based integration
In this method, you can modify or create a custom workflow for Atlantis so your repositories will be scanned by Terrascan as part of the pull request automation.
Requirements
The following requirements must be met before starting the integration workflow:
- The atlantis server must have TCP connectivity to where the terrascan server is running.
- The
curlcommand must be installed on the system so theterrascan-remote-scan.shscript can make the scan request. Atlantis’s docker image has curl preinstalled.
Integration steps for Workflow based integration
- Modify Workflow
- Configure the Script
- Run Atlantis
Modify Workflow
- Modify your workflow to call
terrascan-remote-scan.shduring the plan stage. - See the ‘plan’ detailed below:
- the first three
run: terraformcommands are the default for an atlantis workflow.
Note: The values for the variables
$WORKSPACEand$PLANFILEreferenced in the second and third run commands in the yaml below are automatically provided by atlantis
- The fourth
run terrascan-remote-scan.shinitiates the Terrascan scan request.
Note: By default, the
terrascan-remote-scan.shscript can be found under thescriptsdirectory in this project; copy this to a location where it can be executed by the Atlantis server. If theterrascan-remote-scan.shscript is not in the directory where the Atlantis server command is being run to, you will have to specify the path to the script in the fourth run command.
repos:
- id: /.*/
workflow: terrascan
workflows:
terrascan:
plan:
steps:
- run: terraform init -input=false -no-color
- run: terraform workspace select -no-color $WORKSPACE
- run: terraform plan -input=false -refresh -no-color --out $PLANFILE
- run: terrascan-remote-scan.sh
Script configuration
Modify the terrascan-remote-scan.sh script according your environment. The script is located here. Open the script with your any editor of your choice and review the following six settings which is found at the top of the file:
TERRASCAN_SERVER=192.168.1.55
TERRASCAN_PORT=9010
IGNORE_LOW_SEVERITY=false
IAC=terraform
IAC_VERSION=v14
CLOUD_PROVIDER=aws
Descriptions of these settings are as follows:
TERRASCAN_SERVERis the hostname or IP address of the host running the terrascan server. This will be used by the script to submit the scan request.TERRASCAN_PORTis the TCP port which Terrascan server is listening on. By default, this is9010.IGNORE_LOW_SERVERITYallows you to specify the scan response for low-severity findings in the code. During a scan if theterrascan-remote-scan.shshould fail a build if a low-severity finding is found. Some users will want to set this totrueso they may ignore low-severity findings.IAC,IAC_VERSION, andCLOUD_PROVIDERare terrascan options. Descriptions and valid values can be found by runningterrascan scan -h.
Running atlantis
Run Atlantis with the terrascan-workflow.yaml as a server-side repo configuration. The command for this depends on how you choose to deploy Atlantis.
If running the Atlantis binary directly, use the following command:
$ atlantis server \
--atlantis-url="$URL" \
--gh-user="$USERNAME" \
--gh-token="$TOKEN" \
--gh-webhook-secret="$SECRET" \
--repo-allowlist="$REPO_ALLOWLIST" \
--repo-config=terrascan-workflow.yaml
Note: The variables in the example above must be configured separately using
exportor similar shell methods.
Important: Before the first pull request is processed, run Terrascan in server mode using the following command:
terrascan server
Automated scanning and results
When the systems are running, if Atlantis is initiated either via a pull request, or via a comment of atlantis plan, Terrascan will be also be invoked as part of the atlantis plan flow. Scan results are reported as part of the pull request as comments, this notifies the reviewers before approving a requests. If any issues are found the test will be marked as failed.
Method 2: Custom Atlantis Container
Terrascan offers a custom container built on top of the official Atlantis container image, which allows users to run IaC scans with Terrascan, in addition to the usual atlantis usage. There’s a built-in atlantis workflow configured inside the
container which is ready to be used.
The default workflow.yaml file used is the atlantis/workflow.yaml in the Terrascan repo.
Alternatively, you can also override that default workflow using the --repo-config flag.
Steps to use the custom Atlantis container
In code repository, usage is exactly the same as atlantis, add a comment atlantis plan and atlantis plan to your Pull Requests to trigger the custom atlantis-terrascan workflow.
To use the default built-in container image:
docker pull tenable/terrascan_atlantis
To build your own container image:
docker build ./integrations/atlantis -t <image_name>
Run the container:
docker run \
--env-file=<.env-file> \
-p 4141:4141 \
-v <pwd>/config_data/:/etc/terrascan/ \
tenable/terrascan_atlantis server \
--gh-user="$USERNAME" --gh-token="$TOKEN" --gh-webhook-secret="$SECRET" \
--repo-allowlist="$REPO_ALLOWLIST" \
-c /etc/terrascan/config.toml
The syntax of the Atlantis server command here is same as in atlantis docs, except for an optional -c flag which can be used to specify the file path for the toml config to be used by Terrascan. Another way to provide the toml config filepath would be the TERRASCAN_CONFIG environment variable. You need to provide all the environment variables that terraform requires to operate with your respective cloud providers.
Note: As a good practice, Terrascan recommends use of a specific tag of the container image rather than the latest tag.
Running a scan
With everything configured, a local Terrascan scan will be triggered as part of the Atlantis plan workflow.
3.4 - GitHub and GitLab
GitHub Action
The Terrascan GitHub Action can be used as part of GitHub workflows to scan your repository for IaC issues as part of code pushes or pull requests.
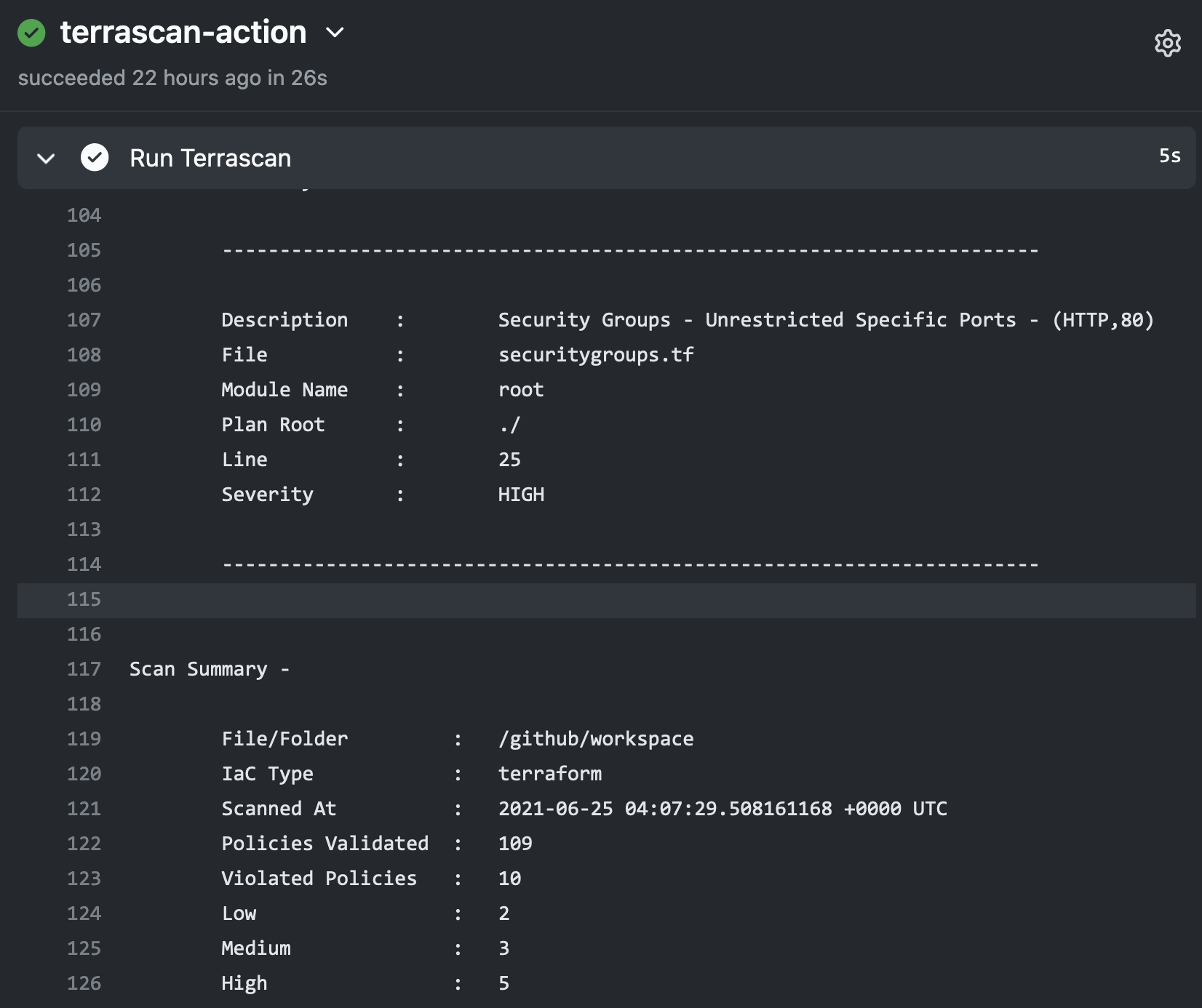
Using Terrascan’s SARIF output, the action can include issues found during the scan within GitHub’s code scanning results for the repository.
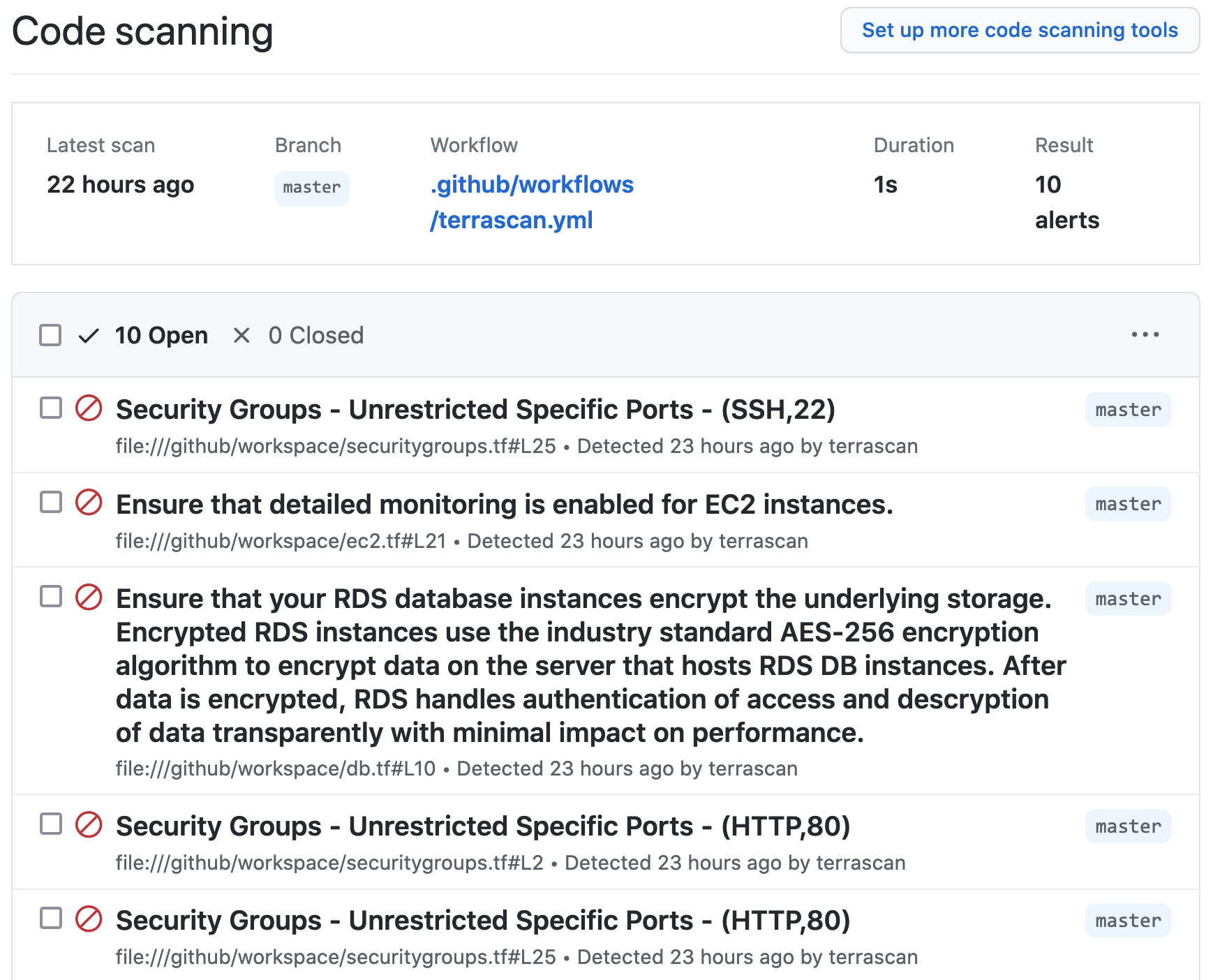
Below is an example workflow configuration where the action is configured to scan a repository including Terraform v14+ HCL files for AWS resources and the SARIF output of the scan is uploaded to GitHub code scanning.
on: [push]
jobs:
terrascan_job:
runs-on: ubuntu-latest
name: terrascan-action
steps:
- name: Checkout repository
uses: actions/checkout@v2
- name: Run Terrascan
id: terrascan
uses: tenable/terrascan-action@main
with:
iac_type: 'terraform'
iac_version: 'v14'
policy_type: 'aws'
only_warn: true
sarif_upload: true
#non_recursive:
#iac_dir:
#policy_path:
#skip_rules:
#config_path:
- name: Upload SARIF file
uses: github/codeql-action/upload-sarif@v1
with:
sarif_file: terrascan.sarif
A detailed explanation of the action’s input variables is available in the terrascan-action repository.
GitLab CI
GitLab CI can use Docker images as part of a pipeline. We can take advantage of this functionality and use Terrascan’s docker image as part of your pipeline to scan infrastructure as code.
To do this you can update your .gitlab-ci.yml file to use the “accurics/terrascan:latest” image with the [“bin/sh”, “-c”] entrypoint. Terrascan can be found on “/go/bin” in the image and you can use any Terrascan command line options according to your needs. Here’s an example .gitlab-ci.yml file:
stages:
- scan
terrascan:
image:
name: tenable/terrascan:latest
entrypoint: ["/bin/sh", "-c"]
stage: scan
script:
- /go/bin/terrascan scan .
Argo CD Application PreSync Hooks
Terrascan can be configured as an Argo CD job during the application sync process using resource hooks. The PreSync resource hook is the best way to evaluate the kubernetes deployment configuration and report any violations.
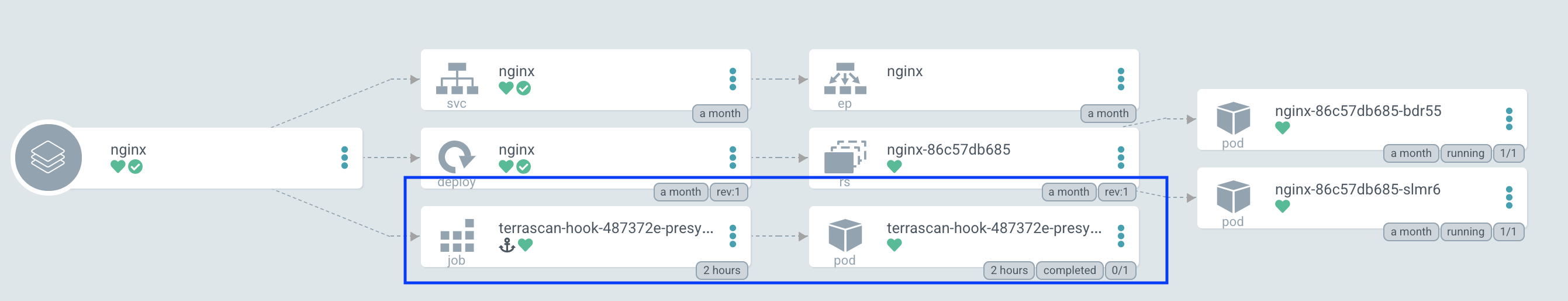
Adding the Terrascan job consists of two steps:
- Creating a container which runs Terrascan
- Configuring a PreSync hook which uses that container
We’ll address the PreSync hook first.
Step 1: Configure PreSync resource hook
The following example hooks yaml is mostly ready to be added to an existing kubernetes configuration. Just make sure the secrets volume is relevant, specify your new Terrascan container image, and make sure the embedded script scans your repo and sends notifications to your Slack webhook endpoint.
apiVersion: batch/v1
kind: Job
metadata:
generateName: terrascan-hook-
annotations:
argocd.argoproj.io/hook: PreSync
spec:
ttlSecondsAfterFinished: 3600
template:
spec:
volumes:
- name: secret-volume
secret:
secretName: ssh-key-secret
containers:
- name: terrascan-argocd
image: "<your container namespace>/<your container build from step #2 below>:<hash>"
command: ["/bin/ash", "-c"]
args:
- >
cp /etc/secret-volume/ssh-privatekey /home/terrascan/.ssh/id_rsa &&
chmod 400 /home/terrascan/.ssh/id_rsa &&
/go/bin/terrascan scan -r git -u <git URL to scan> -i k8s -t k8s | /home/terrascan/bin/notify_slack.sh webhook-tests argo-cd https://hooks.slack.com/services/TXXXXXXXX/XXXXXXXXXXX/0XXXXXXXXXXXXXXXXXX
volumeMounts:
- name: secret-volume
readOnly: true
mountPath: "/etc/secret-volume"
restartPolicy: Never
backoffLimit: 1
As shown, the PreSync requires access to the repository where IaC is stored, using the same branch (default) as the Argo CD application pipeline.
For non-public repositories, the private key needs to be added as a kubernetes secret.
kubectl create secret generic ssh-key-secret \
--from-file=ssh-privatekey=/path/to/.ssh/id_rsa \
--from-file=ssh-publickey=/path/to/.ssh/id_rsa.pub
Configuring the job to delete only after the specified time see ttlSecondsAfterFinished will allow users to check for violations in the User Interface, the alternative is through notifications.
Step 2: Create Terrascan container
The container which runs Terrascan can be built using the following files: known_hosts, notify_slack.sh, Dockerfile.
known_hosts
The known_hosts file ensures that the container will be able to clone your project’s git repository in order to scan it. Hashes for the most common public repository hosts are included here, and you may add hashes for any private hosts which you need to access in order to clone your project.
# known_hosts
github.com,192.30.255.113 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAq2A7hRGmdnm9tUDbO9IDSwBK6TbQa+PXYPCPy6rbTrTtw7PHkccKrpp0yVhp5HdEIcKr6pLlVDBfOLX9QUsyCOV0wzfjIJNlGEYsdlLJizHhbn2mUjvSAHQqZETYP81eFzLQNnPHt4EVVUh7VfDESU84KezmD5QlWpXLmvU31/yMf+Se8xhHTvKSCZIFImWwoG6mbUoWf9nzpIoaSjB+weqqUUmpaaasXVal72J+UX2B+2RPW3RcT0eOzQgqlJL3RKrTJvdsjE3JEAvGq3lGHSZXy28G3skua2SmVi/w4yCE6gbODqnTWlg7+wC604ydGXA8VJiS5ap43JXiUFFAaQ==
bitbucket.org,104.192.141.1 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAubiN81eDcafrgMeLzaFPsw2kNvEcqTKl/VqLat/MaB33pZy0y3rJZtnqwR2qOOvbwKZYKiEO1O6VqNEBxKvJJelCq0dTXWT5pbO2gDXC6h6QDXCaHo6pOHGPUy+YBaGQRGuSusMEASYiWunYN0vCAI8QaXnWMXNMdFP3jHAJH0eDsoiGnLPBlBp4TNm6rYI74nMzgz3B9IikW4WVK+dc8KZJZWYjAuORU3jc1c/NPskD2ASinf8v3xnfXeukU0sJ5N6m5E8VLjObPEO+mN2t/FZTMZLiFqPWc/ALSqnMnnhwrNi2rbfg/rd/IpL8Le3pSBne8+seeFVBoGqzHM9yXw==
gitlab.com,172.65.251.78 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFSMqzJeV9rUzU4kWitGjeR4PWSa29SPqJ1fVkhtj3Hw9xjLVXVYrU9QlYWrOLXBpQ6KWjbjTDTdDkoohFzgbEY=
notify_slack.sh
The notify_slack.sh script is used to send a Slack notification after the scan completes. This example expects the channel name, username, and webhook URL to be passed as command line arguments from the PreSync hook which invokes this container. You may modify this script if you wish to send notifications in a different way.
#!/bin/ash
# notify_slack.sh
function send_slack_notificaton {
channel=$1
username=$2
slack_hook=$3
curl -X POST --data-urlencode payload="{\"channel\": \"#${channel}\", \"username\": \"${username}\", \"text\": \" \`\`\` $(cat results.out) \`\`\` \", \"icon_emoji\": \":ghost:\"}" ${slack_hook}
}
if [ -p /dev/stdin ]; then
echo "processing terrascan results"
while IFS= read line; do
echo "${line}" | tr '\\"' ' ' >> results.out
done
cat results.out
send_slack_notificaton $1 $2 $3
echo "notification exit code: $?"
else
echo "no response skipping"
fi
Dockerfile
The Dockerfile is, of course, used to build the container. In this case, we start with the official Terrascan image and we add in the above files to ensure we can access the repository and send notifications.
# Dockerfile
FROM tenable/terrascan:929e377
ENTRYPOINT []
USER root
RUN apk add --no-cache openssh curl
WORKDIR /home/terrascan
RUN mkdir -p .ssh && mkdir -p bin
COPY known_hosts .ssh
COPY notify_slack.sh bin/
RUN chown -R terrascan:terrascan .ssh && \
chown -R terrascan:terrascan bin && \
chmod 400 .ssh/known_hosts && \
chmod u+x bin/notify_slack.sh
USER terrascan
CMD ["ash"]
Once you’ve built the image and pushed to your container registry, you can add the PreSync hook which will automatically run Terrascan during the application sync process.
3.5 - Pre-commit hook
Integrating Terrascan with Pre-commit
Overview
Terrascan scan can be used as a pre-commit hook in order to automatically scan your IaC before every commit. For more information about pre-commit hooks see https://pre-commit.com/#intro
Requirements
- Ensure Terrascan is properly installed (See https://runterrascan.io/docs/getting-started/#installing-terrascan)
- Have Pre-commit package manager installed (See https://pre-commit.com/#install)
Integration Method
Add config file
- Add file called .pre-commit-config.yaml to root of repo you wish to scan with pre-commit. It should look like this:
repos:
- repo: https://github.com/tenable/terrascan
rev: <COMMIT/VERSION>
hooks:
- id: terraform-pre-commit
args: [ '-i <IAC PROVIDER>'] #optional
Note: The optional args line allows you to specify the IaC provider. For example,
repos:
- repo: https://github.com/tenable/terrascan
rev: <COMMIT/VERSION>
hooks:
- id: terraform-pre-commit
args: [ '-i k8s']
will cause
'terrascan scan -i k8s'
to run and thus scan kubernetes yaml files. You may exclude the args like so:
repos:
- repo: https://github.com/tenable/terrascan
rev: <COMMIT/VERSION>
hooks:
- id: terraform-pre-commit
which causes the default
'terrascan scan'
to be run, scanning all IaC provider types.
Once you have everything installed, and add the appropriate config file to your repo,
'terrascan scan -i <IAC PROVIDER>'
everytime you attempt to commit your staged changes. You can also call the hook directly on all files using pre-commit run –all-files
4 - Architecture
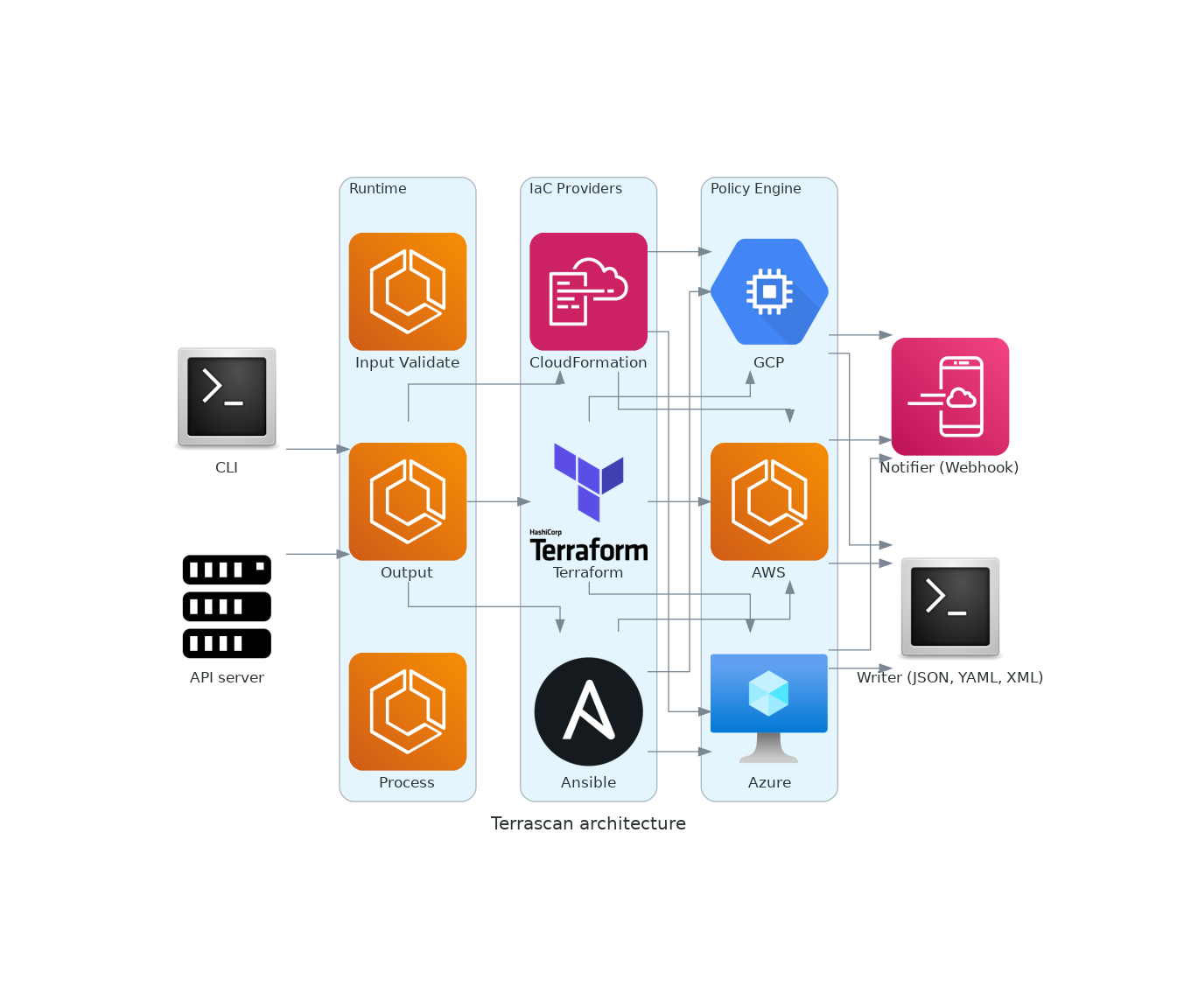
Terrascan’s architecture is built to be modular to facilitate adding IaC languages and policies. At a high level Terrascan is composed of the following architectural components: a command line interface, API server, runtime, pluggable IaC providers, pluggable policy engine, notifier, and writer.
- Command Line Interface = Provides CLI input to Terrascan.
- API Server = Provides input to Terrascan through an API.
- Runtime = Performs input validation and process inputs
- IaC Providers = Converts IaC language into normalized JSON
- Policy Engine = Applies policies against normalized JSON
- Notifier = Provides webhooks for results of Terrascan scans.
- Writer = Writes results into various formats like JSON, YAML, or XML.
5 - Policies
5.1 - Policy Overview
Terrascan policies are written using the Rego policy language. With each rego policy, a JSON “rule” file is included which defines metadata for the policy. Policies included within Terrascan are stored in the pkg/policies/opa/rego directory.
Updating Terrascan with the latest policies
The first time using Terrascan, if the -p flag is not specified, Terrascan will download the latest policies from the Terrascan repository. You can update your local environment to the latest policies published in the repository by running terrascan init.
Ignoring Policies on a scan
Terrascan keeps a copy of policies on your local filesystem on the ~/.terrascan/pkg/policies/opa/rego directory. You can also specify a particular directory with rego policies to scan by using the -p flag. Terrascan allows you to ignore policies from scans by using the –skip-rules flag or using in-file instrumentation to skip policies on a particular resource.
Adding policies
For each policy, there are 2 files required by Terrascan, a rule .json file with metadata for the policy and a .rego rego file for the policy itself.
Writing an OPA rego policy file
The input for the rego policies is the normalized input from the IaC provider. When writing policies you can obtain this as a normalized .json by using the --config-only flag of the scan command in combination with -o json. Let’s use this Terraform HCL file for example:
resource "github_repository" "example" {
name = "example"
description = "My awesome codebase"
private = false
template {
owner = "github"
repository = "terraform-module-template"
}
}
Here’s the output of the --config-only flag.
$ terrascan scan -i terraform --config-only -o json
{
"github_repository": [
{
"id": "github_repository.example",
"name": "example",
"source": "main.tf",
"line": 1,
"type": "github_repository",
"config": {
"description": "My awesome codebase",
"name": "example",
"private": false,
"template": [
{
"owner": "github",
"repository": "terraform-module-template"
}
]
}
}
]
}
You can use this .json output as the input in the rego playgound. The following policy can be used on the above Terraform to flag if the GitHub repository has been created with private = false.
package accurics
privateRepoEnabled[api.id] {
api := input.github_repository[_]
not api.config.private == true
not api.config.visibility == "private"
}
A successful policy will trigger the following output:
{
"privateRepoEnabled": [
"github_repository.example"
]
}
The Rule JSON file
The rule files follow this naming convention: AC_<policy_type>_<next_available_rule_number>.json where <policy_type> is the upper case of any supported policy types by terrascan. The supported policy types can be fetched from Terrascan’s help menu: terrascan scan -h | grep "policy-type".
Note: The previous naming convention was:
<cloud-provider>.<resource-type>.<rule-category>.<severity>.<next-available-rule-number>.json. This has been deprecated.
Here’s an example of the contents of a rule file:
{
"name": "unrestrictedIngressAccess",
"file": "unrestrictedIngressAccess.rego",
"policy_type": "aws",
"resource_type": "aws_db_security_group",
"template_args": {
"name": "unrestrictedIngressAccess",
"prefix": "",
"suffix": ""
},
"severity": "HIGH",
"description": "It is recommended that no security group allows unrestricted ingress access",
"category": "NETWORK_SECURITY",
"version": 1,
"id": "AC_AWS_0001"
}
| Key | Value |
|---|---|
| name | Short name for the rule |
| file | Filename of the Rego policy |
| policy_type | Type of cloud provider used by this rule (e.g. aws, azure, docker, gcp, github, k8s, etc.) |
| resource_type | IaC resource applicable to the policy |
| template_args | Used for making rego policies unique |
| severity | Likelihood * impact of issue |
| description | Description of the issue found with this rule |
| ruleReferenceId (deprecated) | This field was used in previous versions of Terrascan, but has been replaced by id. |
| category | Descriptive category for this rule |
| version | Version number for the rule/rego |
5.2 - AWS Policies
aws_iam_role_policy
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | json | HIGH | It is recommended and considered a standard security advice to grant least privileges that is, granting only the permissions required to perform a task. IAM policies are the means by which privileges are granted to users, groups, or roles. Determine what users need to do and then craft policies for them that let the users perform only those tasks, instead of granting full administrative privileges. | AC-AW-IA-H-1189 |
| Identity and Access Management | AIRP | HIGH | Ensure IAM roles do not have any policies attached that may cause privilege escalation. | AWS.AIRP.IAM.HIGH.0051 |
aws_route53_record
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | Route53HostedZone | HIGH | Route53HostedZone should have recordSets. | AWS.Route53HostedZone.DNSManagement.High.0422 |
aws_elasticsearch_domain_policy
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | AEDP | HIGH | Ensure Elasticsearch domains do not have wildcard policies. | AWS.AEDP.IAM.HIGH.0060 |
aws_lb_target_group
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | ALTG | MEDIUM | Ensure Target Group use HTTPs to ensure end to end encryption | AWS.ALTG.IS.MEDIUM.0042 |
aws_api_gateway_method_settings
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | API Gateway | MEDIUM | Enable Detailed CloudWatch Metrics for APIs | AWS.APIGateway.Logging.Medium.0569 |
aws_workspaces_workspace
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | AWW | MEDIUM | Ensure user volume for Workspaces is Encrypted | AWS.AWW.DP.MEDIUM.041 |
| Data Protection | AWW | MEDIUM | Ensure root volume for Workspaces is Encrypted | AWS.AWW.DP.MEDIUM.040 |
aws_vpc
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Security Best Practices | VPC | MEDIUM | Avoid creating resources in default VPC | AWS.VPC.Logging.Medium.0471 |
| Logging and Monitoring | VPC | LOW | Ensure VPC flow logging is enabled in all VPCs | AWS.VPC.Logging.Medium.0470 |
aws_iam_account_password_policy
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Compliance Validation | Iam | LOW | Lower case alphabet not present in the Password, Password Complexity is not high. Increased Password complexity increases resiliency against brute force attack | AWS.Iam.IAM.Medium.0454 |
| Compliance Validation | Iam | MEDIUM | Setting a lengthy password increases account resiliency against brute force login attempts | AWS.Iam.IAM.Medium.0458 |
| Compliance Validation | Iam | LOW | It is recommended that the password policy prevent the reuse of passwords.Preventing password reuse increases account resiliency against brute force login attempts | AWS.Iam.IAM.Low.0539 |
| Compliance Validation | Iam | MEDIUM | Number not present in the Password, Password Complexity is not high. Increased Password complexity increases resiliency against brute force attack | AWS.Iam.IAM.Medium.0455 |
| Compliance Validation | Iam | MEDIUM | Setting a lengthy password increases account resiliency against brute force login attempts | AWS.Iam.IAM.Medium.0495 |
| Compliance Validation | Iam | MEDIUM | Special symbols not present in the Password, Password Complexity is not high. Increased Password complexity increases resiliency against brute force attack | AWS.Iam.IAM.Medium.0456 |
| Compliance Validation | Iam | MEDIUM | Upper case alphabet not present in the Password, Password Complexity is not high. Increased Password complexity increases resiliency against brute force attack | AWS.Iam.IAM.Medium.0457 |
| Compliance Validation | Iam | LOW | Reducing the password lifetime increases account resiliency against brute force login attempts | AWS.Iam.IAM.Low.0540 |
aws_mq_broker
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Security Best Practices | ElasticSearch | MEDIUM | Publicly Accessible MQ Brokers | AWS.ElasticSearch.NetworkSecurity.Medium.0887 |
| Logging and Monitoring | ElasticSearch | LOW | Enable AWS MQ Log Exports | AWS.ElasticSearch.Logging.Medium.0885 |
aws_db_instance
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | RDS | HIGH | Ensure Certificate used in RDS instance is updated | AWS.RDS.DS.High.1042 |
| Logging and Monitoring | ADI | MEDIUM | Ensure AWS RDS instances have logging enabled. | AWS.ADI.LM.MEDIUM.0076 |
| Data Protection | RDS | MEDIUM | Ensure that your RDS database has IAM Authentication enabled. | AWS.RDS.DataSecurity.High.0577 |
| Infrastructure Security | RDS | HIGH | RDS Instance publicly_accessible flag is true | AWS.RDS.NS.High.0101 |
| Data Protection | RDS | HIGH | RDS Instance Auto Minor Version Upgrade flag disabled | AWS.RDS.DS.High.1041 |
| Data Protection | RDS | HIGH | Ensure that your RDS database instances encrypt the underlying storage. Encrypted RDS instances use the industry standard AES-256 encryption algorithm to encrypt data on the server that hosts RDS DB instances. After data is encrypted, RDS handles authentication of access and descryption of data transparently with minimal impact on performance. | AWS.RDS.DataSecurity.High.0414 |
aws_secretsmanager_secret_policy
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | ASSP | HIGH | Ensure secrets manager do not wildcard policies attached | AWS.ASSP.IAM.HIGH.0066 |
aws_ebs_volume
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | EcsCluster | HIGH | Ensure that AWS EBS clusters are encrypted. Data encryption at rest, prevents unauthorized users from accessing sensitive data on your AWS EBS clusters and associated cache storage systems. | AWS.EcsCluster.EncryptionandKeyManagement.High.0413 |
| Data Protection | EBS | HIGH | Enable AWS EBS Snapshot Encryption | AWS.EBS.EKM.Medium.0682 |
aws_api_gateway_rest_api
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | APIGateway | MEDIUM | Enable Content Encoding | AWS.APIGateway.Medium.0568 |
| Infrastructure Security | APIGateway | MEDIUM | API Gateway Private Endpoints | AWS.APIGateway.NetworkSecurity.Medium.0570 |
aws_iam_role
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | json | HIGH | It is recommended and considered a standard security advice to grant least privileges that is, granting only the permissions required to perform a task. IAM policies are the means by which privileges are granted to users, groups, or roles. Determine what users need to do and then craft policies for them that let the users perform only those tasks, instead of granting full administrative privileges. | AC-AW-IA-H-1188 |
aws_iam_user_policy_attachment
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | AIUPA | MEDIUM | Ensure IAM permissions are not given directly to users | AWS.AIUPA.IAM.MEDIUM.0050 |
aws_ebs_encryption_by_default
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | EBS | HIGH | Ensure that the AWS EBS that hold sensitive and critical data is encrypted by default to fulfill compliance requirements for data-at-rest encryption. | AWS.EBS.DataSecurity.High.0580 |
aws_sns_topic
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Compliance Validation | SNS | HIGH | Ensure SNS Topic is Publicly Accessible For Subscription | AWS.SNS.NS.Medium.1044 |
| Data Protection | AST | MEDIUM | Ensure SNS topic is Encrypted using KMS master key | AWS.AST.DP.MEDIUM.0037 |
aws_apigatewayv2_api
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Security Best Practices | ApiGatewayV2Api | Medium | Insecure Cross-Origin Resource Sharing Configuration allowing all domains | AWS.ApiGatewayV2Api.AccessControl.0630 |
aws_efs_file_system
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | EFS | HIGH | Enable encryption of your EFS file systems in order to protect your data and metadata from breaches or unauthorized access and fulfill compliance requirements for data-at-rest encryption within your organization. | AWS.EFS.EncryptionandKeyManagement.High.0409 |
| Data Protection | EFS | HIGH | Enable encryption of your EFS file systems in order to protect your data and metadata from breaches or unauthorized access and fulfill compliance requirements for data-at-rest encryption within your organization. | AWS.EFS.EncryptionandKeyManagement.High.0410 |
aws_lb_listener
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | ALL | MEDIUM | Ensure there is a listener configured on HTTPs or with a port 443 | AWS.ALL.IS.MEDIUM.0046 |
aws_sqs_queue
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Security Best Practices | SQS | HIGH | Identify any publicly accessible SQS queues available in your AWS account and update their permissions in order to protect against unauthorized users. | AWS.SQS.NetworkSecurity.High.0569 |
| Security Best Practices | SQS | HIGH | Ensure that your Amazon Simple Queue Service (SQS) queues are protecting the contents of their messages using Server-Side Encryption (SSE). The SQS service uses an AWS KMS Customer Master Key (CMK) to generate data keys required for the encryption/decryption process of SQS messages. There is no additional charge for using SQS Server-Side Encryption, however, there is a charge for using AWS KMS | AWS.SQS.NetworkSecurity.High.0570 |
aws_docdb_cluster
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | ADC | MEDIUM | Ensure DocDb is encrypted at rest | AWS.ADC.DP.MEDIUM.0022 |
| Logging and Monitoring | ADC | MEDIUM | Ensure DocDb clusters have log exports enabled. | AWS.ADC.LM.MEDIUM.0069 |
aws_cloudwatch_log_group
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | ACLG | MEDIUM | Ensure AWS Cloudwatch log group has retention policy set. | AWS.ACLG.LM.MEDIUM.0068 |
aws_instance
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | json | MEDIUM | EC2 instances should disable IMDS or require IMDSv2 as this can be related to the weaponization phase of kill chain | AC-AWS-NS-IN-M-1172 |
| Identity and Access Management | json | HIGH | Ensure that instance launched follows the least privilege principle as this can be related to delivery-exploitation-Installation phases of kill chain | AC-AW-IA-LC-H-0442 |
| Logging and Monitoring | AI | HIGH | Ensure that detailed monitoring is enabled for EC2 instances. | AWS.AI.LM.HIGH.0070 |
| Infrastructure Security | json | HIGH | Security group attached to launch configuration is wide open to internet and this can be related to reconnaissance phase | AC-AW-IS-LC-H-0443 |
| Infrastructure Security | json | MEDIUM | Ensure that your AWS application is not deployed within the default Virtual Private Cloud in order to follow security best practices | AC-AW-IS-IN-M-0144 |
aws_config
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | Config | MEDIUM | Ensure AWS Config Rule is enabled for Encrypted Volumes | AWS.Config.EncryptionandKeyManagement.Medium.0660 |
aws_cloudformation_stack
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Security Best Practices | CloudFormation | MEDIUM | AWS CloudFormation Not In Use | AWS.CloudFormation.Medium.0599 |
| Security Best Practices | CloudFormation | MEDIUM | AWS CloudFormation Stack Policy | AWS.CloudFormation.Medium.0604 |
| Security Best Practices | CloudFormation | MEDIUM | Enable AWS CloudFormation Stack Termination Protection | AWS.CloudFormation.Medium.0605 |
| Security Best Practices | CloudFormation | MEDIUM | Enable AWS CloudFormation Stack Notifications | AWS.CloudFormation.Medium.0603 |
aws_iam_user_policy
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Compliance Validation | IamUser | HIGH | Ensure Hardware MFA device is enabled for the “root” account | AWS.IamUser.IAM.High.0387 |
| Identity and Access Management | json | HIGH | It is recommended and considered a standard security advice to grant least privileges that is, granting only the permissions required to perform a task. IAM policies are the means by which privileges are granted to users, groups, or roles. Determine what users need to do and then craft policies for them that let the users perform only those tasks, instead of granting full administrative privileges. | AC-AW-IA-H-1190 |
| Identity and Access Management | AIUP | MEDIUM | Ensure IAM policies are attached only to groups or roles | AWS.AIUP.IAM.MEDIUM.0049 |
| Compliance Validation | IamUser | HIGH | Ensure Virtual MFA device is enabled for the “root” account | AWS.IamUser.IAM.High.0388 |
| Compliance Validation | IamUser | HIGH | It is recommended that MFA be enabled for all accounts that have a console password. Enabling MFA provides increased security for console access as it requires the authenticating principal to possess a device that emits a time-sensitive key and have knowledge of a credential | AWS.IamUser.IAM.High.0389 |
aws_ecs_task_definition
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | EcsCluster | HIGH | Like any other EC2 instance it is recommended to place ECS instance within a VPC. AWS VPCs provides the controls to facilitate a formal process for approving and testing all network connections and changes to the firewall and router configurations | AWS.EcsCluster.NetworkSecurity.High.0104 |
| Infrastructure Security | AETD | MEDIUM | Ensure EFS volume used for ECS task defination has in transit encryption enabled | AWS.AETD.IS.MEDIUM.0043 |
| Data Protection | LaunchConfiguration | HIGH | Sensitive Information Disclosure | AWS.LaunchConfiguration.DataSecurity.High.0101 |
aws_ecr_repository_policy
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | ECR | HIGH | Identify any exposed Amazon ECR image repositories available within your AWS account and update their permissions in order to protect against unauthorized access. Amazon Elastic Container Registry (ECR) is a managed Docker registry service that makes it easy for DevOps teams to store, manage and deploy Docker container images. An ECR repository is a collection of Docker images available on AWS cloud. | AWS.ECR.DataSecurity.High.0579 |
aws_iam_policy
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | json | HIGH | It is recommended and considered a standard security advice to grant least privileges that is, granting only the permissions required to perform a task. IAM policies are the means by which privileges are granted to users, groups, or roles. Determine what users need to do and then craft policies for them that let the users perform only those tasks, instead of granting full administrative privileges. | AC-AW-IA-H-1187 |
aws_dynamodb_table
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Resilience | DynamoDb | MEDIUM | Ensure Point In Time Recovery is enabled for DynamoDB Tables | AWS.DynamoDb.Logging.Medium.007 |
| Data Protection | ADT | MEDIUM | Ensure DynamoDb is encrypted at rest | AWS.ADT.DP.MEDIUM.0025 |
aws_apigatewayv2_stage
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | ApiGatewayV2Stage | Low | AWS API Gateway V2 Stage is missing access logs | AWS.ApiGatewayV2Stage.Logging.0630 |
aws_ecr_repository
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | AER | MEDIUM | Ensure ECR repository is encrypted at rest | AWS.AER.DP.MEDIUM.0026 |
| Configuration and Vulnerability Analysis | ECR | MEDIUM | Unscanned images may contain vulnerabilities | AWS.ECR.DataSecurity.High.0578 |
| Identity and Access Management | AER | MEDIUM | Ensure ECR repository has policy attached. | AWS.AER.DP.MEDIUM.0058 |
aws_cloudfront_distribution
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | CloudFront | HIGH | Secure ciphers are not used in CloudFront distribution | AWS.CloudFront.EncryptionandKeyManagement.High.0408 |
| Infrastructure Security | json | LOW | Ensure that geo restriction is enabled for your Amazon CloudFront CDN distribution to whitelist or blacklist a country in order to allow or restrict users in specific locations from accessing web application content. | AC-AW-IS-CD-M-0026 |
| Infrastructure Security | json | Medium | Ensure that cloud-front has web application firewall enabled | AC-AW-IS-CD-M-1186 |
| Data Protection | CloudFront | HIGH | Use encrypted connection between CloudFront and origin server | AWS.CloudFront.EncryptionandKeyManagement.High.0407 |
| Logging and Monitoring | CloudFront | MEDIUM | Ensure that your AWS Cloudfront distributions have the Logging feature enabled in order to track all viewer requests for the content delivered through the Content Delivery Network (CDN). | AWS.CloudFront.Logging.Medium.0567 |
aws_cloudwatch
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | CloudWatch | MEDIUM | App-Tier CloudWatch Log Group Retention Period | AWS.CloudWatch.Logging.Medium.0631 |
| Data Protection | CloudWatch | HIGH | AWS CloudWatch log group is not encrypted with a KMS CMK | AWS.CloudWatch.EncryptionandKeyManagement.High.0632 |
aws_ami_launch_permission
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | AMI | MEDIUM | Limit access to AWS AMIs | AWS.AMI.NS.Medium.1040 |
aws_launch_configuration
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | EcsCluster | HIGH | Ensure that AWS ECS clusters are encrypted. Data encryption at rest, prevents unauthorized users from accessing sensitive data on your AWS ECS clusters and associated cache storage systems. | AWS.EcsCluster.EncryptionandKeyManagement.High.0413 |
| Identity and Access Management | json | HIGH | Ensure that launch configuration launched follows the least privilege principle | AC-AW-IA-LC-H-0441 |
| Data Protection | LaunchConfiguration | HIGH | Avoid using base64 encoded private keys as part of config | AWS.LaunchConfiguration.DataSecurity.High.0102 |
| Data Protection | LaunchConfiguration | HIGH | Avoid using base64 encoded shell script as part of config | AWS.LaunchConfiguration.DataSecurity.High.0101 |
| Logging and Monitoring | json | Medium | It is important to enable cloudWatch monitoring incase monitoring the activity | AC-AW-LM-LC-M-0440 |
| Configuration and Vulnerability Analysis | json | HIGH | Launch configuration uses IMDSv1 which vulnerable to SSRF | AC-AW-CA-LC-H-0439 |
| Infrastructure Security | json | HIGH | Security group attached to launch configuration is wide open to internet | AC-AW-IS-LC-H-0438 |
aws_athena_database
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | ADB | MEDIUM | Ensure Athena Database is encrypted at rest | AWS.ADB.DP.MEDIUM.016 |
aws_api_gateway_stage
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | API Gateway | MEDIUM | Enable SSL Client Certificate | AWS.APIGateway.NetworkSecurity.Medium.0565 |
| Logging and Monitoring | API Gateway | MEDIUM | Ensure that AWS CloudWatch logs are enabled for all your APIs created with Amazon API Gateway service in order to track and analyze execution behavior at the API stage level. | AWS.APIGateway.Logging.Medium.0572 |
| Logging and Monitoring | API Gateway | LOW | Ensure AWS API Gateway has active xray tracing enabled | AWS.APIGateway.Logging.Medium.0571 |
| Logging and Monitoring | API Gateway | MEDIUM | Enable AWS CloudWatch Logs for APIs | AWS.APIGateway.Logging.Medium.0567 |
aws_elasticsearch_domain
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | ElasticSearch | HIGH | Enable AWS ElasticSearch Encryption At Rest | AWS.ElasticSearch.EKM.Medium.0778 |
| Infrastructure Security | ElasticSearch | MEDIUM | Ensure Elasticsearch domains being created are set to be encrypted node-to-node | AWS.ElasticSearch.IS.MEDIUM.0045 |
| Data Protection | ElasticSearch | MEDIUM | ElasticSearch Domain Encrypted with KMS CMKs | AWS.ElasticSearch.EKM.Medium.0768 |
| Compliance Validation | Elasticsearch | MEDIUM | Ensure that your AWS Elasticsearch clusters have enabled the support for publishing slow logs to AWS CloudWatch Logs. This feature enables you to publish slow logs from the indexing and search operations performed on your ES clusters and gain full insight into the performance of these operations. | AWS.Elasticsearch.Logging.Medium.0573 |
aws_iam_user_login_profile
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Compliance Validation | Iam | HIGH | Password policies are, in part, used to enforce password complexity requirements. IAM password policies can be used to ensure password are comprised of different character sets, have minimal length, rotation and history restrictions | AWS.Iam.IAM.High.0391 |
aws_iam_group_policy
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | json | HIGH | It is recommended and considered a standard security advice to grant least privileges that is, granting only the permissions required to perform a task. IAM policies are the means by which privileges are granted to users, groups, or roles. Determine what users need to do and then craft policies for them that let the users perform only those tasks, instead of granting full administrative privileges. | AC-AW-IA-H-0392 |
aws_load_balancer_policy
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | ELB | HIGH | Using insecure ciphers for your ELB Predefined or Custom Security Policy, could make the SSL connection between the client and the load balancer vulnerable to exploits. TLS 1.0 was recommended to be disabled by PCI Council after June 30, 2016 | AWS.ELB.EncryptionandKeyManagement.High.0401 |
| Infrastructure Security | ELB | HIGH | Remove insecure ciphers for your ELB Predefined or Custom Security Policy, to reduce the risk of the SSL connection between the client and the load balancer being exploited. | AWS.ELB.EncryptionandKeyManagement.High.0403 |
aws_s3_bucket
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | S3Bucket | HIGH | Misconfigured S3 buckets can leak private information to the entire internet or allow unauthorized data tampering / deletion | AWS.S3Bucket.IAM.High.0377 |
| Identity and Access Management | S3Bucket | HIGH | Ensure S3 buckets do not have, a both public ACL on the bucket and a public access block. | AWS.S3Bucket.IAM.HIGH.0065 |
| Logging and Monitoring | S3Bucket | MEDIUM | Ensure S3 buckets have access logging enabled. | AWS.S3Bucket.LM.MEDIUM.0078 |
| Infrastructure Security | S3Bucket | LOW | Ensure that there are not any static websites being hosted on buckets you aren’t aware of | AWS.S3Bucket.NetworkSecurity.High.0417 |
| Resilience | S3Bucket | HIGH | Enabling S3 versioning will enable easy recovery from both unintended user actions, like deletes and overwrites | AWS.S3Bucket.IAM.High.0370 |
| Identity and Access Management | S3Bucket | HIGH | S3 bucket Access is allowed to all AWS Account Users. | AWS.S3Bucket.DS.High.1043 |
| Identity and Access Management | S3Bucket | HIGH | Misconfigured S3 buckets can leak private information to the entire internet or allow unauthorized data tampering / deletion | AWS.S3Bucket.IAM.High.0379 |
| Data Protection | S3Bucket | HIGH | Ensure that S3 Buckets have server side encryption at rest enabled with KMS key to protect sensitive data. | AWS.S3Bucket.EncryptionandKeyManagement.High.0405 |
| Identity and Access Management | S3Bucket | HIGH | Misconfigured S3 buckets can leak private information to the entire internet or allow unauthorized data tampering / deletion | AWS.S3Bucket.IAM.High.0378 |
| Identity and Access Management | S3Bucket | HIGH | Misconfigured S3 buckets can leak private information to the entire internet or allow unauthorized data tampering / deletion | AWS.S3Bucket.IAM.High.0381 |
aws_eks_cluster
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | AEC | MEDIUM | Ensure EKS clusters have control plane logging enabled. | AWS.AEC.LM.MEDIUM.0071 |
aws_elb
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | ELB | MEDIUM | Ensure AWS ELB has access logging enabled. | AWS.ELB.LM.MEDIUM.0072 |
| Infrastructure Security | ELB | LOW | AWS ELB incoming traffic not encrypted | AWS.ELB.NetworkPortsSecurity.Low.0563 |
aws_redshift_cluster
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | Redshift | HIGH | Ensure Redshift clusters are not publicly accessible to minimize security risks. | AWS.Redshift.NetworkSecurity.HIGH.0564 |
| Logging and Monitoring | Redshift | LOW | Ensure AWS Redshift cluster instances have logging enabled. | AWS.Redshift.Logging.Medium.0565 |
| Data Protection | Redshift | MEDIUM | Use customer-managed KMS keys instead of AWS-managed keys, to have granular control over encrypting and encrypting data. Encrypt Redshift clusters with a Customer-managed KMS key. This is a recommended best practice. | AWS.Redshift.EncryptionandKeyManagement.High.0415 |
aws_elasticcache_replication_group
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | AERG | MEDIUM | Ensure Elastic Cache Replication Group is encrypted at rest | AWS.AERG.DP.MEDIUM.0027 |
| Data Protection | AERG | MEDIUM | Ensure Elastic Cache Replication Group is encrypted in transit | AWS.AERG.DP.MEDIUM.0044 |
aws_kinesis_stream
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | Kinesis | HIGH | Ensure Kinesis Stream is encrypted | AWS.Kinesis.EncryptionandKeyManagement.High.0412 |
aws_config_configuration_aggregator
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | Config | HIGH | Ensure AWS Config is enabled in all regions | AWS.Config.Logging.HIGH.0590 |
aws_s3_bucket_object
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | ASBO | MEDIUM | Ensure S3 object is Encrypted | AWS.ASBO.DP.MEDIUM.0034 |
aws_route53_query_log
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | Route53 query logs | MEDIUM | Ensure CloudWatch logging is enabled for Route53 hosted zones. | AWS.Route53querylogs.Logging.Medium.0574 |
aws_secretsmanager_secret
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | SecretsManagerSecret | MEDIUM | Ensure SecretsManager Secrets are Encrypted using KMS key | AWS.SecretsManagerSecret.DP.MEDIUM.0036 |
aws_iam_access_key
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | IamUser | HIGH | The root account is the most privileged user in an AWS account. AWS Access Keys provide programmatic access to a given AWS account. It is recommended that all access keys associated with the root account be removed. Removing access keys associated with the root account limits vectors by which the account can be compromised. Additionally, removing the root access keys encourages the creation and use of role based accounts that are least privileged. | AWS.IamUser.IAM.High.0390 |
| Identity and Access Management | IamUser | MEDIUM | Ensure that there are no exposed Amazon IAM access keys in order to protect your AWS resources against unapproved access | AWS.IamUser.IAM.High.0391 |
aws_neptune_cluster
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | ANC | MEDIUM | Ensure Neptune Cluster is Encrypted | AWS.ANC.DP.MEDIUM.0030 |
| Logging and Monitoring | ANC | MEDIUM | Ensure AWS Neptune clusters have logging enabled. | AWS.ANC.LM.MEDIUM.0075 |
aws_dax_cluster
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | ADC | MEDIUM | Ensure server-side encryption is enabled for AWS DAX Cluster | AWS.ADC.DP.MEDIUM.0021 |
aws_guardduty_detector
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | GuardDuty Enabled | MEDIUM | Ensure that Amazon GuardDuty service is currently enabled in all regions in order to protect your AWS environment and infrastructure (AWS accounts and resources, IAM credentials, guest operating systems, applications, etc) against security threats. AWS GuardDuty is a managed threat detection service that continuously monitors your VPC flow logs, AWS CloudTrail event logs and DNS logs for malicious or unauthorized behavior. The service monitors for activity such as unusual API calls, potentially compromised EC2 instances or potentially unauthorized deployments that indicate a possible AWS account compromise. AWS GuardDuty operates entirely on Amazon Web Services infrastructure and does not affect the performance or reliability of your applications. The service does not require any software agents, sensors or network appliances. | AWS.GuardDutyEnabled.Security.Medium.0575 |
aws_db_security_group
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | RDS | HIGH | RDS should not be defined with public interface. Firewall and router configurations should be used to restrict connections between untrusted networks and any system components in the cloud environment. | AWS.RDS.NetworkSecurity.High.0101 |
| Infrastructure Security | RDS | HIGH | RDS should not be open to a large scope. Firewall and router configurations should be used to restrict connections between untrusted networks and any system components in the cloud environment. | AWS.RDS.NetworkSecurity.High.0103 |
| Infrastructure Security | RDS | HIGH | RDS should not be open to a public scope. Firewall and router configurations should be used to restrict connections between untrusted networks and any system components in the cloud environment. | AWS.RDS.NetworkSecurity.High.0102 |
aws_s3_bucket_policy
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | S3Bucket | HIGH | Misconfigured S3 buckets can leak private information to the entire internet or allow unauthorized data tampering / deletion | AWS.S3Bucket.IAM.High.0371 |
| Identity and Access Management | IamPolicy | HIGH | Misconfigured S3 buckets can leak private information to the entire internet or allow unauthorized data tampering / deletion | AWS.IamPolicy.IAM.High.0376 |
| Identity and Access Management | IamPolicy | HIGH | Misconfigured S3 buckets can leak private information to the entire internet or allow unauthorized data tampering / deletion | AWS.IamPolicy.IAM.High.0375 |
| Identity and Access Management | IamPolicy | HIGH | Misconfigured S3 buckets can leak private information to the entire internet or allow unauthorized data tampering / deletion | AWS.IamPolicy.IAM.High.0374 |
| Identity and Access Management | S3Bucket | HIGH | Misconfigured S3 buckets can leak private information to the entire internet or allow unauthorized data tampering / deletion | AWS.S3Bucket.IAM.High.0372 |
| Identity and Access Management | IamPolicy | HIGH | Misconfigured S3 buckets can leak private information to the entire internet or allow unauthorized data tampering / deletion | AWS.IamPolicy.IAM.High.0373 |
aws_ami
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | EC2 | MEDIUM | Enable AWS AMI Encryption | AWS.EC2.EncryptionandKeyManagement.Medium.0688 |
aws_elasticache_cluster
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Compliance Validation | ElastiCache | HIGH | ElastiCache for Redis version is not compliant with AWS PCI DSS requirements | AWS.ElastiCache.DataSecurity.High.0425 |
| Compliance Validation | ElastiCache | HIGH | ElastiCache for Memcached is not in use in AWS PCI DSS environments | AWS.ElastiCache.DataSecurity.High.0424 |
| Resilience | ElastiCache | MEDIUM | AWS ElastiCache Multi-AZ | AWS.ElastiCache.HighAvailability.Medium.0757 |
aws_kinesis_firehose_delivery_stream
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | Kinesis | HIGH | AWS Kinesis Server data at rest has server side encryption (SSE) | AWS.Kinesis.EncryptionandKeyManagement.High.0411 |
aws_rds_cluster
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Resilience | RDS | MEDIUM | Ensure backup retention period is set for rds cluster | AWS.RDS.RE.MEDIUM.0013 |
| Data Protection | RDS | HIGH | Encrypt Amazon RDS instances and snapshots at rest, by enabling the encryption option for your Amazon RDS DB instance | AWS.RDS.EncryptionandKeyManagement.High.0414 |
aws_cloudtrail
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | CloudTrail | HIGH | Ensure CloudTrail logs are encrypted using KMS | AWS.CloudTrail.Logging.High.0399 |
| Logging and Monitoring | CloudTrail | MEDIUM | Cloud Trail Multi Region not enabled | AWS.CloudTrail.Logging.Medium.004 |
| Security Best Practices | CloudTrail | MEDIUM | Ensure that EC2 is EBS optimized | AWS.CloudTrail.Logging.Medium.008 |
| Security Best Practices | CloudTrail | LOW | ECR should have an image tag be immutable | AWS.CloudTrail.Logging.Low.009 |
| Logging and Monitoring | CloudTrail | MEDIUM | Cloud Trail Multi Region not enabled | AWS.CloudTrail.Logging.Medium.0460 |
| Logging and Monitoring | CloudTrail | MEDIUM | Ensure CloudTrail has log file validation enabled. | AWS.CloudTrail.LM.MEDIUM.0087 |
| Logging and Monitoring | CloudTrail | MEDIUM | Ensure appropriate subscribers to each SNS topic | AWS.CloudTrail.Logging.Low.0559 |
| Logging and Monitoring | Config | Medium | Ensure AWS Config is enabled in all regions | AWS.Config.Logging.Medium.0590 |
aws_sagemaker_notebook_instance
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | ASNI | MEDIUM | Ensure SageMaker Instance is Encrypted | AWS.ASNI.DP.MEDIUM.0035 |
aws_lambda_function
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | LambdaFunction | MEDIUM | Ensure AWS Lambda function has policy attached. | AWS.LambdaFunction.LM.MEIDUM.0063 |
| Infrastructure Security | LambdaFunction | Low | Lambda function doesn’t not include a VPC configuration. | AWS.LambdaFunction.Logging.0472 |
| Logging and Monitoring | LambdaFunction | LOW | Lambda tracing is not enabled. | AWS.LambdaFunction.Logging.0470 |
| Data Protection | LambdaFunction | High | Lambda does not use KMS CMK key to protect environment variables. | AWS.LambdaFunction.EncryptionandKeyManagement.0471 |
| Logging and Monitoring | LambdaFunction | LOW | Lambda tracing is not enabled. | AWS.LambdaFunction.Logging.0470 |
aws_kms_key
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | AKK | HIGH | Ensure IAM policies do not have ‘Principal’ element missing from the policy statement. | AWS.AKK.IAM.HIGH.0012 |
| Identity and Access Management | KMS | HIGH | Identify any publicly accessible AWS Key Management Service master keys and update their access policy in order to stop any unsigned requests made to these resources. | AWS.KMS.NetworkSecurity.High.0566 |
| Data Protection | AKK | HIGH | Ensure rotation for customer created CMKs is enabled | AWS.AKK.DP.HIGH.0012 |
| Identity and Access Management | AKK | HIGH | Ensure KMS key policy does not have wildcard policies attached. | AWS.AKK.IAM.HIGH.0082 |
aws_security_group
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | json | MEDIUM | Ensure Memcached SSL (UDP,11214) is not accessible by a public CIDR block range | AC_AWS_0292 |
| Infrastructure Security | json | LOW | Ensure Cassandra' (TCP,7001) is not exposed to private hosts more than 32 | AC_AWS_0338 |
| Infrastructure Security | json | MEDIUM | Ensure Known internal web port (TCP,8080) is not accessible by a CIDR block range | AC_AWS_0284 |
| Infrastructure Security | json | MEDIUM | Ensure Oracle DB SSL (TCP,2484) is not accessible by a public CIDR block range | AC_AWS_0302 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - MSSQL Server (TCP,1433) | AC_AWS_0247 |
| Infrastructure Security | json | LOW | Ensure SNMP' (UDP,161) is not exposed to private hosts more than 32 | AC_AWS_0355 |
| Infrastructure Security | json | LOW | Ensure NetBIOSNameService' (TCP,137) is not exposed to private hosts more than 32 | AC_AWS_0343 |
| Infrastructure Security | json | HIGH | Ensure SMTP (TCP,25) is not accessible by a public CIDR block range | AC_AWS_0314 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Memcached SSL (UDP,11215) | AC_AWS_0251 |
| Infrastructure Security | json | LOW | Ensure Elasticsearch' (TCP,9300) is not exposed to private hosts more than 32 | AC_AWS_0363 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Telnet (TCP,23) | AC_AWS_0271 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports MemcachedSSL (UDP,11214) is not exposed to private hosts more than 32 | AC_AWS_0334 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - SQL Server Analysis Service browser (TCP,2382) | AC_AWS_0267 |
| Infrastructure Security | json | MEDIUM | Ensure MSSQL Debugger (TCP,135) is not accessible by a public CIDR block range | AC_AWS_0288 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports https (TCP,443) is not exposed to private hosts more than 32 | AC_AWS_0322 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - remote desktop port (TCP,3389) | AC_AWS_0230 |
| Infrastructure Security | json | LOW | Ensure Telnet' (TCP,23) is not exposed to private hosts more than 32 | AC_AWS_0359 |
| Infrastructure Security | json | HIGH | Ensure Elasticsearch (TCP,9300) is not accessible by a public CIDR block range | AC_AWS_0318 |
| Infrastructure Security | json | LOW | Ensure SSH (TCP,22) is not accessible by a public CIDR block range | AC_AWS_0319 |
| Infrastructure Security | json | LOW | Ensure OracleDatabaseServer' (TCP,521) is not exposed to private hosts more than 32 | AC_AWS_0358 |
| Infrastructure Security | json | HIGH | Ensure no security groups allow ingress from 0.0.0.0/0 to ALL ports and protocols | AC_AWS_0231 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - SNMP (UDP,161) | AC_AWS_0266 |
| Infrastructure Security | json | MEDIUM | Ensure MSSQL Server (TCP,1433) is not accessible by a public CIDR block range | AC_AWS_0289 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports remote desktop port (TCP,3389) is not exposed to private hosts more than 32 | AC_AWS_0323 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Oracle Database Server (TCP,1521) | AC_AWS_0270 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports MemcachedSSL (UDP,11215) is not exposed to private hosts more than 32 | AC_AWS_0335 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - (SSH,22) | AC_AWS_0227 |
| Infrastructure Security | json | LOW | Ensure MongoDB' (TCP,27017) is not exposed to private hosts more than 32 | AC_AWS_0362 |
| Infrastructure Security | json | HIGH | Ensure CIFS for file/printer (TCP,445) is not accessible by a public CIDR block range | AC_AWS_0315 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Memcached SSL (UDP,11214) | AC_AWS_0250 |
| Infrastructure Security | json | LOW | Ensure MongoWebPortal' (TCP,27018) is not exposed to private hosts more than 32 | AC_AWS_0342 |
| Infrastructure Security | json | LOW | Ensure PuppetMaster' (TCP,8140) is not exposed to private hosts more than 32 | AC_AWS_0354 |
| Infrastructure Security | json | MEDIUM | Ensure Oracle DB SSL (UDP,2484) is not accessible by a public CIDR block range | AC_AWS_0303 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - MSSQL Debugger (TCP,135) | AC_AWS_0246 |
| Infrastructure Security | json | MEDIUM | Ensure LDAP SSL (TCP,636) is not accessible by a public CIDR block range | AC_AWS_0285 |
| Infrastructure Security | json | MEDIUM | Ensure Memcached SSL (UDP,11215) is not accessible by a public CIDR block range | AC_AWS_0293 |
| Infrastructure Security | json | LOW | Ensure HadoopNameNode' (TCP,9000) is not exposed to private hosts more than 32 | AC_AWS_0339 |
| Infrastructure Security | json | MEDIUM | Ensure SaltStack Master (TCP,4505) is not accessible by a public CIDR block range | AC_AWS_0277 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports MemcachedSSL (TCP,11214) is not exposed to private hosts more than 32 | AC_AWS_0332 |
| Infrastructure Security | json | MEDIUM | Ensure NetBios Datagram Service (TCP,138) is not accessible by a public CIDR block range | AC_AWS_0298 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Oracle DB SSL (UDP,2484) | AC_AWS_0261 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports Elasticsearch (TCP,9200) is not exposed to private hosts more than 32 | AC_AWS_0324 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - SaltStack Master (TCP,4506) | AC_AWS_0236 |
| Infrastructure Security | json | MEDIUM | Ensure SNMP (UDP,161) is not accessible by a public CIDR block range | AC_AWS_0308 |
| Infrastructure Security | json | LOW | Ensure OracleDBSSL' (TCP,2484) is not exposed to private hosts more than 32 | AC_AWS_0349 |
| Infrastructure Security | json | MEDIUM | Ensure Mongo Web Portal (TCP,27018) is not accessible by a public CIDR block range | AC_AWS_0294 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports MSSQLAdmin (TCP,1434) is not exposed to private hosts more than 32 | AC_AWS_0328 |
| Infrastructure Security | json | MEDIUM | Ensure Hadoop Name Node (TCP,9000) is not accessible by a public CIDR block range | AC_AWS_0282 |
| Infrastructure Security | json | MEDIUM | Ensure Postgres SQL (TCP,5432) is not accessible by a public CIDR block range | AC_AWS_0304 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Known internal web port (TCP,8000) | AC_AWS_0241 |
| Infrastructure Security | json | LOW | Ensure Prevalentknowninternalport' (TCP,3000) is not exposed to private hosts more than 32 | AC_AWS_0353 |
| Infrastructure Security | json | LOW | Ensure NetBIOSNameService' (UDP,137) is not exposed to private hosts more than 32 | AC_AWS_0345 |
| Infrastructure Security | json | HIGH | Ensure Oracle Database Server (TCP,1521) is not accessible by a public CIDR block range | AC_AWS_0312 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - NetBIOS Datagram Service (UDP,138) | AC_AWS_0257 |
| Infrastructure Security | json | HIGH | Ensure Telnet (TCP,23) is not accessible by a public CIDR block range | AC_AWS_0313 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - NetBIOS Datagram Service (TCP,138) | AC_AWS_0256 |
| Infrastructure Security | json | LOW | Ensure NetBIOSNameService' (UDP,137) is not exposed to private hosts more than 32 | AC_AWS_0344 |
| Infrastructure Security | json | LOW | Ensure PostgresSQL' (UDP,5432) is not exposed to private hosts more than 32 | AC_AWS_0352 |
| Infrastructure Security | json | MEDIUM | Ensure Postgres SQL (UDP,5432) is not accessible by a CIDR block range | AC_AWS_0305 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Hadoop Name Node (TCP,9000) | AC_AWS_0240 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports MSSQLBrowserService (UDP,1434) is not exposed to private hosts more than 32 | AC_AWS_0329 |
| Infrastructure Security | json | MEDIUM | Ensure Known internal web port (TCP,8000) is not accessible by a public CIDR block range | AC_AWS_0283 |
| Infrastructure Security | json | MEDIUM | Ensure MySQL (TCP,3306) is not accessible by a public CIDR block range | AC_AWS_0295 |
| Infrastructure Security | json | LOW | Ensure NetBIOSSessionService' (UDP,139) is not exposed to private hosts more than 32 | AC_AWS_0348 |
| Infrastructure Security | json | MEDIUM | Ensure SQL Server Analysis Service browser (TCP,2382) is not accessible by a public CIDR block range | AC_AWS_0309 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - CIFS / SMB (TCP,3020) | AC_AWS_0237 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Oracle DB SSL (TCP,2484) | AC_AWS_0260 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports SaltStackMaster (TCP,4506) is not exposed to private hosts more than 32 | AC_AWS_0325 |
| Infrastructure Security | json | HIGH | Ensure Unknown Port is not exposed to the entire internet | AC_AWS_0276 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports MemcachedSSL (TCP,11215) is not exposed to private hosts more than 32 | AC_AWS_0333 |
| Infrastructure Security | json | MEDIUM | Ensure NetBios Datagram Service (UDP,138) is not accessible by a public CIDR block range | AC_AWS_0299 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - NetBIOS Session Service (UDP,139) | AC_AWS_0259 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Elasticsearch (TCP,9200) | AC_AWS_0234 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports CassandraOpsCenteragent (TCP,61621) is not exposed to private hosts more than 32 | AC_AWS_0326 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Postgres SQL (UDP,5432) | AC_AWS_0263 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports MSSQLDebugger (TCP,135) is not exposed to private hosts more than 32 | AC_AWS_0330 |
| Infrastructure Security | json | HIGH | Ensure no security groups is wide open to public, that is, allows traffic from 0.0.0.0/0 to ALL ports and protocols | AC_AWS_0275 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - NetBIOS Name Service (UDP,137) | AC_AWS_0255 |
| Infrastructure Security | json | MEDIUM | Ensure SQL Server Analysis Services (TCP,2383) is not accessible by a public CIDR block range | AC_AWS_0310 |
| Infrastructure Security | json | LOW | Ensure NetBIOSSessionService' (TCP,139) is not exposed to private hosts more than 32 | AC_AWS_0347 |
| Infrastructure Security | json | LOW | Ensure PostgresSQL' (TCP,5432) is not exposed to private hosts more than 32 | AC_AWS_0351 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - LDAP SSL (TCP,636) | AC_AWS_0243 |
| Infrastructure Security | json | MEDIUM | Ensure Prevalent known internal port (TCP,3000) is not accessible by a public CIDR block range | AC_AWS_0306 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Cassandra OpsCenter agent (TCP,61621) | AC_AWS_0238 |
| Infrastructure Security | json | MEDIUM | Ensure Cassandra OpsCenter agent port (TCP,61621) is not accessible by a public CIDR block range | AC_AWS_0280 |
| Infrastructure Security | json | MEDIUM | Ensure NetBIOS Name Service (TCP,137) is not accessible by a public CIDR block range | AC_AWS_0296 |
| Infrastructure Security | json | MEDIUM | Ensure CIFS / SMB (TCP,3020) is not accessible by a public CIDR block range | AC_AWS_0279 |
| Infrastructure Security | json | MEDIUM | Ensure NetBIOS Name Service (UDP,137) is not accessible by a public CIDR block range | AC_AWS_0297 |
| Infrastructure Security | json | MEDIUM | Ensure SaltStack Master (TCP,4506) is not accessible by a public CIDR block range | AC_AWS_0278 |
| Infrastructure Security | json | MEDIUM | Ensure Cassandra (TCP,7001) is not accessible by a public CIDR block range | AC_AWS_0281 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Cassandra (TCP,7001) | AC_AWS_0239 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Known internal web port (TCP,8080) | AC_AWS_0242 |
| Infrastructure Security | json | MEDIUM | Ensure Puppet Master (TCP:8140) is not accessible by a public CIDR block range | AC_AWS_0307 |
| Infrastructure Security | json | LOW | Ensure OracleDBSSL' (UDP,2484) is not exposed to private hosts more than 32 | AC_AWS_0350 |
| Infrastructure Security | json | LOW | Ensure NetBIOSDatagramService' (UDP,138) is not exposed to private hosts more than 32 | AC_AWS_0346 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - NetBIOS Name Service (TCP,137) | AC_AWS_0254 |
| Infrastructure Security | json | MEDIUM | Ensure SaltStack Master (TCP,4505) is not accessible by a public CIDR block range | AC_AWS_0311 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports MSSQLServer (TCP,1433) is not exposed to private hosts more than 32 | AC_AWS_0331 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - MongoDB (TCP,27017) | AC_AWS_0274 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports Knowninternalwebport (TCP,8080) is not exposed to private hosts more than 32 | AC_AWS_0327 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Postgres SQL (TCP,5432) | AC_AWS_0262 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Elasticsearch (TCP,9300) | AC_AWS_0235 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - NetBIOS Session Service (TCP,139) | AC_AWS_0258 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - MySQL (TCP,3306) | AC_AWS_0253 |
| Infrastructure Security | json | HIGH | Ensure MongoDB (TCP,27017) is not accessible by a public CIDR block range | AC_AWS_0316 |
| Infrastructure Security | json | LOW | Ensure LDAPSSL' (TCP,636) is not exposed to private hosts more than 32 | AC_AWS_0341 |
| Infrastructure Security | json | LOW | Ensure SQLServerAnalysisServices' (TCP,2383) is not exposed to private hosts more than 32 | AC_AWS_0357 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - MSSQL Browser Service (UDP,1434) | AC_AWS_0245 |
| Infrastructure Security | json | MEDIUM | Ensure NetBios Session Service (TCP,139) is not accessible by a CIDR block range | AC_AWS_0300 |
| Infrastructure Security | json | MEDIUM | Ensure MSSQL Admin (TCP,1434) is not accessible by a public CIDR block range | AC_AWS_0286 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - SaltStack Master (TCP,4505) | AC_AWS_0269 |
| Infrastructure Security | json | MEDIUM | Ensure Memcached SSL (TCP,11214) is not accessible by a public CIDR block range | AC_AWS_0290 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - (HTTP,80) | AC_AWS_0228 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Memcached SSL (TCP,11215) | AC_AWS_0249 |
| Infrastructure Security | json | HIGH | Ensure no default security groups are used as they allow ingress from 0.0.0.0/0 to ALL ports and protocols | AC_AWS_0232 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports SSH (TCP,22) is not exposed to private hosts more than 32 | AC_AWS_0320 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Puppet Master (TCP,8140) | AC_AWS_0265 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports MySQL (TCP,3306) is not exposed to private hosts more than 32 | AC_AWS_0336 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - CIFS for file/printer (TCP,445) | AC_AWS_0273 |
| Infrastructure Security | json | LOW | Ensure CIFSforfile/printer' (TCP,445) is not exposed to private hosts more than 32 | AC_AWS_0361 |
| Infrastructure Security | json | LOW | Ensure SMTP' (TCP,25) is not exposed to private hosts more than 32 | AC_AWS_0360 |
| Infrastructure Security | json | LOW | Ensure CIFS/SMB' (TCP,3020) is not exposed to private hosts more than 32 | AC_AWS_0337 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - SMTP (TCP,25) | AC_AWS_0272 |
| Infrastructure Security | json | LOW | Ensure Security Groups Unrestricted Specific Ports http (TCP,80) is not exposed to private hosts more than 32 | AC_AWS_0321 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Prevalent known internal port (TCP,3000) | AC_AWS_0264 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - SaltStack Master (TCP,4505) | AC_AWS_0233 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Memcached SSL (TCP,11214) | AC_AWS_0248 |
| Infrastructure Security | json | LOW | Security Groups - Unrestricted Specific Ports - (HTTPS,443) | AC_AWS_0229 |
| Infrastructure Security | json | MEDIUM | Ensure Memcached SSL (TCP,11215) is not accessible by a public CIDR block range | AC_AWS_0291 |
| Infrastructure Security | json | MEDIUM | Ensure MSSQL Browser Service (UDP,1434) is not accessible by a public CIDR block range | AC_AWS_0287 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - SQL Server Analysis Services (TCP,2383) | AC_AWS_0268 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - MSSQL Admin (TCP,1434) | AC_AWS_0244 |
| Infrastructure Security | json | MEDIUM | Ensure NetBios Session Service (UDP,139) is not accessible by a CIDR block range | AC_AWS_0301 |
| Infrastructure Security | json | LOW | Ensure SQLServerAnalysisServicebrowser' (TCP,2382) is not exposed to private hosts more than 32 | AC_AWS_0356 |
| Infrastructure Security | json | LOW | Ensure Knowninternalwebport' (TCP,8000) not exposed to private hosts more than 32 | AC_AWS_0340 |
| Infrastructure Security | json | HIGH | Security Groups - Unrestricted Specific Ports - Mongo Web Portal (TCP,27018) | AC_AWS_0252 |
| Infrastructure Security | json | HIGH | Ensure Elasticsearch (TCP,9200) is not accessible by a public CIDR block range | AC_AWS_0317 |
aws_api_gateway_method
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | APGM | LOW | Ensure there is no open access to back-end resources through API | AWS.APGM.IS.LOW.0056 |
aws_efs_file_system_policy
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | AEFSP | HIGH | Ensure EFS file system does not use insecure wildcard policies. | AWS.AEFSP.IAM.HIGH.0059 |
aws_ecs_service
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | ECS | HIGH | Ensure there are no ECS services Admin roles | AWS.ECS.High.0436 |
aws_globalaccelerator_accelerator
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | AGA | LOW | Ensure Global Accelerator accelerator has flow logs enabled. | AWS.AGA.LM.LOW.0073 |
aws_api_gateway_rest_api_policy
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | APGRAP | HIGH | Ensure use of API Gateway endpoint policy, and no action wildcards are being used. | AWS.APGRAP.IAM.HIGH.0064 |
5.3 - Azure Policies
azurerm_storage_container
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | azure | HIGH | Anonymous, public read access to a container and its blobs can be enabled in Azure Blob storage. This is only recommended if absolutely necessary. | accurics.azure.IAM.368 |
azurerm_mysql_server
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | azure | HIGH | Ensure ‘Enforce SSL connection’ is set to ‘ENABLED’ for MySQL Database Server. | accurics.azure.NS.361 |
azurerm_sql_firewall_rule
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | azure | MEDIUM | Restrict Azure SQL Server accessibility to a minimal address range | accurics.azure.NS.169 |
| Infrastructure Security | azure | HIGH | Ensure entire Azure infrastructure doesn’t have access to Azure SQL ServerEnsure entire Azure infrastructure doesn’t have access to Azure SQL Server | accurics.azure.NS.5 |
| Infrastructure Security | azure | MEDIUM | Ensure that no SQL Server allows ingress from 0.0.0.0/0 (ANY IP) | accurics.azure.NS.21 |
azurerm_key_vault
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | azure | MEDIUM | Ensure the key vault is recoverable - enable “Soft Delete” setting for a Key Vault | accurics.azure.EKM.164 |
| Logging and Monitoring | azure | HIGH | Ensure that logging for Azure KeyVault is ‘Enabled’ | accurics.azure.EKM.20 |
azurerm_resource_group
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | azure | LOW | Ensure that Azure Resource Group has resource lock enabled | accurics.azure.NS.272 |
azurerm_storage_account_network_rules
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | azure | MEDIUM | Ensure default network access rule for Storage Accounts is set to deny. | accurics.azure.NS.370 |
azurerm_storage_account
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | azure | HIGH | Ensure ‘Trusted Microsoft Services’ is enabled for Storage Account access | accurics.azure.NS.2 |
| Infrastructure Security | azure | HIGH | Ensure default network access rule for Storage Accounts is not open to public | accurics.azure.NS.4 |
| Data Protection | azure | HIGH | Ensure that ‘Secure transfer required’ is enabled for Storage Accounts | accurics.azure.EKM.7 |
azurerm_sql_server
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | azure | MEDIUM | Ensure that ‘Auditing’ is set to ‘On’ for SQL servers | accurics.azure.MON.354 |
| Identity and Access Management | azure | HIGH | Ensure that Azure Active Directory Admin is configured for SQL Server | accurics.azure.IAM.10 |
| Compliance Validation | azure | MEDIUM | Avoid using names like ‘Admin’ for an Azure SQL Server admin account login | accurics.azure.IAM.138 |
| Compliance Validation | azure | LOW | Ensure that ‘Auditing’ Retention is ‘greater than 90 days’ for SQL servers. | accurics.azure.LOG.356 |
azurerm_postgresql_configuration
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | azure | MEDIUM | Ensure server parameter ‘log_duration’ is set to ‘ON’ for PostgreSQL Database Server | accurics.azure.LOG.154 |
| Logging and Monitoring | azure | MEDIUM | Ensure server parameter ‘log_retention_days’ is greater than 3 days for PostgreSQL Database Server | accurics.azure.LOG.155 |
| Logging and Monitoring | azure | MEDIUM | Ensure server parameter ‘log_connections’ is set to ‘ON’ for PostgreSQL Database Server | accurics.azure.LOG.152 |
| Logging and Monitoring | azure | MEDIUM | Ensure server parameter ‘log_checkpoints’ is set to ‘ON’ for PostgreSQL Database Server | accurics.azure.LOG.364 |
| Logging and Monitoring | azure | MEDIUM | Ensure server parameter ‘log_disconnections’ is set to ‘ON’ for PostgreSQL Database Server | accurics.azure.LOG.153 |
| Logging and Monitoring | azure | MEDIUM | Ensure server parameter ‘connection_throttling’ is set to ‘ON’ for PostgreSQL Database Server | accurics.azure.LOG.151 |
azurerm_sql_database
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | azure | MEDIUM | Ensure that ‘Threat Detection’ is enabled for Azure SQL Database | accurics.azure.MON.157 |
azurerm_redis_cache
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Security Best Practices | azure | HIGH | Ensure that Redis is updated regularly with security and operational updates.Note this feature is only available to Premium tier Redis Caches. | accurics.azure.NS.13 |
| Infrastructure Security | azure | MEDIUM | Ensure that the Redis Cache accepts only SSL connections | accurics.azure.EKM.23 |
| Infrastructure Security | azure | HIGH | Ensure there are no firewall rules allowing unrestricted access to Redis from other Azure sources | accurics.azure.NS.31 |
| Infrastructure Security | azure | HIGH | Ensure there are no firewall rules allowing unrestricted access to Redis from the Internet | accurics.azure.NS.30 |
| Infrastructure Security | azure | MEDIUM | Ensure there are no firewall rules allowing Redis Cache access for a large number of source IPs | accurics.azure.NS.166 |
azurerm_mssql_server
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | azure | MEDIUM | Ensure that ‘Auditing’ is set to ‘On’ for MSSQL servers | accurics.azure.MON.355 |
| Logging and Monitoring | azure | MEDIUM | Ensure that ‘Auditing’ Retention is ‘greater than 90 days’ for MSSQL servers. | accurics.azure.LOG.357 |
azurerm_kubernetes_cluster
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | azure | MEDIUM | Ensure Kube Dashboard is disabled | accurics.azure.NS.383 |
| Infrastructure Security | azure | MEDIUM | Ensure AKS cluster has Network Policy configured. | accurics.azure.NS.382 |
azurerm_managed_disk
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | azure | MEDIUM | Ensure that ‘Unattached disks’ are encrypted in Azure Managed Disk | accurics.azure.EKM.156 |
azurerm_network_watcher_flow_log
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Resilience | azure | MEDIUM | Ensure that Network Security Group Flow Log retention period is ‘greater than 90 days’ for Azure Network Watcher Flow Log | accurics.azure.NS.342 |
| Logging and Monitoring | azure | HIGH | Enable Network Watcher for Azure subscriptions. Network diagnostic and visualization tools available with Network Watcher help users understand, diagnose, and gain insights to the network in Azure. | accurics.azure.NS.11 |
azurerm_key_vault_secret
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | azure | HIGH | Ensure that the expiration date is set on all secrets | accurics.azure.EKM.26 |
azurerm_key_vault_key
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | azure | HIGH | Ensure that the expiration date is set on all keys | accurics.azure.EKM.25 |
azurerm_security_center_contact
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | azure | MEDIUM | Ensure that ‘Send email notification for high severity alerts’ is set to ‘On’ | accurics.azure.MON.353 |
azurerm_network_security_rule
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | json | MEDIUM | Ensure Known internal web port (Tcp:8000) is not exposed to public for Azure Network Security Rule | AC_AZURE_0528 |
| Infrastructure Security | json | LOW | Ensure NetBIOS Name Service (Udp:137) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0482 |
| Infrastructure Security | json | LOW | Ensure Microsoft-DS (Tcp:445) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0494 |
| Infrastructure Security | json | LOW | Ensure MSSQL Debugger (Tcp:135) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0512 |
| Infrastructure Security | json | HIGH | Ensure PostgreSQL (Udp:5432) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0457 |
| Infrastructure Security | json | MEDIUM | Ensure Memcached SSL (Tcp:11215) is not exposed to public for Azure Network Security Rule | AC_AZURE_0504 |
| Infrastructure Security | json | MEDIUM | Ensure SQL Server Analysis (Tcp:2382) is not exposed to public for Azure Network Security Rule | AC_AZURE_0441 |
| Infrastructure Security | json | LOW | Ensure POP3 (Tcp:110) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0461 |
| Infrastructure Security | json | LOW | Ensure Known internal web port (Tcp:8080) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0524 |
| Infrastructure Security | json | HIGH | Ensure SaltStack Master (Tcp:4505) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0436 |
| Infrastructure Security | json | MEDIUM | Ensure NetBIOS Datagram Service (Udp:138) is not exposed to public for Azure Network Security Rule | AC_AZURE_0477 |
| Infrastructure Security | json | HIGH | Ensure Hadoop Name Node (Tcp:9000) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0532 |
| Infrastructure Security | json | MEDIUM | Ensure Memcached SSL (Udp:11215) is not exposed to public for Azure Network Security Rule | AC_AZURE_0498 |
| Infrastructure Security | json | MEDIUM | Ensure CIFS / SMB (Tcp:3020) is not exposed to public for Azure Network Security Rule | AC_AZURE_0271 |
| Infrastructure Security | json | HIGH | Ensure Memcached SSL (Tcp:11214) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0508 |
| Infrastructure Security | json | LOW | Ensure MSSQL Server (Tcp:1433) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0509 |
| Infrastructure Security | json | HIGH | Ensure CIFS / SMB (Tcp:3020) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0270 |
| Infrastructure Security | json | LOW | Ensure NetBIOS Datagram Service (Udp:138) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0476 |
| Infrastructure Security | json | LOW | Ensure DNS (Udp:53) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0533 |
| Infrastructure Security | json | HIGH | Ensure Memcached SSL (Udp:11215) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0499 |
| Infrastructure Security | json | LOW | Ensure server is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0421 |
| Infrastructure Security | json | LOW | Ensure SQL Server Analysis (Tcp:2383) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0437 |
| Infrastructure Security | json | HIGH | Ensure PostgreSQL (Tcp:5432) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0460 |
| Infrastructure Security | json | MEDIUM | Ensure Known internal web port (Tcp:8080) is not exposed to public for Azure Network Security Rule | AC_AZURE_0525 |
| Infrastructure Security | json | HIGH | Ensure Memcached SSL (Tcp:11215) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0505 |
| Infrastructure Security | json | LOW | Ensure SQL Server Analysis (Tcp:2382) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0440 |
| Infrastructure Security | json | HIGH | Ensure SSH (Tcp:22) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0285 |
| Infrastructure Security | json | MEDIUM | Ensure MSSQL Debugger (Tcp:135) is not exposed to public for Azure Network Security Rule | AC_AZURE_0513 |
| Infrastructure Security | json | MEDIUM | Ensure PostgreSQL (Udp:5432) is not exposed to public for Azure Network Security Rule | AC_AZURE_0456 |
| Infrastructure Security | json | MEDIUM | Ensure Microsoft-DS (Tcp:445) is not exposed to public for Azure Network Security Rule | AC_AZURE_0495 |
| Infrastructure Security | json | HIGH | Ensure that RDP access is restricted from the internet for Azure Network Security Rule | AC_AZURE_0342 |
| Infrastructure Security | json | HIGH | Ensure Known internal web port (Tcp:8000) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0529 |
| Infrastructure Security | json | MEDIUM | Ensure NetBIOS Name Service (Udp:137) is not exposed to public for Azure Network Security Rule | AC_AZURE_0483 |
| Infrastructure Security | json | LOW | Ensure Oracle DB SSL (Tcp:2484) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0467 |
| Infrastructure Security | json | LOW | Ensure MySQL (Tcp:3306) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0488 |
| Infrastructure Security | json | MEDIUM | Ensure LDAP SSL (Tcp:636) is not exposed to public for Azure Network Security Rule | AC_AZURE_0522 |
| Infrastructure Security | json | HIGH | Ensure Telnet (Tcp:23) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0430 |
| Infrastructure Security | json | MEDIUM | Ensure VNC Listener (Tcp:5500) is not exposed to public for Azure Network Security Rule | AC_AZURE_0426 |
| Infrastructure Security | json | MEDIUM | Ensure NetBIOS Session Service (Udp:139) is not exposed to public for Azure Network Security Rule | AC_AZURE_0471 |
| Infrastructure Security | json | MEDIUM | Ensure DNS (Udp:53) is not exposed to public for Azure Network Security Rule | AC_AZURE_0534 |
| Infrastructure Security | json | LOW | Ensure MSSQL Admin (Tcp:1434) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0518 |
| Infrastructure Security | json | HIGH | Ensure NetBIOS Name Service (Udp:137) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0484 |
| Infrastructure Security | json | MEDIUM | Ensure Mongo Web Portal (Tcp:27018) is not exposed to public for Azure Network Security Rule | AC_AZURE_0492 |
| Infrastructure Security | json | HIGH | Ensure MSSQL Debugger (Tcp:135) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0514 |
| Infrastructure Security | json | HIGH | Ensure Puppet Master (Tcp:8140) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0451 |
| Infrastructure Security | json | HIGH | Ensure Memcached SSL (Udp:11214) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0502 |
| Infrastructure Security | json | MEDIUM | Ensure SMTP (Tcp:25) is not exposed to public for Azure Network Security Rule | AC_AZURE_0447 |
| Infrastructure Security | json | LOW | Ensure Memcached SSL (Tcp:11215) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0503 |
| Infrastructure Security | json | LOW | Ensure SMTP (Tcp:25) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0446 |
| Infrastructure Security | json | LOW | Ensure MSSQL Browser (Udp:1434) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0515 |
| Infrastructure Security | json | MEDIUM | Ensure Puppet Master (Tcp:8140) is not exposed to public for Azure Network Security Rule | AC_AZURE_0450 |
| Infrastructure Security | json | HIGH | Ensure Mongo Web Portal (Tcp:27018) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0493 |
| Infrastructure Security | json | LOW | Ensure NetBIOS Name Service (Tcp:137) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0485 |
| Infrastructure Security | json | HIGH | Ensure Cassandra OpsCenter (Tcp:61621) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0276 |
| Infrastructure Security | json | MEDIUM | Ensure MSSQL Admin (Tcp:1434) is not exposed to public for Azure Network Security Rule | AC_AZURE_0519 |
| Infrastructure Security | json | LOW | Ensure NetBIOS Session Service (Udp:139) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0470 |
| Infrastructure Security | json | HIGH | Ensure DNS (Udp:53) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0535 |
| Infrastructure Security | json | HIGH | Ensure VNC Listener (Tcp:5500) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0427 |
| Infrastructure Security | json | LOW | Ensure SaltStack Master (Tcp:4506) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0431 |
| Infrastructure Security | json | HIGH | Ensure Oracle DB SSL (Udp:2484) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0466 |
| Infrastructure Security | json | MEDIUM | Ensure MySQL (Tcp:3306) is not exposed to public for Azure Network Security Rule | AC_AZURE_0489 |
| Infrastructure Security | json | HIGH | Ensure LDAP SSL (Tcp:636) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0523 |
| Infrastructure Security | json | LOW | Ensure Puppet Master (Tcp:8140) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0449 |
| Infrastructure Security | json | LOW | Ensure Cassandra (Tcp:7001) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0275 |
| Infrastructure Security | json | LOW | Ensure Cassandra OpsCenter (Tcp:61621) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0536 |
| Infrastructure Security | json | LOW | Ensure NetBIOS Session Service (Tcp:139) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0473 |
| Infrastructure Security | json | HIGH | Ensure VNC Server (Tcp:5900) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0424 |
| Infrastructure Security | json | MEDIUM | Ensure SaltStack Master (Tcp:4506) is not exposed to public for Azure Network Security Rule | AC_AZURE_0432 |
| Infrastructure Security | json | HIGH | Ensure MSSQL Admin (Tcp:1434) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0520 |
| Infrastructure Security | json | MEDIUM | Ensure Oracle DB SSL (Udp:2484) is not exposed to public for Azure Network Security Rule | AC_AZURE_0465 |
| Infrastructure Security | json | HIGH | Ensure SNMP (Udp:161) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0445 |
| Infrastructure Security | json | LOW | Ensure Memcached SSL (Udp:11214) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0500 |
| Infrastructure Security | json | MEDIUM | Ensure Prevalent known internal port (Tcp:3000) is not exposed to public for Azure Network Security Rule | AC_AZURE_0453 |
| Infrastructure Security | json | MEDIUM | Ensure MSSQL Browser (Udp:1434) is not exposed to public for Azure Network Security Rule | AC_AZURE_0516 |
| Infrastructure Security | json | HIGH | Ensure MySQL (Tcp:3306) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0490 |
| Infrastructure Security | json | LOW | Ensure Telnet (Tcp:23) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0428 |
| Infrastructure Security | json | MEDIUM | Ensure NetBIOS Name Service (Tcp:137) is not exposed to public for Azure Network Security Rule | AC_AZURE_0486 |
| Infrastructure Security | json | HIGH | Ensure Oracle DB SSL (Tcp:2484) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0469 |
| Infrastructure Security | json | HIGH | Ensure NetBIOS Name Service (Tcp:137) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0487 |
| Infrastructure Security | json | MEDIUM | Ensure Oracle DB SSL (Tcp:2484) is not exposed to public for Azure Network Security Rule | AC_AZURE_0468 |
| Infrastructure Security | json | MEDIUM | Ensure Telnet (Tcp:23) is not exposed to public for Azure Network Security Rule | AC_AZURE_0429 |
| Infrastructure Security | json | LOW | Ensure Mongo Web Portal (Tcp:27018) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0491 |
| Infrastructure Security | json | LOW | Ensure Prevalent known internal port (Tcp:3000) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0452 |
| Infrastructure Security | json | HIGH | Ensure MSSQL Browser (Udp:1434) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0517 |
| Infrastructure Security | json | MEDIUM | Ensure SNMP (Udp:161) is not exposed to public for Azure Network Security Rule | AC_AZURE_0444 |
| Infrastructure Security | json | MEDIUM | Ensure Memcached SSL (Udp:11214) is not exposed to public for Azure Network Security Rule | AC_AZURE_0501 |
| Infrastructure Security | json | LOW | Ensure LDAP SSL (Tcp:636) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0521 |
| Infrastructure Security | json | LOW | Ensure Oracle DB SSL (Udp:2484) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0464 |
| Infrastructure Security | json | HIGH | Ensure SaltStack Master (Tcp:4506) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0433 |
| Infrastructure Security | json | LOW | Ensure VNC Listener (Tcp:5500) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0425 |
| Infrastructure Security | json | MEDIUM | Ensure Cassandra OpsCenter (Tcp:61621) is not exposed to public for Azure Network Security Rule | AC_AZURE_0537 |
| Infrastructure Security | json | HIGH | Ensure NetBIOS Session Service (Udp:139) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0472 |
| Infrastructure Security | json | MEDIUM | Ensure Cassandra (Tcp:7001) is not exposed to public for Azure Network Security Rule | AC_AZURE_0274 |
| Infrastructure Security | json | HIGH | Ensure SMTP (Tcp:25) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0448 |
| Infrastructure Security | json | LOW | Ensure SNMP (Udp:161) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0443 |
| Infrastructure Security | json | LOW | Ensure Memcached SSL (Tcp:11214) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0506 |
| Infrastructure Security | json | MEDIUM | Ensure SSH (Tcp:22) is not exposed to public for Azure Network Security Rule | AC_AZURE_0286 |
| Infrastructure Security | json | LOW | Ensure PostgreSQL (Udp:5432) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0455 |
| Infrastructure Security | json | MEDIUM | Ensure MSSQL Server (Tcp:1433) is not exposed to public for Azure Network Security Rule | AC_AZURE_0510 |
| Infrastructure Security | json | HIGH | Ensure Microsoft-DS (Tcp:445) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0496 |
| Infrastructure Security | json | LOW | Ensure NetBIOS Datagram Service (Tcp:138) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0479 |
| Infrastructure Security | json | HIGH | Ensure that request initiated from all ports () for all destination ports () is restricted from the internet for Azure Network Security Rule | AC_AZURE_0357 |
| Infrastructure Security | json | MEDIUM | Ensure SQL Server Analysis (Tcp:2383) is not exposed to public for Azure Network Security Rule | AC_AZURE_0438 |
| Infrastructure Security | json | MEDIUM | Ensure NetBIOS Datagram Service (Tcp:138) is not exposed to public for Azure Network Security Rule | AC_AZURE_0480 |
| Infrastructure Security | json | HIGH | Ensure Cassandra (Tcp:7001) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0273 |
| Infrastructure Security | json | MEDIUM | Ensure PostgreSQL (Tcp:5432) is not exposed to public for Azure Network Security Rule | AC_AZURE_0459 |
| Infrastructure Security | json | LOW | Ensure Hadoop Name Node (Tcp:9000) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0530 |
| Infrastructure Security | json | HIGH | Ensure NetBIOS Session Service (Tcp:139) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0475 |
| Infrastructure Security | json | LOW | Ensure VNC Server (Tcp:5900) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0422 |
| Infrastructure Security | json | LOW | Ensure SaltStack Master (Tcp:4505) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0434 |
| Infrastructure Security | json | HIGH | Ensure Known internal web port (Tcp:8080) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0526 |
| Infrastructure Security | json | HIGH | Ensure POP3 (Tcp:110) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0463 |
| Infrastructure Security | json | LOW | Ensure Known internal web port (Tcp:8000) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0527 |
| Infrastructure Security | json | MEDIUM | Ensure POP3 (Tcp:110) is not exposed to public for Azure Network Security Rule | AC_AZURE_0462 |
| Infrastructure Security | json | MEDIUM | Ensure SaltStack Master (Tcp:4505) is not exposed to public for Azure Network Security Rule | AC_AZURE_0435 |
| Infrastructure Security | json | MEDIUM | Ensure VNC Server (Tcp:5900) is not exposed to public for Azure Network Security Rule | AC_AZURE_0423 |
| Infrastructure Security | json | MEDIUM | Ensure Hadoop Name Node (Tcp:9000) is not exposed to public for Azure Network Security Rule | AC_AZURE_0531 |
| Infrastructure Security | json | MEDIUM | Ensure NetBIOS Session Service (Tcp:139) is not exposed to public for Azure Network Security Rule | AC_AZURE_0474 |
| Infrastructure Security | json | LOW | Ensure PostgreSQL (Tcp:5432) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0458 |
| Infrastructure Security | json | LOW | Ensure CIFS / SMB (Tcp:3020) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0272 |
| Infrastructure Security | json | HIGH | Ensure NetBIOS Datagram Service (Tcp:138) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0481 |
| Infrastructure Security | json | HIGH | Ensure SQL Server Analysis (Tcp:2383) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0439 |
| Infrastructure Security | json | LOW | Ensure Memcached SSL (Udp:11215) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0497 |
| Infrastructure Security | json | HIGH | Ensure NetBIOS Datagram Service (Udp:138) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0478 |
| Infrastructure Security | json | HIGH | Ensure Prevalent known internal port (Tcp:3000) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0454 |
| Infrastructure Security | json | HIGH | Ensure MSSQL Server (Tcp:1433) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0511 |
| Infrastructure Security | json | LOW | Ensure SSH (Tcp:22) is not exposed to private hosts more than 32 for Azure Network Security Rule | AC_AZURE_0287 |
| Infrastructure Security | json | HIGH | Ensure SQL Server Analysis (Tcp:2382) is not exposed to entire internet for Azure Network Security Rule | AC_AZURE_0442 |
| Infrastructure Security | json | MEDIUM | Ensure Memcached SSL (Tcp:11214) is not exposed to public for Azure Network Security Rule | AC_AZURE_0507 |
azurerm_cosmosdb_account
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | azure | HIGH | Ensure to filter source Ips for Cosmos DB Account | accurics.azure.NS.32 |
| Compliance Validation | azure | MEDIUM | Ensure that Cosmos DB Account has an associated tag | accurics.azure.CAM.162 |
azurerm_security_center_subscription_pricing
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Security Best Practices | azure | MEDIUM | Ensure that standard pricing tiers are selected | accurics.azure.OPS.349 |
azurerm_sql_active_directory_administrator
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Compliance Validation | azure | MEDIUM | Avoid using names like ‘Admin’ for an Azure SQL Server Active Directory Administrator account | accurics.azure.IAM.137 |
azurerm_container_registry
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | azure | MEDIUM | Ensure that admin user is disabled for Container Registry | accurics.azure.EKM.164 |
| Resilience | azure | HIGH | Ensure Container Registry has locks | accurics.azure.AKS.3 |
azurerm_virtual_network
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | azure | MEDIUM | Ensure that Azure Virtual Network subnet is configured with a Network Security Group | accurics.azure.NS.161 |
azurerm_role_assignment
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | azure | HIGH | Ensure that there are no guest users | accurics.azure.IAM.388 |
azurerm_application_gateway
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | azure | MEDIUM | Ensure Azure Application Gateway Web application firewall (WAF) is enabled | accurics.azure.NS.147 |
azurerm_postgresql_server
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | azure | HIGH | Ensure ‘Enforce SSL connection’ is set to ‘ENABLED’ for PostgreSQL Database Server | accurics.azure.EKM.1 |
| Resilience | azure | MEDIUM | Ensure that Geo Redundant Backups is enabled on PostgreSQL | accurics.azure.BDR.163 |
5.4 - GCP Policies
google_container_node_pool
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Security Best Practices | gcp | LOW | Ensure ‘Automatic node upgrade’ is enabled for Kubernetes Clusters. | accurics.gcp.OPS.101 |
| Compliance Validation | gcp | HIGH | Ensure Container-Optimized OS (cos) is used for Kubernetes Engine Clusters Node image. | accurics.gcp.OPS.114 |
| Security Best Practices | gcp | LOW | Ensure ‘Automatic node repair’ is enabled for Kubernetes Clusters. | accurics.gcp.OPS.144 |
github_repository
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | gcp | MEDIUM | Repository is Not Private. | accurics.gcp.IAM.145 |
google_bigquery_dataset
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | gcp | HIGH | BigQuery datasets may be anonymously or publicly accessible. | accurics.gcp.IAM.106 |
google_compute_project_metadata
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | gcp | HIGH | Ensure oslogin is enabled for a Project | accurics.gcp.IAM.127 |
google_compute_subnetwork
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | gcp | MEDIUM | Ensure that VPC Flow Logs is enabled for every subnet in a VPC Network. | accurics.gcp.LOG.118 |
google_project_iam_audit_config
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | gcp | LOW | Ensure that Cloud Audit Logging is configured properly across all services and all users from a project. | accurics.gcp.LOG.010 |
google_sql_database_instance
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Resilience | gcp | HIGH | Ensure all Cloud SQL database instance have backup configuration enabled. | accurics.gcp.BDR.105 |
| Infrastructure Security | gcp | HIGH | Ensure that Cloud SQL database Instances are not open to the world. | accurics.gcp.NS.102 |
| Infrastructure Security | gcp | HIGH | Ensure that Cloud SQL database instance requires all incoming connections to use SSL | accurics.gcp.EKM.141 |
google_compute_instance
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | gcp | MEDIUM | Ensure IP forwarding is not enabled on Instances. | accurics.gcp.NS.130 |
| Infrastructure Security | gcp | HIGH | Ensure ‘Block Project-wide SSH keys’ is enabled for VM instances. | accurics.gcp.NS.126 |
| Data Protection | gcp | MEDIUM | VM disks attached to a compute instance should be encrypted with Customer Supplied Encryption Keys (CSEK) . | accurics.gcp.EKM.132 |
| Identity and Access Management | gcp | HIGH | Instances may have been configured to use the default service account with full access to all Cloud APIs | accurics.gcp.IAM.124 |
| Infrastructure Security | gcp | MEDIUM | Ensure ‘Enable connecting to serial ports’ is not enabled for VM instances. | accurics.gcp.NS.129 |
| Infrastructure Security | gcp | MEDIUM | Ensure Compute instances are launched with Shielded VM enabled. | accurics.gcp.NS.133 |
| Identity and Access Management | gcp | MEDIUM | Ensure that no instance in the project overrides the project setting for enabling OSLogin | accurics.gcp.IAM.128 |
| Infrastructure Security | gcp | HIGH | Instances may have been configured to use the default service account with full access to all Cloud APIs | accurics.gcp.NS.125 |
google_storage_bucket_iam_binding
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | gcp | MEDIUM | Ensure that Cloud Storage bucket is not anonymously or publicly accessible. | accurics.gcp.IAM.121 |
google_container_cluster
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | json | Medium | GKE Control Plane is exposed to few public IP addresses using master-authorized-network-config | AC-GC-IS-CC-M-0367 |
| Logging and Monitoring | gcp | HIGH | Ensure Stackdriver Monitoring is enabled on Kubernetes Engine Clusters. | accurics.gcp.MON.143 |
| Infrastructure Security | gcp | HIGH | Ensure Kubernetes Cluster is created with Private cluster enabled. | accurics.gcp.NS.117 |
| Compliance Validation | gcp | HIGH | Ensure PodSecurityPolicy controller is enabled on the Kubernetes Engine Clusters. | accurics.gcp.OPS.116 |
| Identity and Access Management | gcp | HIGH | Ensure GKE basic auth is disabled. | accurics.gcp.IAM.110 |
| Infrastructure Security | gcp | HIGH | Ensure Master Authentication is set to enabled on Kubernetes Engine Clusters. | accurics.gcp.NS.112 |
| Compliance Validation | gcp | HIGH | Ensure Kubernetes Cluster is created with Alias IP ranges enabled | accurics.gcp.OPS.115 |
| Infrastructure Security | gcp | HIGH | Ensure GKE Control Plane is not public. | accurics.gcp.NS.109 |
| Identity and Access Management | gcp | MEDIUM | Ensure Kubernetes Cluster is created with Client Certificate disabled. | accurics.gcp.IAM.104 |
| Compliance Validation | gcp | HIGH | Ensure Kubernetes Clusters are configured with Labels. | accurics.gcp.OPS.113 |
| Identity and Access Management | gcp | HIGH | Ensure Legacy Authorization is set to disabled on Kubernetes Engine Clusters. | accurics.gcp.IAM.142 |
| Logging and Monitoring | gcp | HIGH | Ensure Stackdriver Logging is enabled on Kubernetes Engine Clusters. | accurics.gcp.LOG.100 |
| Infrastructure Security | gcp | HIGH | Ensure Network policy is enabled on Kubernetes Engine Clusters. | accurics.gcp.NS.103 |
google_project
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | gcp | MEDIUM | Ensure that the default network does not exist in a project. | accurics.gcp.NS.119 |
google_compute_firewall
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | json | MEDIUM | Ensure Puppet Master (TCP:8140) is not exposed to public for Google Compute Firewall | AC_GCP_0049 |
| Infrastructure Security | json | HIGH | Ensure Remote Desktop (TCP:3389) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0225 |
| Infrastructure Security | json | HIGH | Ensure LDAP SSL (TCP:636) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0161 |
| Infrastructure Security | json | MEDIUM | Ensure SaltStack Master (TCP:4506) is not exposed to public for Google Compute Firewall | AC_GCP_0073 |
| Infrastructure Security | json | MEDIUM | Ensure Cassandra (TCP:7001) is not exposed to public for Google Compute Firewall | AC_GCP_0136 |
| Infrastructure Security | json | HIGH | Ensure VNC Listener (TCP:5500) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0065 |
| Infrastructure Security | json | LOW | Ensure Memcached SSL (UDP:11215) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0120 |
| Infrastructure Security | json | MEDIUM | Ensure Oracle DB (TCP:1521) is not exposed to public for Google Compute Firewall | AC_GCP_0209 |
| Infrastructure Security | json | HIGH | Ensure Cassandra Internode Communication (TCP:7000) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0198 |
| Infrastructure Security | json | LOW | Ensure Elastic Search (TCP:9300) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0177 |
| Infrastructure Security | json | MEDIUM | Ensure NetBios Datagram Service (TCP:138) is not exposed to public for Google Compute Firewall | AC_GCP_0100 |
| Infrastructure Security | json | LOW | Ensure Mongo Web Portal (TCP:27018) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0045 |
| Infrastructure Security | json | MEDIUM | Ensure MSSQL Server (TCP:1433) is not exposed to public for Google Compute Firewall | AC_GCP_0157 |
| Infrastructure Security | json | LOW | Ensure Postgres SQL (TCP:5432) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0141 |
| Infrastructure Security | json | HIGH | Ensure Microsoft-DS (TCP:445) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0116 |
| Infrastructure Security | json | HIGH | Ensure SQL Server Analysis Service browser (TCP:2382) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0053 |
| Infrastructure Security | json | HIGH | Ensure Elastic Search (TCP:9200) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0182 |
| Infrastructure Security | json | HIGH | Ensure LDAP (UDP:389) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0213 |
| Infrastructure Security | json | LOW | Ensure NetBios Session Service (UDP:139) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0090 |
| Infrastructure Security | json | LOW | Ensure Oracle DB (TCP:2483) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0205 |
| Infrastructure Security | json | LOW | Ensure Known internal web port (TCP:8000) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0069 |
| Infrastructure Security | json | HIGH | Ensure DNS (UDP:53) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0086 |
| Infrastructure Security | json | HIGH | Ensure Cassandra Monitoring (TCP:7199) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0194 |
| Infrastructure Security | json | HIGH | Ensure Known internal web port (TCP:8080) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0068 |
| Infrastructure Security | json | LOW | Ensure SNMP (UDP:161) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0087 |
| Infrastructure Security | json | HIGH | Ensure Oracle DB (UDP:2483) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0204 |
| Infrastructure Security | json | MEDIUM | Ensure NetBios Session Service (UDP:139) is not exposed to public for Google Compute Firewall | AC_GCP_0091 |
| Infrastructure Security | json | MEDIUM | Ensure LDAP (UDP:389) is not exposed to public for Google Compute Firewall | AC_GCP_0212 |
| Infrastructure Security | json | LOW | Ensure Cassandra Thrift (TCP:9160) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0183 |
| Infrastructure Security | json | LOW | Ensure Telnet (TCP:23) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0117 |
| Infrastructure Security | json | MEDIUM | Ensure SQL Server Analysis Service browser (TCP:2382) is not exposed to public for Google Compute Firewall | AC_GCP_0052 |
| Infrastructure Security | json | HIGH | Ensure Postgres SQL (UDP:5432) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0140 |
| Infrastructure Security | json | LOW | Ensure MSSQL Server (TCP:1433) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0156 |
| Infrastructure Security | json | HIGH | Ensure NetBios Datagram Service (TCP:138) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0101 |
| Infrastructure Security | json | HIGH | Ensure Cassandra OpsCenter agent (TCP:61621) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0044 |
| Infrastructure Security | json | HIGH | Ensure SSH (TCP:20) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0228 |
| Infrastructure Security | json | LOW | Ensure Redis (TCP:6379) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0199 |
| Infrastructure Security | json | HIGH | Ensure Unencrypted Memcached Instances (TCP:11211) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0176 |
| Infrastructure Security | json | LOW | Ensure Oracle DB (TCP:1521) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0208 |
| Infrastructure Security | json | MEDIUM | Ensure VNC Listener (TCP:5500) is not exposed to public for Google Compute Firewall | AC_GCP_0064 |
| Infrastructure Security | json | MEDIUM | Ensure Memcached SSL (UDP:11215) is not exposed to public for Google Compute Firewall | AC_GCP_0121 |
| Infrastructure Security | json | LOW | Ensure SaltStack Master (TCP:4506) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0072 |
| Infrastructure Security | json | HIGH | Ensure Cassandra (TCP:7001) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0137 |
| Infrastructure Security | json | MEDIUM | Ensure LDAP SSL (TCP:636) is not exposed to public for Google Compute Firewall | AC_GCP_0160 |
| Infrastructure Security | json | MEDIUM | Ensure Remote Desktop (TCP:3389) is not exposed to public for Google Compute Firewall | AC_GCP_0224 |
| Infrastructure Security | json | LOW | Ensure Puppet Master (TCP:8140) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0048 |
| Infrastructure Security | json | MEDIUM | Ensure NetBIOS Name Service (TCP:137) is not exposed to public for Google Compute Firewall | AC_GCP_0106 |
| Infrastructure Security | json | MEDIUM | Ensure Cassandra OpsCenter agent (TCP:61621) is not exposed to public for Google Compute Firewall | AC_GCP_0043 |
| Infrastructure Security | json | MEDIUM | Ensure Oracle DB SSL (TCP:2484) is not exposed to public for Google Compute Firewall | AC_GCP_0151 |
| Infrastructure Security | json | LOW | Ensure Oracle DB SSL (UDP:2484) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0147 |
| Infrastructure Security | json | HIGH | Ensure POP3 (TCP:110) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0110 |
| Infrastructure Security | json | MEDIUM | Ensure MSSQL Browser Service (UDP:1434) is not exposed to public for Google Compute Firewall | AC_GCP_0055 |
| Infrastructure Security | json | MEDIUM | Ensure Cassandra Thrift (TCP:9160) is not exposed to public for Google Compute Firewall | AC_GCP_0184 |
| Infrastructure Security | json | MEDIUM | Ensure LDAP (TCP:389) is not exposed to public for Google Compute Firewall | AC_GCP_0215 |
| Infrastructure Security | json | MEDIUM | Ensure CIFS / SMB (TCP:3020) is not exposed to public for Google Compute Firewall | AC_GCP_0079 |
| Infrastructure Security | json | LOW | Ensure NetBios Datagram Service (TCP:138) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0096 |
| Infrastructure Security | json | MEDIUM | Ensure Oracle DB (UDP:2483) is not exposed to public for Google Compute Firewall | AC_GCP_0203 |
| Infrastructure Security | json | HIGH | Ensure CIFS / SMB (TCP:3020) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0080 |
| Infrastructure Security | json | LOW | Ensure Cassandra Monitoring (TCP:7199) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0192 |
| Infrastructure Security | json | LOW | Ensure Remote Desktop (TCP:3389) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0223 |
| Infrastructure Security | json | HIGH | Ensure MSSQL Admin (TCP:1434) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0059 |
| Infrastructure Security | json | HIGH | Ensure Cassandra Client (TCP:9042) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0188 |
| Infrastructure Security | json | HIGH | Ensure Cassandra OpsCenter Monitoring (TCP:61620) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0167 |
| Infrastructure Security | json | LOW | Ensure SaltStack Master (TCP:4505) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0075 |
| Infrastructure Security | json | MEDIUM | Ensure Memcached SSL (TCP:11214) is not exposed to public for Google Compute Firewall | AC_GCP_0130 |
| Infrastructure Security | json | HIGH | Ensure CiscoSecure, Websm (TCP:9090) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0219 |
| Infrastructure Security | json | LOW | Ensure VNC Listener (TCP:5500) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0063 |
| Infrastructure Security | json | LOW | Ensure Memcached SSL (UDP:11214) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0126 |
| Infrastructure Security | json | LOW | Ensure Unencrypted Memcached Instances (UDP:11211) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0171 |
| Infrastructure Security | json | HIGH | Ensure Unencrypted Mongo Instances (TCP:27017) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0170 |
| Infrastructure Security | json | HIGH | Ensure VNC Server (TCP:5900) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0062 |
| Infrastructure Security | json | MEDIUM | Ensure Memcached SSL (UDP:11214) is not exposed to public for Google Compute Firewall | AC_GCP_0127 |
| Infrastructure Security | json | MEDIUM | Ensure CiscoSecure, Websm (TCP:9090) is not exposed to public for Google Compute Firewall | AC_GCP_0218 |
| Infrastructure Security | json | HIGH | Ensure SaltStack Master (TCP:4506) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0074 |
| Infrastructure Security | json | HIGH | Ensure Memcached SSL (TCP:11214) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0131 |
| Infrastructure Security | json | LOW | Ensure Cassandra OpsCenter Website (TCP:8888) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0189 |
| Infrastructure Security | json | MEDIUM | Ensure Cassandra OpsCenter Monitoring (TCP:61620) is not exposed to public for Google Compute Firewall | AC_GCP_0166 |
| Infrastructure Security | json | MEDIUM | Ensure MSSQL Admin (TCP:1434) is not exposed to public for Google Compute Firewall | AC_GCP_0058 |
| Infrastructure Security | json | HIGH | Ensure Hadoop Name Node (TCP:9000) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0222 |
| Infrastructure Security | json | MEDIUM | Ensure Cassandra Monitoring (TCP:7199) is not exposed to public for Google Compute Firewall | AC_GCP_0193 |
| Infrastructure Security | json | LOW | Ensure Prevalent known internal port (TCP:3000) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0081 |
| Infrastructure Security | json | LOW | Ensure Oracle DB (UDP:2483) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0202 |
| Infrastructure Security | json | LOW | Ensure CIFS / SMB (TCP:3020) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0078 |
| Infrastructure Security | json | MEDIUM | Ensure NetBios Datagram Service (TCP:138) is not exposed to public for Google Compute Firewall | AC_GCP_0097 |
| Infrastructure Security | json | LOW | Ensure LDAP (TCP:389) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0214 |
| Infrastructure Security | json | HIGH | Ensure Cassandra Thrift (TCP:9160) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0185 |
| Infrastructure Security | json | LOW | Ensure SMTP (TCP:25) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0111 |
| Infrastructure Security | json | LOW | Ensure MSSQL Browser Service (UDP:1434) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0054 |
| Infrastructure Security | json | HIGH | Ensure MySQL (TCP:3306) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0146 |
| Infrastructure Security | json | LOW | Ensure Oracle DB SSL (TCP:2484) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0150 |
| Infrastructure Security | json | HIGH | Ensure NetBIOS Name Service (TCP:137) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0107 |
| Infrastructure Security | json | LOW | Ensure Cassandra OpsCenter agent (TCP:61621) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0042 |
| Infrastructure Security | json | MEDIUM | Ensure Cassandra OpsCenter Website (TCP:8888) is not exposed to public for Google Compute Firewall | AC_GCP_0190 |
| Infrastructure Security | json | MEDIUM | Ensure Prevalent known internal port (TCP:3000) is not exposed to public for Google Compute Firewall | AC_GCP_0082 |
| Infrastructure Security | json | HIGH | Ensure Memcached SSL (UDP:11214) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0128 |
| Infrastructure Security | json | HIGH | Ensure Redis (TCP:6379) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0201 |
| Infrastructure Security | json | MEDIUM | Ensure NetBios Session Service (TCP:139) is not exposed to public for Google Compute Firewall | AC_GCP_0094 |
| Infrastructure Security | json | LOW | Ensure CiscoSecure, Websm (TCP:9090) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0217 |
| Infrastructure Security | json | MEDIUM | Ensure Unencrypted Mongo Instances (TCP:27017) is not exposed to public for Google Compute Firewall | AC_GCP_0169 |
| Infrastructure Security | json | LOW | Ensure Cassandra Client (TCP:9042) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0186 |
| Infrastructure Security | json | LOW | Ensure MSSQL Admin (TCP:1434) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0057 |
| Infrastructure Security | json | MEDIUM | Ensure SMTP (TCP:25) is not exposed to public for Google Compute Firewall | AC_GCP_0112 |
| Infrastructure Security | json | MEDIUM | Ensure MySQL (TCP:3306) is not exposed to public for Google Compute Firewall | AC_GCP_0145 |
| Infrastructure Security | json | LOW | Ensure SQL Server Analysis Services (TCP:2383) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0153 |
| Infrastructure Security | json | HIGH | Ensure NetBIOS Name Service (UDP:137) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0104 |
| Infrastructure Security | json | HIGH | Ensure Unencrypted Memcached Instances (UDP:11211) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0173 |
| Infrastructure Security | json | MEDIUM | Ensure Memcached SSL (TCP:11215) is not exposed to public for Google Compute Firewall | AC_GCP_0124 |
| Infrastructure Security | json | MEDIUM | Ensure VNC Server (TCP:5900) is not exposed to public for Google Compute Firewall | AC_GCP_0061 |
| Infrastructure Security | json | HIGH | Ensure NetBios Datagram Service (TCP:138) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0098 |
| Infrastructure Security | json | LOW | Ensure Remote Desktop (TCP:3389) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0132 |
| Infrastructure Security | json | HIGH | Ensure SaltStack Master (TCP:4505) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0077 |
| Infrastructure Security | json | LOW | Ensure Cassandra OpsCenter Monitoring (TCP:61620) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0165 |
| Infrastructure Security | json | HIGH | Ensure Oracle DB SSL (UDP:2484) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0149 |
| Infrastructure Security | json | MEDIUM | Ensure Hadoop Name Node (TCP:9000) is not exposed to public for Google Compute Firewall | AC_GCP_0221 |
| Infrastructure Security | json | LOW | Ensure POP3 (TCP:110) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0108 |
| Infrastructure Security | json | MEDIUM | Ensure POP3 (TCP:110) is not exposed to public for Google Compute Firewall | AC_GCP_0109 |
| Infrastructure Security | json | LOW | Ensure Hadoop Name Node (TCP:9000) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0220 |
| Infrastructure Security | json | MEDIUM | Ensure Oracle DB SSL (UDP:2484) is not exposed to public for Google Compute Firewall | AC_GCP_0148 |
| Infrastructure Security | json | HIGH | Ensure MSSQL Debugger (TCP:135) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0164 |
| Infrastructure Security | json | LOW | Ensure NetBios Datagram Service (TCP:138) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0099 |
| Infrastructure Security | json | MEDIUM | Ensure Remote Desktop (TCP:3389) is not exposed to public for Google Compute Firewall | AC_GCP_0133 |
| Infrastructure Security | json | MEDIUM | Ensure SaltStack Master (TCP:4505) is not exposed to public for Google Compute Firewall | AC_GCP_0076 |
| Infrastructure Security | json | HIGH | Ensure Memcached SSL (TCP:11215) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0125 |
| Infrastructure Security | json | LOW | Ensure VNC Server (TCP:5900) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0060 |
| Infrastructure Security | json | MEDIUM | Ensure Unencrypted Memcached Instances (UDP:11211) is not exposed to public for Google Compute Firewall | AC_GCP_0172 |
| Infrastructure Security | json | LOW | Ensure NetBIOS Name Service (TCP:137) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0105 |
| Infrastructure Security | json | HIGH | Ensure Oracle DB SSL (TCP:2484) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0152 |
| Infrastructure Security | json | LOW | Ensure MySQL (TCP:3306) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0144 |
| Infrastructure Security | json | HIGH | Ensure MSSQL Browser Service (UDP:1434) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0056 |
| Infrastructure Security | json | HIGH | Ensure SMTP (TCP:25) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0113 |
| Infrastructure Security | json | LOW | Ensure Unencrypted Mongo Instances (TCP:27017) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0168 |
| Infrastructure Security | json | MEDIUM | Ensure Cassandra Client (TCP:9042) is not exposed to public for Google Compute Firewall | AC_GCP_0187 |
| Infrastructure Security | json | HIGH | Ensure LDAP (TCP:389) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0216 |
| Infrastructure Security | json | HIGH | Ensure NetBios Session Service (TCP:139) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0095 |
| Infrastructure Security | json | MEDIUM | Ensure Redis (TCP:6379) is not exposed to public for Google Compute Firewall | AC_GCP_0200 |
| Infrastructure Security | json | HIGH | Ensure Prevalent known internal port (TCP:3000) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0083 |
| Infrastructure Security | json | LOW | Ensure Memcached SSL (TCP:11214) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0129 |
| Infrastructure Security | json | HIGH | Ensure Cassandra OpsCenter Website (TCP:8888) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0191 |
| Infrastructure Security | json | MEDIUM | Ensure Unencrypted Memcached Instances (TCP:11211) is not exposed to public for Google Compute Firewall | AC_GCP_0175 |
| Infrastructure Security | json | HIGH | Ensure Memcached SSL (UDP:11215) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0122 |
| Infrastructure Security | json | MEDIUM | Ensure SNMP (UDP:161) is not exposed to public for Google Compute Firewall | AC_GCP_0088 |
| Infrastructure Security | json | MEDIUM | Ensure Known internal web port (TCP:8080) is not exposed to public for Google Compute Firewall | AC_GCP_0067 |
| Infrastructure Security | json | HIGH | Ensure Remote Desktop (TCP:3389) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0134 |
| Infrastructure Security | json | HIGH | Ensure Known internal web port (TCP:8000) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0071 |
| Infrastructure Security | json | MEDIUM | Ensure MSSQL Debugger (TCP:135) is not exposed to public for Google Compute Firewall | AC_GCP_0163 |
| Infrastructure Security | json | MEDIUM | Ensure Telnet (TCP:23) is not exposed to public for Google Compute Firewall | AC_GCP_0118 |
| Infrastructure Security | json | LOW | Ensure LDAP SSL (TCP:636) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0159 |
| Infrastructure Security | json | MEDIUM | Ensure SSH (TCP:20) is not exposed to public for Google Compute Firewall | AC_GCP_0227 |
| Infrastructure Security | json | HIGH | Ensure Elastic Search (TCP:9300) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0179 |
| Infrastructure Security | json | LOW | Ensure Cassandra Internode Communication (TCP:7000) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0196 |
| Infrastructure Security | json | LOW | Ensure DNS (UDP:53) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0084 |
| Infrastructure Security | json | HIGH | Ensure Oracle DB (TCP:2483) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0207 |
| Infrastructure Security | json | LOW | Ensure Postgres SQL (UDP:5432) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0138 |
| Infrastructure Security | json | HIGH | Ensure NetBios Session Service (UDP:139) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0092 |
| Infrastructure Security | json | LOW | Ensure LDAP (UDP:389) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0211 |
| Infrastructure Security | json | LOW | Ensure Elastic Search (TCP:9200) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0180 |
| Infrastructure Security | json | LOW | Ensure SQL Server Analysis Service browser (TCP:2382) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0051 |
| Infrastructure Security | json | LOW | Ensure Microsoft-DS (TCP:445) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0114 |
| Infrastructure Security | json | HIGH | Ensure Postgres SQL (TCP:5432) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0143 |
| Infrastructure Security | json | HIGH | Ensure SQL Server Analysis Services (TCP:2383) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0155 |
| Infrastructure Security | json | HIGH | Ensure Mongo Web Portal (TCP:27018) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0047 |
| Infrastructure Security | json | LOW | Ensure NetBIOS Name Service (UDP:137) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0102 |
| Infrastructure Security | json | MEDIUM | Ensure Mongo Web Portal (TCP:27018) is not exposed to public for Google Compute Firewall | AC_GCP_0046 |
| Infrastructure Security | json | MEDIUM | Ensure NetBIOS Name Service (UDP:137) is not exposed to public for Google Compute Firewall | AC_GCP_0103 |
| Infrastructure Security | json | MEDIUM | Ensure SQL Server Analysis Services (TCP:2383) is not exposed to public for Google Compute Firewall | AC_GCP_0154 |
| Infrastructure Security | json | MEDIUM | Ensure Postgres SQL (TCP:5432) is not exposed to public for Google Compute Firewall | AC_GCP_0142 |
| Infrastructure Security | json | HIGH | Ensure Puppet Master (TCP:8140) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0050 |
| Infrastructure Security | json | MEDIUM | Ensure Microsoft-DS (TCP:445) is not exposed to public for Google Compute Firewall | AC_GCP_0115 |
| Infrastructure Security | json | MEDIUM | Ensure Elastic Search (TCP:9200) is not exposed to public for Google Compute Firewall | AC_GCP_0181 |
| Infrastructure Security | json | HIGH | Ensure Oracle DB (TCP:1521) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0210 |
| Infrastructure Security | json | MEDIUM | Ensure Postgres SQL (UDP:5432) is not exposed to public for Google Compute Firewall | AC_GCP_0139 |
| Infrastructure Security | json | LOW | Ensure NetBios Session Service (TCP:139) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0093 |
| Infrastructure Security | json | MEDIUM | Ensure Oracle DB (TCP:2483) is not exposed to public for Google Compute Firewall | AC_GCP_0206 |
| Infrastructure Security | json | MEDIUM | Ensure DNS (UDP:53) is not exposed to public for Google Compute Firewall | AC_GCP_0085 |
| Infrastructure Security | json | MEDIUM | Ensure Elastic Search (TCP:9300) is not exposed to public for Google Compute Firewall | AC_GCP_0178 |
| Infrastructure Security | json | MEDIUM | Ensure Cassandra Internode Communication (TCP:7000) is not exposed to public for Google Compute Firewall | AC_GCP_0197 |
| Infrastructure Security | json | LOW | Ensure SSH (TCP:20) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0226 |
| Infrastructure Security | json | HIGH | Ensure MSSQL Server (TCP:1433) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0158 |
| Infrastructure Security | json | HIGH | Ensure Telnet (TCP:23) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0119 |
| Infrastructure Security | json | LOW | Ensure MSSQL Debugger (TCP:135) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0162 |
| Infrastructure Security | json | LOW | Ensure Cassandra (TCP:7001) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0135 |
| Infrastructure Security | json | MEDIUM | Ensure Known internal web port (TCP:8000) is not exposed to public for Google Compute Firewall | AC_GCP_0070 |
| Infrastructure Security | json | LOW | Ensure Memcached SSL (TCP:11215) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0123 |
| Infrastructure Security | json | HIGH | Ensure SNMP (UDP:161) is not exposed to entire internet for Google Compute Firewall | AC_GCP_0089 |
| Infrastructure Security | json | LOW | Ensure Known internal web port (TCP:8080) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0066 |
| Infrastructure Security | json | LOW | Ensure Unencrypted Memcached Instances (TCP:11211) is not exposed to private hosts more than 32 for Google Compute Firewall | AC_GCP_0174 |
google_dns_managed_zone
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | gcp | HIGH | Ensure that RSASHA1 is not used for the zone-signing and key-signing keys in Cloud DNS DNSSEC. | accurics.gcp.EKM.108 |
| Infrastructure Security | gcp | LOW | Ensure that DNSSEC is enabled for Cloud DNS. | accurics.gcp.NS.107 |
google_compute_disk
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Data Protection | gcp | MEDIUM | Ensure VM disks for critical VMs are encrypted with Customer Supplied Encryption Keys (CSEK) . | accurics.gcp.EKM.131 |
google_project_iam_member
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | gcp | HIGH | Ensure that IAM users are not assigned the Service Account User or Service Account Token Creator roles at project level. | accurics.gcp.IAM.137 |
| Identity and Access Management | gcp | HIGH | Ensure that Service Account has no Admin privileges. | accurics.gcp.IAM.138 |
google_storage_bucket_iam_member
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | gcp | HIGH | Ensure that Cloud Storage bucket is not anonymously or publicly Accessible. | accurics.gcp.IAM.120 |
google_compute_ssl_policy
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | gcp | MEDIUM | Ensure no HTTPS or SSL proxy load balancers permit SSL policies with weak cipher suites. | accurics.gcp.EKM.134 |
google_storage_bucket
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Logging and Monitoring | gcp | HIGH | Ensure that logging is enabled for Cloud storage buckets. | accurics.gcp.LOG.147 |
| Logging and Monitoring | gcp | HIGH | Ensure that object versioning is enabled on log-buckets. | accurics.gcp.LOG.146 |
| Identity and Access Management | gcp | MEDIUM | Ensure that Cloud Storage buckets have uniform bucket-level access enabled. | accurics.gcp.IAM.122 |
google_kms_crypto_key
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Security Best Practices | gcp | MEDIUM | Ensure Encryption keys are rotated within a period of 90 days. | accurics.gcp.EKM.139 |
| Security Best Practices | gcp | HIGH | Ensure Encryption keys are rotated within a period of 365 days. | accurics.gcp.EKM.007 |
google_project_iam_binding
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | gcp | HIGH | Ensure that IAM users are not assigned the Service Account User or Service Account Token Creator roles at project level. | accurics.gcp.IAM.136 |
| Identity and Access Management | gcp | MEDIUM | Ensure that corporate login credentials are used instead of Gmail accounts. | accurics.gcp.IAM.150 |
5.5 - GitHub Policies
github_repository
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | github | MEDIUM | Repository is Not Private. | accurics.github.IAM.1 |
github_repository_webhook
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Encryption and Key Management | github | MEDIUM | Insecure SSL is used for repository webhook. | accurics.github.EKM.2 |
github_organization_webhook
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Encryption and Key Management | github | MEDIUM | Insecure SSL is used for organization webhook. | accurics.github.EKM.1 |
5.6 - Docker Policies
docker_from
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | json | MEDIUM | Ensure platform flag with FROM command is not used for Docker file | AC_DOCKER_0001 |
| Infrastructure Security | json | MEDIUM | Ensure tag with FROM command exists and is not latest | AC_DOCKER_0041 |
docker_expose
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | json | HIGH | Ensure range of ports is from 0 to 65535 | AC_DOCKER_0011 |
docker_run
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | json | MEDIUM | Ensure Pinned Pip Package Version | AC_DOCKER_0010 |
| Infrastructure Security | json | HIGH | Ensure to avoid RUN with sudo command | AC_DOCKER_0007 |
| Infrastructure Security | json | MEDIUM | Ensure apt is not used with RUN command for Docker file | AC_DOCKER_0002 |
| Infrastructure Security | json | MEDIUM | Ensure dnf Update is not used for Docker file | AC_DOCKER_0003 |
| Infrastructure Security | json | MEDIUM | Ensure yum install allow manual input with RUN command for Docker file | AC_DOCKER_0004 |
| Infrastructure Security | json | MEDIUM | Ensure Yum Clean All is used after Yum Install | AC_DOCKER_0009 |
| Infrastructure Security | json | MEDIUM | Ensure root with RUN command is not used for Docker file | AC_DOCKER_0005 |
docker_workdir
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | json | HIGH | Ensure the use absolute paths for your WORKDIR. | AC_DOCKER_0013 |
5.7 - Kubernetes Policies
kubernetes_endpoint_slice
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | json | LOW | Ensure endpoint slice is not created or updated with loopback addresses as this acts as an attack vector for exploiting CVE-2021-25737 by an authorized user | AC_K8S_0113 |
kubernetes_service
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | json | LOW | Ensure the use of selector is enforced for Kubernetes Ingress or LoadBalancer service | AC_K8S_0114 |
| Infrastructure Security | json | MEDIUM | Restrict the use of externalIPs | AC-K8-NS-SE-M-0188 |
| Infrastructure Security | json | MEDIUM | Ensure that the Tiller Service (Helm v2) is deleted | AC-K8-NS-SE-M-0185 |
| Infrastructure Security | json | LOW | Nodeport service can expose the worker nodes as they have public interface | AC-K8-NS-SV-L-0132 |
| Infrastructure Security | json | MEDIUM | Vulnerable to CVE-2020-8554 | AC-K8-NS-SE-M-0188 |
kubernetes_ingress
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | json | MEDIUM | TLS disabled can affect the confidentiality of the data in transit | AC-K8-NS-IN-H-0020 |
kubernetes_pod
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Infrastructure Security | json | MEDIUM | Containers Should Not Share the Host Network Namespace | AC-K8-NS-PO-M-0164 |
| Infrastructure Security | json | MEDIUM | Image without digest affects the integrity principle of image security | AC-K8-NS-PO-M-0133 |
| Identity and Access Management | json | HIGH | Minimize Admission of Root Containers | AC-K8-IA-PO-H-0168 |
| Security Best Practices | json | Medium | CPU Request Not Set in config file. | AC-K8-OE-PK-M-0155 |
| Security Best Practices | json | HIGH | Default Namespace Should Not be Used | AC-K8-OE-PO-M-0166 |
| Infrastructure Security | json | MEDIUM | Do Not Use CAP_SYS_ADMIN Linux Capability | AC-K8-NS-PO-H-0170 |
| Security Best Practices | json | Medium | Memory Limits Not Set in config file. | AC-K8-OE-PK-M-0158 |
| Data Protection | json | MEDIUM | Ensure That Tiller (Helm V2) Is Not Deployed | AC-K8-DS-PO-M-0177 |
| Security Best Practices | json | LOW | No readiness probe will affect automatic recovery in case of unexpected errors | AC-K8-OE-PO-L-0130 |
| Identity and Access Management | json | MEDIUM | Default seccomp profile not enabled will make the container to make non-essential system calls | AC-K8-IA-PO-M-0141 |
| Identity and Access Management | json | MEDIUM | Container images with readOnlyRootFileSystem set as false mounts the container root file system with write permissions | AC-K8-IA-PO-M-0140 |
| Infrastructure Security | json | HIGH | Prefer using secrets as files over secrets as environment variables | AC-K8-NS-PO-H-0117 |
| Infrastructure Security | json | MEDIUM | Containers Should Not Share Host IPC Namespace | AC-K8-NS-PO-M-0163 |
| Infrastructure Security | json | MEDIUM | Apply Security Context to Your Pods and Containers | AC-K8-NS-PO-M-0122 |
| Data Protection | json | MEDIUM | Ensure Kubernetes Dashboard Is Not Deployed | AC-K8-DS-PO-M-0176 |
| Identity and Access Management | json | HIGH | Allowing hostPaths to mount to Pod arise the probability of getting access to the node’s filesystem | AC-K8-IA-PO-H-0138 |
| Identity and Access Management | json | MEDIUM | Some volume types mount the host file system paths to the pod or container, thus increasing the chance of escaping the container to access the host | AC-K8-IA-PO-M-0143 |
| Identity and Access Management | json | MEDIUM | Allowing the pod to make system level calls provide access to host/node sensitive information | AC-K8-IA-PO-H-0137 |
| Data Protection | json | MEDIUM | Vulnerable to CVE-2020-8555 (affected version of kube-controller-manager: v1.18.0, v1.17.0 - v1.17.4, v1.16.0 - v1.16.8, and v1.15.11 | AC-K8-DS-PO-M-0143 |
| Compliance Validation | json | MEDIUM | AlwaysPullImages plugin is not set | AC-K8-OE-PK-M-0034 |
| Identity and Access Management | json | MEDIUM | Unmasking the procMount will allow more information than is necessary to the program running in the containers spawned by k8s | AC-K8-IA-PO-M-0139 |
| Identity and Access Management | json | MEDIUM | AppArmor profile not set to default or custom profile will make the container vulnerable to kernel level threats | AC-K8-IA-PO-M-0135 |
| Identity and Access Management | json | MEDIUM | Containers Should Not Share Host Process ID Namespace | AC-K8-IA-PO-M-0162 |
| Infrastructure Security | json | MEDIUM | Containers Should Run as a High UID to Avoid Host Conflict | AC-K8-NS-PO-M-0182 |
| Identity and Access Management | json | MEDIUM | Minimize the admission of containers with the NET_RAW capability | AC-K8-IA-PS-M-0112 |
| Security Best Practices | json | LOW | No liveness probe will ensure there is no recovery in case of unexpected errors | AC-K8-OE-PO-L-0129 |
| Security Best Practices | json | LOW | No tag or container image with :Latest tag makes difficult to rollback and track | AC-K8-OE-PO-L-0134 |
| Security Best Practices | json | Medium | Memory Request Not Set in config file. | AC-K8-OE-PK-M-0157 |
| Compliance Validation | json | HIGH | Containers Should Not Run with AllowPrivilegeEscalation | AC-K8-CA-PO-H-0165 |
| Identity and Access Management | json | HIGH | Minimize the admission of privileged containers | AC-K8-IA-PO-H-0106 |
| Security Best Practices | json | Medium | CPU Limits Not Set in config file. | AC-K8-OE-PK-M-0156 |
| Infrastructure Security | json | MEDIUM | Restrict Mounting Docker Socket in a Container | AC-K8-NS-PO-M-0171 |
| Identity and Access Management | json | MEDIUM | Ensure that Service Account Tokens are only mounted where necessary | AC-K8-IA-PO-M-0105 |
kubernetes_role
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Identity and Access Management | json | HIGH | Ensure that default service accounts are not actively used in Kubernetes Role | AC-K8-IA-RO-H-0104 |
kubernetes_namespace
| Category | Resource | Severity | Description | Reference ID |
|---|---|---|---|---|
| Security Best Practices | json | LOW | No owner for namespace affects the operations | AC-K8-OE-NS-L-0128 |
6 - Contribution Guidelines
Contributing
Contributions are welcome, and they are greatly appreciated!
You can contribute in many ways:
Types of Contributions
Report Bugs
Report bugs at https://github.com/tenable/terrascan/issues.
If you are reporting a bug, please include:
- Your operating system name and version.
- Any details about your local setup that might be helpful in troubleshooting.
- Detailed steps to reproduce the bug.
Fix Bugs
Look through the GitHub issues for bugs. Anything tagged with “bug” and “help wanted” is open to whoever wants to implement it.
Implement Features
Look through the GitHub issues for features. Anything tagged with “enhancement” and “help wanted” is open to whoever wants to implement it.
Write Documentation
Terrascan could always use more documentation, whether as part of the official Terrascan docs, or even on the web in blog posts, articles, videos, and such.
Submit Feedback
The best way to send feedback is to file an issue at https://github.com/tenable/terrascan/issues.
If you are proposing a feature:
- Explain in detail how it would work.
- Keep the scope as narrow as possible, to make it easier to implement.
- Remember that this is a volunteer-driven project, and that contributions are welcome :)
Get Started!
Ready to contribute? Here’s how to set up terrascan for local development.
- Fork the
terrascanrepo on GitHub. - Clone your fork locally:
$ git clone git@github.com:your_name_here/terrascan.git
- Create a branch for local development:
$ git checkout -b name-of-your-bugfix-or-feature
Now you can make your changes locally.
- When you’re done making changes, check that your changes pass linting and tests. The following commands will simulate locally all checks executed as part of Terrascan’s CI pipeline:
$ make cicd
- Commit your changes and push your branch to GitHub::
$ git add .
$ git commit -m "Your detailed description of your changes."
$ git push origin name-of-your-bugfix-or-feature
- Submit a pull request through the GitHub website.
Pull Request Guidelines
Before you submit a pull request, check that it meets these guidelines:
- The pull request should include tests.
- If the pull request adds functionality or policies, the docs should be updated.
- Make sure all tests pass by running
make cicd.
7 - Changelog
v1.17.0 (2022-11-17)
Implemented enhancements:
- refs resolution #1445 (gaurav-gogia)
- bump goformation from v6 to v7 #1440 (gaurav-gogia)
- update cft map for elb and s3 bucket #1434 (gaurav-gogia)
- Include DirScanErrors info in SARIF file #1398 (shaopeng-gh)
Merged pull requests:
- fix remote source url #1437 (Rchanger)
- Update object.get first parameter #1433 (Matt2212)
- Update/release command #1430 (gaurav-gogia)
- updated terrascan version in deployment scripts #1429 (nasir-rabbani)
Changelog
v1.16.0 (2022-10-19)
Implemented enhancements:
- JSON Output has Logs for Standard Error #1378
- Malformed output after a parsing error #1326
- update rds instance cft map #1422 (gaurav-gogia)
- update libraries #1385 (gaurav-gogia)
Closed issues:
- installation error #1403
- Calling attention to your documentation… #1384
- Docs don’t mention pre-requirements #1345
- resource ID has an invalid format Dockerfile #1344
- Error message scanning IaC Types #1259
- False positive with AWS provider >=4.x style bucket resources #1219
Merged pull requests:
- Update RDS Policies #1424 (gaurav-gogia)
- Add Terrascan Sandbox link to README #1409 (khasty720)
- allow host policy update #1400 (DEVANSHUSHARMA1)
- Policy IDs update #1396 (gaurav-gogia)
- vuln tests #1394 (gaurav-gogia)
- Mention pre-requirements in the README #1375 (VeraBE)
- fixed typo of the function name #1373 (Antsaniaina)
- Add github-actions to dependabot #1365 (gliptak)
- adding PITR attribute mapping config for dyanmodb #1340 (harkirat22)
- container funcs to return dev friendly warnings #1319 (gaurav-gogia)
- [Snyk] Security upgrade alpine from 3.15.4 to 3.16 #1315 (bkizer-tenable)
- Add iac providers endpoint #1307 (khasty720)
- updated policy for kubernetes #1288 (harkirat22)
- Update README.md #1265 (sangam14)
Changelog
v1.15.2 (2022-06-13)
Closed issues:
- Export Windows files in release using zip extension #1280
Merged pull requests:
- Adding CFT support for new resources #1293 (shreyas-phansalkar-189)
- fixes: panic in case of zap logger init on windows os #1283 (Rchanger)
Changelog
v1.15.2 (2022-06-13)
Closed issues:
- Export Windows files in release using zip extension #1280
Merged pull requests:
Changelog
v1.15.1 (2022-05-20)
Merged pull requests:
- Support reading .terraformrc file from env var #1264 (Rchanger)
- CFT lambda conversion nil pointer check to avoid panic #1260 (Rchanger)
- Fix descriptions to install terrascan #1254 (yu-iskw)
- Rebranding repository to Tenable brand #1253 (cesar-rodriguez)
- Rebranding to Tenable #1246 (cesar-rodriguez)
- Update README.md #1245 (sangam14)
- fix: remove master ref check from release docker push job #1244 (Rchanger)
Changelog
v1.15.0 (2022-05-10)
Fixed bugs:
- Issue with Terrascan and CloudFormation #1235
Closed issues:
- Terrascan 1.13.2 version uses go 1.16.14 version which has High vulnerability. When can we expect the release with go version 1.17? #1190
Merged pull requests:
- Update Docker #1242 (cesar-rodriguez)
- Update mkdocs-material to 8.2.14 #1240 (pyup-bot)
- Fix panic while scanning cloudformation templates #1238 (patilpankaj212)
- Bump alpine from 3.14.6 to 3.15.4 in /build #1237 (dependabot[bot])
- Removing workflow file #1236 (bkizer-tenable)
- Bump github.com/hashicorp/go-getter from 1.5.7 to 1.5.11 #1233 (dependabot[bot])
- file out writer implementation #1229 (nasir-rabbani)
- mark ecr e2e test pending #1224 (Rchanger)
- Add dep scan #1223 (bkizer-tenable)
- Update alpine version #1222 (bkizer-tenable)
- support for new flag to define custom temp directory #1217 (Rchanger)
- Use Docker buildx for multi-platform support #1062 (rnsc)
Changelog
v1.14.0 (2022-04-01)
Implemented enhancements:
- [Feature]Option to provide temp directory path for download #1214 (Rchanger)
- Feature/endpoint policy download #1200 (gaurav-gogia)
- Feature/best effort cft file load #1168 (gaurav-gogia)
Fixed bugs:
- update lambda function mapper #1199 (gaurav-gogia)
- remove undefined template variable #1179 (gaurav-gogia)
Closed issues:
- Terrascan creates ~/.terrascan even though policy directory is supplied #1209
- Terrascan 1.13.2 version uses go 1.16.14 which has High vulnerability. When is the release with go 1.17 version expected? #1183
- Blocks of type “moved” not supported #1182
- Intermittent error running terrascan - rego_parse_error: unexpected assign token: non-terminated set #1180
- cli/run.go:110 scan run failed{error 26 0 failed to initialize OPA policy engine} #1178
- Can’t parse Terraform variable field:
nullable#1176 - AC_AWS_0214 not backward compatible #1172
- azurerm_key_vault_secret error not in line with tests #1163
- Support AWS Terraform provider v4 for S3 buckets #1162
Merged pull requests:
- terraform iac provider should proceed with static analysis when rootMod is not
nil#1211 (patilpankaj212) - skip policy download if -p flag used #1210 (Rchanger)
- Update README.md #1206 (sangam14)
- Update mkdocs to 1.3.0 #1203 (pyup-bot)
- remove source_code_hash mapping #1197 (patilpankaj212)
- Adds: dir scan errors in human readable output format #1196 (Rchanger)
- Update mkdocs-material to 8.2.6 #1195 (pyup-bot)
- add CODEOWNERS for terrascan #1194 (patilpankaj212)
- Adds: git in container which is required for go build #1193 (Rchanger)
- typo: Change “desitnation” to “destination”. #1192 (adyavanapalli)
- Add security policy #1189 (bkizer-tenable)
- skip vuln test for dependabot #1185 (Rchanger)
- Perform: go mod tidy #1184 (Rchanger)
- updating s3 bucket policies for v4 aws provider #1175 (harkirat22)
- Add backward compatible implementation of AC_AWS_0214 #1173 (HorizonNet)
- fix: reworded error to explain tests performed #1164 (beararmy)
- Bump go 1.17 #1026 (Rchanger)
Changelog
v1.13.2 (2022-02-22)
Implemented enhancements:
- Feature/s3 policy update #1153 (gaurav-gogia)
Fixed bugs:
- Bugfix/coginto pool #1159 (gaurav-gogia)
Closed issues:
- Is it possible to use terrascan in an offline environment #1154
- Support AWS provider version 4.0.0 #1152
- False positives and false negatives - AC_AWS_0215 / AWS.S3Bucket.DS.High.1043 #1139
- False positive: AWS.RDS.DataSecurity.High.0414 / AC_AWS_0058 #1135
- AC_GCP_0014 (dnsStateIsNotOn) false positive #1033
Merged pull requests:
- skip terrascan init for –config-with-error flag #1160 (nasir-rabbani)
- Bugfix/s3 user policy #1157 (gaurav-gogia)
- fix rds encryptionc check policy #1156 (gaurav-gogia)
- Update mkdocs-material to 8.2.1 #1155 (pyup-bot)
- Adds: missing release tag push step #1151 (Rchanger)
- Adding CFT scanning support for the resources: #1149 (shreyas-phansalkar-189)
Changelog
v1.13.1 (2022-02-10)
Implemented enhancements:
- update cft mapper #1148 (gaurav-gogia)
- update cft mapper #1143 (gaurav-gogia)
- Feature/eks msk vpc version #1140 (gaurav-gogia)
- Feature/rds sage dms load emr msk #1133 (gaurav-gogia)
- Feature/ec2 cog lambda acm cft #1129 (gaurav-gogia)
- Updates CloudFormation mapper to support additional resources #1120 (gaurav-gogia)
Closed issues:
- Issue with skipped violations using CircleCI and JUnit output format #1122
Merged pull requests:
- Add Policy AC_GCP_0296 - Service Attachment with ACCEPT_AUTOMATIC #1147 (hoexter)
- fix panic in cft #1146 (patilpankaj212)
- Fixes failing docker IaC provider test #1145 (Rchanger)
- [Snyk] Security upgrade alpine from 3.12.0 to 3.14 #1144 (snyk-bot)
- Update mkdocs-material to 8.1.10 #1141 (pyup-bot)
- Fix typos in docs and release_checklist #1138 (myersg86)
- add rule id to docs #1136 (jrobison-sb)
- add ability to output normalized resource config with errors #1134 (nasir-rabbani)
- Update mkdocs-material to 8.1.9 #1132 (pyup-bot)
- Allow internal github repos to pass AC_GCP_0231 & AC_GITHUB_0002 #1131 (briankanya)
- Update mkdocs-material to 8.1.8 #1124 (pyup-bot)
- Prevent adding both skipped and failure elements #1123 (gchappel)
- Updated discord link in readme #1118 (sangam14)
- Adds: logger in case of flag parsing fails #1115 (Rchanger)
- Update README.md #1109 (sangam14)
- Fix gcp policy AC_GCP_0014 - dnsStateIsNotOn (#1033) #1107 (hoexter)
- Allow tfplan format version 0.2 #1074 (mtranter)
Changelog
v1.13.0 (2022-01-05)
Closed issues:
Merged pull requests:
- Update mkdocs-material to 8.1.4 #1106 (pyup-bot)
- fix input CFT templates based on goformation structs #1105 (patilpankaj212)
- Update mkdocs-material to 8.1.3 #1101 (pyup-bot)
- Update mkdocs-material to 8.0.5 #1095 (pyup-bot)
- fix: update go mod to add missing dependencies #1094 (Rchanger)
- Update mkdocs-material to 8.0.3 #1092 (pyup-bot)
- fix: handles nil pointer while extracting container images #1076 (Rchanger)
- Update mkdocs-material to 7.3.6 #1075 (pyup-bot)
- updating policies to detect cve-2021-25742 #1071 (harkirat22)
- Fix Sarif file uri path invalid in Windows and update go-sarif to latest #1070 (shaopeng-gh)
- New k8s policy to detect CVE-2021-25742 #1069 (harkirat22)
- making change in imageVersionnotusinglatest.rego #1068 (shreyas-phansalkar-189)
Changelog
v1.12.0 (2021-10-21)
Fixed bugs:
- A scan should NOT crash if the notification doesn’t work as expected #1044
- Rotation period for KMS keys not correctly interpreted (GCP) #699
Closed issues:
- pre-commit hook reporting error with terrascan #1053
- Terrascan: Not working in a Repository referencing other repository #1030
- vulnerabilities found in accurics/terrascan_atlantis image #1029
Merged pull requests:
- Update mkdocs-material to 7.3.4 #1060 (pyup-bot)
- Add support for repo-url and branch name in CLI flags and scan output #1059 (nasir-rabbani)
- Update mkdocs to 1.2.3 #1058 (pyup-bot)
- Update mkdocs-material to 7.3.3 #1057 (pyup-bot)
- Add support for getting line numbers for all attributes #1055 (kanchwala-yusuf)
- Update atlantis base image #1054 (cesar-rodriguez)
- Fix notification webhook flow #1051 (nasir-rabbani)
- update container image version in helm and kustomize sources #1050 (dev-gaur)
- Accept notification webhook configs as CLI args #1042 (nasir-rabbani)
v1.11.0 (2021-10-07)
Implemented enhancements:
- How to ignore rules onto whole module included into HCL file #983
- Adds: support for harbor registry vulnerability fetching #1015 (Rchanger)
Fixed bugs:
- panic: value is null #1019
Closed issues:
- helm chart breaking due to invalid configfile name extension #1046
Merged pull requests:
- Fix #1046: helm chart breaking due to invalid configfile name extension #1047 (dev-gaur)
- fix permission issues in creating webhook mode logs file persistence #1045 (dev-gaur)
- Update mkdocs-material to 7.3.2 #1043 (pyup-bot)
- accepted 2xx in response code as success #1040 (nasir-rabbani)
- Optimized disk encryption check code on the azurerm_managed_disk resource #1037 (IrinaRaza)
- Update docs for AWS.LambdaFunction.Logging.Low.0472 policy #1027 (brandysnaps)
- fix: added null check before value conversion to avoid panic #1020 (Rchanger)
- Update mkdocs-material to 7.2.6 #1012 (pyup-bot)
- Update README.md #1011 (enmanuelmoreira)
- Adds: e2e tests for vulnerability #1009 (Rchanger)
- Adds additional dockerfile policies #984 (rishidhamija)
Changelog
v1.10.0 (2021-08-24)
Implemented enhancements:
- Add capability to extract references to container images in K8s ecosystem IaC #881
Fixed bugs:
- Terrascan does not exit with error code in pipeline or CLI #950
Closed issues:
- Links are Not formatted Properly in Contributor Doc #969
- Enabling dependabot or renovate for automatic dependency update #959
- AC_K8S_0131 triggers on a Namespace resource #957
- Integrity issue with Kustomize v4 support #956
- Add Support For ECR #927
- Add capability to extract references to container images in terraform #898
- Kustomize support says v3 but is actually v4 #891
Merged pull requests:
- Extract images from Dockerfiles #1002 (nasir-rabbani)
- Revert “update resource type to map[string]bool” #1001 (cesar-rodriguez)
- Upgrade helm.sh/helm/v3 to version 3.6.1 #1000 (patilpankaj212)
- Bump github.com/pelletier/go-toml from 1.8.1 to 1.9.3 #999 (dependabot[bot])
- Adds additional policies for dockerfile #996 (pavniii)
- terrascan should exit with non zero exit code when scan error are present #994 (patilpankaj212)
- Bump github.com/hashicorp/go-getter from 1.5.2 to 1.5.7 #993 (dependabot[bot])
- update resource type to map[string]bool #992 (patilpankaj212)
- docs: fixes links in contributing documentation #990 (cesar-rodriguez)
- Initial support for image scanning #989 (Rchanger)
- added binary based support for kustomize v2 and v3 #988 (nasir-rabbani)
- Docs: adds brew instructions to release checklist #987 (cesar-rodriguez)
- Update mkdocs-material to 7.2.4 #985 (pyup-bot)
- modify wait logic for service account creation in e2e validating webhook test #979 (patilpankaj212)
- Update mkdocs-material to 7.2.3 #978 (pyup-bot)
- Bump github.com/hashicorp/hcl/v2 from 2.10.0 to 2.10.1 #972 (dependabot[bot])
- Bump github.com/spf13/afero from 1.5.1 to 1.6.0 #970 (dependabot[bot])
- Adds: e2e test for docker IaC provider #968 (Rchanger)
- Fix dependency issue that caused dependabot to fail #966 (patilpankaj212)
- fix(policies): removing false-positive for K8s namespaces #961 (danmx)
- Extract Docker images from Terraform templates #937 (dev-gaur)
- Fixes supported Kustomize version (should be v4) #932 (dev-gaur)
- Extract Docker images from k8s YAML files #905 (dev-gaur)
v1.9.0 (2021-08-06)
Implemented enhancements:
- Dockerfile Support #798
- pre-commit hook #311
- Add support for CFT nested stacks #949
- Adds support for using Terraform modules cached locally #940
Fixed bugs:
- Helm chart scans use only 4 policies #946
Closed issues:
- Link to docks in README #944
- Ensure remote modules are downloaded only once #936
- Rule supression for specific resources #868
Merged pull requests:
- Fixes k8s policy filtering #963 (patilpankaj212)
- Update mkdocs-material to 7.2.2 #954 (pyup-bot)
- Adds Terrascan pre-commit #953 (mihirhasan)
- Add support for CFT nested stacks #949 (sigmabaryon)
- fix - remote repo scan with config only option generates panic #948 (patilpankaj212)
- Update mkdocs-material to 7.2.1 #947 (pyup-bot)
- Update README.md #945 (sangam14)
- Update helm chart progress checklist #943 (dev-gaur)
- Adds support for using Terraform modules cached locally #940 (Rchanger)
- Update mkdocs-material to 7.2.0 #939 (pyup-bot)
- Dockerfile support #849 (Rchanger)
v1.8.1 (2021-07-22)
Closed issues:
- terrascan init should not be triggered if the user only wants to generate normalised json. #926
- No rules are processed in GitlabCI #925
- Scanning remote modules doesn’t have same results as for scanning Terraform plan itself #923
- Module AWS.KMS.Logging.High.0400 seems to serve no purpose #917
- Secure ciphers are not used in CloudFront distribution #875
- Correct point in time recovery for DynamoDB still leads to violation #838
Merged pull requests:
- fix go mod files #941 (kanchwala-yusuf)
- Update mkdocs-material to 7.1.11 #938 (pyup-bot)
- Update mkdocs to 1.2.2 #935 (pyup-bot)
- K8s Policy to detect a service type Loadbalancer without a selector #931 (harkirat22)
- Fix #926: Do not initiate policy engine incase of –config-only flag #930 (dev-gaur)
- Update mkdocs-material to 7.1.10 #929 (pyup-bot)
- fix(sws/cloudfront): wrong check tls version #928 (frediana)
- fixes: broken doc links #921 (Rchanger)
- update getting started and Usage, fix links #920 (amirbenv)
- Update overview.md #919 (sangam14)
- Remove unnecessary KMS deletion window code #918 (matt-slalom)
- minor-doc-fix #916 (amirbenv)
- fix confusing error log message #914 (dev-gaur)
- add integrations overview and minor fixes #913 (amirbenv)
- Updating the dax cluster policy #909 (shreyas-phansalkar-189)
- add github-sarif writer for github suited sarif output #907 (dev-gaur)
- Add support for arm linked templates #903 (sigmabaryon)
- terraform 0.15 support #860 (dev-gaur)
v1.8.0 (2021-07-02)
Implemented enhancements:
- Add Support for new reference id field #786
Fixed bugs:
- Sarif output has wrong file path value for file scans #861
- ‘k8s’ key updated multiple times in policy package #439
Closed issues:
- Terrascan is failing in scan #887
- Refactor to Disable CGO #884
- Issue on Azure Pipelines: failed to initialize terrascan 1.7.0 #864
- Can’t skip rules with underscore #856
- Recursive Loop Scanning Terraform #851
- Improve filenames in remote modules #841
- Issues running terrascan in azure pipelines #835
Merged pull requests:
- fix error messages reported from hcl diags #911 (kanchwala-yusuf)
- add in-file instrumentation segment #910 (amirbenv)
- Minor documentation fixes #908 (brandysnaps)
- Use CGO independent package for sqlite #906 (kanchwala-yusuf)
- GH action doc - fix code block #902 (amirbenv)
- Update cicd-fix code block.md #901 (amirbenv)
- fixes: recursive loop when parent and child module has same local block #900 (Rchanger)
- Update mkdocs-material to 7.1.9 #895 (pyup-bot)
- Updates documentation on Terrascan github action #894 (cesar-rodriguez)
- fix usage overview links.md #893 (amirbenv)
- Split usage docs #890 (amirbenv)
- add proper values via metadata #888 (gaurav-gogia)
- Update mkdocs to 1.2.1 #886 (pyup-bot)
- Update Integration Docs.md #885 (amirbenv)
- k8s policies refactor #879 (gaurav-gogia)
- mod azure policies to improve parity with siac #878 (gaurav-gogia)
- Fix authorization header for http request #877 (kanchwala-yusuf)
- Adding Id fix for github policies #874 (shreyas-phansalkar-189)
- Bugfix/k8s id field #873 (gaurav-gogia)
- Add ID Field in Azure Policies #872 (gaurav-gogia)
- adding ID field for aws policies #871 (harkirat22)
- Adding missing Id field for GCP policies #870 (shreyas-phansalkar-189)
- Updating network security policies for GCP #869 (shreyas-phansalkar-189)
- improves: filename in remote module #867 (Rchanger)
- Adding AWS Network Security Policies #866 (shreyas-phansalkar-189)
- Change api, Add support for s3 bucket resource and better cft loader #865 (sigmabaryon)
- Fixes incorrect filepath reporting in sarif output & added e2e tests for sarif output #863 (dev-gaur)
- Bugfix/az nw sec policies #862 (gaurav-gogia)
- Update mkdocs-material to 7.1.8 #859 (pyup-bot)
- Fix AC_AZURE_0185 policy #858 (maxgio92)
- fixed sarif unit tests hardcoding code smell #857 (dev-gaur)
- fix broken link to
usage.md#855 (dan-hill2802) - Added “id” field support & policy validation tests #843 (nasir-rabbani)
- Add Microsoft Azure ARM as an IaC Provider #736 (gauravgahlot)
Changelog
v1.7.0 (2021-06-09)
Implemented enhancements:
- Enhancement: Support sarif as output format #775
- Admission Controller e2e tests #749
- Enhance terrascan docker to support all terrascan run modes #748
- Config file changes for server and admission controller #747
- Create Helm charts for the terrascan admission webhook setup. #685
- Enhancement: Use module instance name for download directory #672
Fixed bugs:
- Azure AKS failling to check the network policy status. #789
- Scan for terraform doesn’t error out if a module definition refers to a directory with no tf files #782
- Wrong detection of MemoryRequestsCheck,CpuRequestsCheck,noReadinessProbe and nolivenessProbe policy in k8s Job spec #767
- Update Docker build for terrascan to use numeric UID #766
- Wrong detection of AllowPrivilegeEscalation (policy AC-K8-CA-PO-H-0165) in K8s pod spec #721
- Failed to run prepared query error in opa/engine.go #709
- tfplan should use resource address for id field #702
- Rule IDs with spaces cannot be skipped #610
- AWS.CloudFront.Network Security.Low.0568 Doesn’t allow skipping due to space in filename #549
- Error parsing syntax if using complex query for dynamic ip_restriction in azurerm_function_app or azurerm_app_service ressource #433
Closed issues:
- Add support for YAML format for terrascan config file #807
- Add ID field #805
- Add a middleware to log incoming http(s) requests on terrascan server #784
- terrascan server: validation missing for –cert-path and –key-path #769
- show-passed should report passes only for the existing resources #757
- Out of the box handling of certificates in helm charts for terrascan in Server mode #756
- In-file Instrumentation #755
- Release 1.5.2 or 1.6.0 #745
- Issue in GCP Policyfile unrestrictedRdpAccess.rego #735
- accurics.azure.AKS.3 is defective #711
- Rule
lambdaNotEncryptedWithKmsshould not check for KMS when env vars are not being used #682 - Terrascan does not resolve env var for aws_rds_cluster attribute storage_encrypted #678
- Valid Terraform configuration fails with
s3EnforceUserAcl#659 - kmsKeyExposedPolicy:22: eval_builtin_error: json.unmarshal: invalid character ‘$’ looking for beginning of value} #627
- Terrascan not able to find terraform config files in a sub directory, but it works in case of k8s infrastructure type #622
- Potential nil-dereference found while fuzzing #611
- terrascan should have a
category-listcommand #597 - Improved Documentation #416
- Improve test coverage for k8s #400
Merged pull requests:
- Fixing the bug for google_kms_crypto_key policies #848 (shreyas-phansalkar-189)
- Fix AWS dynamo Db policy for point in time recovery #847 (harkirat22)
- Bugfix/use ref id old format #846 (gaurav-gogia)
- reference ids with & and <space> fixed #845 (gaurav-gogia)
- fixes: Terraform inner block reference resolution #844 (Rchanger)
- Bump up to Go/1.16 #836 (kanchwala-yusuf)
- [fix] Add Alternate names for k8s services #834 (rahulchheda)
- Support for spaces in policy reference_id #833 (nasir-rabbani)
- fix - type assertion check for hcl.Body in terraform iac provider #832 (patilpankaj212)
- Add ID Field for AWS Policies' Metadata #831 (gaurav-gogia)
- Policy to check CVE-2021-25737 #830 (harkirat22)
- Enhancing AWS policies #829 (harkirat22)
- aws s3 policy
s3EnforceUserAclupdate #828 (gaurav-gogia) - add check for env vars and kms #827 (gaurav-gogia)
- Add ID Field for K8s Policies' Metadata #826 (Avanti19)
- Do not trim resource id from tfplan json #825 (kanchwala-yusuf)
- Add ID Field for GCP Policies' Metadata #824 (gaurav-gogia)
- fix - source path for k8s file scan is absolute #821 (patilpankaj212)
- added pending test changes for config reader #820 (patilpankaj212)
- fix: moves the pending test to running #819 (Rchanger)
- fix multierror variable issue #818 (patilpankaj212)
- [feat.] Merge Webhook and Server Helm Chart #817 (rahulchheda)
- add support for YAML format for terrascan config file #816 (kanchwala-yusuf)
- Add AWS CFT as an IaC Provider #815 (mahendrabagul)
- fix failing e2e test #812 (patilpankaj212)
- Adding Aws new policies cloudTrail #810 (Avanti19)
- Feature/az id field #808 (gaurav-gogia)
- added support for sarif formatted violation reports #806 (dev-gaur)
- Adds support to scan config resources with applicable policies & Refactors filteration #803 (patilpankaj212)
- Adds: in-file instrumentation for resource prioritizing #802 (Rchanger)
- shifted opa engine warning message to debug log level #800 (dev-gaur)
- fix: added validation for module local source dir #793 (Rchanger)
- policy metadata changes to include
policy\_typeandresource\_type#792 (patilpankaj212) - Fix pod level securityContext support #790 (harkirat22)
- Fix policy code for securityContext and Probes #787 (harkirat22)
- add logging middleware for server #785 (dev-gaur)
- config file changes for terrascan server #780 (patilpankaj212)
- Automate generation of TLS Certs using Helm #779 (rahulchheda)
- Add webhook setup capability and remote repo scan capability in the helm charts #778 (dev-gaur)
- Changed description of policy file to match port. #777 (menzbua)
- Added source_range 0.0.0.0/0 (any) to avoid rule violations #776 (menzbua)
- support for
module namein violation summary #774 (patilpankaj212) - Modified the Dockerfile to use numeric UID #773 (Rchanger)
- adds e2e tests for validating webhook #772 (patilpankaj212)
- add validation for tls private key and cert file values #771 (dev-gaur)
- Documentation #768 (lalchand12)
- change docs to include docker subcommands.md #765 (amirbenv)
- shifted custom atlantis container source under integrations/ directory #758 (dev-gaur)
- Update mkdocs-material to 7.1.4 #746 (pyup-bot)
- Add a kustomize based guide for setting up terrascan server and validating webhook in kubernetes #739 (dev-gaur)
- Fix accurics.azure.AKS.3 #712 (xortim)
- Update mkdocs-redirects to 1.0.3 #710 (pyup-bot)
- Initial addition of terrascan helm chart #688 (jlk)
Changelog
v1.6.0 (2021-05-10)
Implemented enhancements:
- Atlantis Integration #686
- Enhancement: support for all iac scan for cli #673
- Feature request: scan sub-folders too #411
Fixed bugs:
- Admission Controller Doesn’t display feedback for kubectl “create” and “apply” #731
Closed issues:
- GKE Control Plane is exposed to few public IP addresses #743
- Error with finding Enable AWS CloudWatch Logs for APIs #730
- Task: Add to github actions ability to build/push terrascan_atlantis image #728
- accurics.azure.NS.161 does not work with tfplan #725
- terrascan “latest” docker image broken for tfplan #718
- Local expansion recursive infinite loop #690
Merged pull requests:
- Feature/aws new policies sp #751 (shreyas-phansalkar-189)
- Argocd doc volume field modification #742 (Rchanger)
- Update mkdocs.yml #741 (amirbenv)
- fix failing test #740 (patilpankaj212)
- AWS policy pack update #737 (harkirat22)
- Adding release checklist #734 (jlk)
- Gh action terrscan_atlantis release #733 (dev-gaur)
- adds agrocd integration dockerfile, scripts, doc and examples #732 (Rchanger)
- Fix NSG associations #727 (xortim)
- changes for argocd integration #724 (patilpankaj212)
- Update admission-controller-webhooks-usage.md #722 (amirbenv)
- fix - #718 #720 (patilpankaj212)
- doc: add homebrew badge #714 (chenrui333)
- update version #713 (chenrui333)
- adds skipped tests for server file scan when file is k8s yaml #706 (Rchanger)
- fixes infinte loop while local variable resolution #700 (patilpankaj212)
- add terrascan atlantis container files, scripts and doc. #684 (dev-gaur)
- adds support to scan directory with all iac providers in cli mode #674 (patilpankaj212)
- adds support to scan sub folders for terraform iac provider #640 (patilpankaj212)
Changelog
v1.5.0 (2021-04-23)
Fixed bugs:
- Recursive loop expanding variables in included module #675
- Terrascan doesn’t resolve terraform complex variables #656
- Panic while resolving floating point variable #652
- Terrascan using absolute path for “source” value of resource #642
- Failed to initialize terrascan. error : failed to install policies #614
- Terrascan not able to read modules within a subdirectory #600
- Terrascan init command doesn’t work with -c flag #550
Closed issues:
- Not able to scan repo when google terraform module defined #681
- The link referencing the documentation to integrate Terrascan into CI/CD is broken #669
- Make saving of “admission request” configurable via an option in the config file for the validating admission webhook #664
- Add API_KEY to the /logs endpoint for the validating admission webhook #662
- Panic: not a string #647
- unit tests and e2e tests failing on windows #639
- Add support for private terraform repos #631
- policy not evaluating #629
- Terrascan does not support to download modules via SSH #621
- terrascan scan fails if path and rego_subdir are not provided together in the toml configfile #619
- Getting error while running scan on our terraform repo #607
- Terrascan not found policy id #601
Policies ViolatedandViolated Policiesare confusing. #598- Invalid categories not being validated from config file #594
- Terrascan API server’s file scan doesn’t work for k8s yaml files #584
- Add
/go/binto the PATH variable in Docker image #577 - terrascan scan command doesn’t work with TERRASCAN_CONFIG env variable #570
- Format junit-xml need to have passed test results, not only failed test #563
- optimize policy download process in
terrascan init#535
Merged pull requests:
- Release v1.5.0 #689 (kanchwala-yusuf)
- Adds support to configure dashboard mode in k8s validating webhook #683 (patilpankaj212)
- Updating documentation for k8s admission control #679 (kanchwala-yusuf)
- Fix recursive variable reference resolution #677 (patilpankaj212)
- Update mkdocs-material to 7.1.2 #676 (pyup-bot)
- Fixes broken link in README #671 (cesar-rodriguez)
- Docs- fix argo image path.md #667 (amirbenv)
- Makes saving of admission requests configurable via a config file option #665 (kanchwala-yusuf)
- Add authentication with API key for the /logs endpoint #663 (kanchwala-yusuf)
- Fixes docs format #661 (cesar-rodriguez)
- Update mkdocs.yml #660 (amirbenv)
- Support for authenticated tf module download #658 (jlk)
- Fix - terraform complex variables are not getting resolved #657 (patilpankaj212)
- Reorganized and Updated docs #655 (amirbenv)
- Fix- panic when terraform list variable doesn’t have a type #654 (patilpankaj212)
- Fix panic for floating point variables #653 (patilpankaj212)
- Adding support to scan IAC from atlantis workflow #648 (jlk)
- Fix - k8s resources config data has absolute source paths for resources #644 (patilpankaj212)
- Fix - terrascan not able to read modules within a subdirectory #641 (patilpankaj212)
- Add /go/bin to PATH. #637 (seancallaway)
- Update mkdocs-material to 7.1.0 #636 (pyup-bot)
- Fix windows tests #635 (patilpankaj212)
- Fix kustomize scan breakage on windows #630 (dev-gaur)
- Update route53LoggingDisabled.rego to ignore private zones #626 (matt-slalom)
- Adding openssh for downloading modules via ssh #625 (sachinar)
- Fix - init behavior change #624 (patilpankaj212)
- Add support for validating admission webhook in terrascan #620 (kanchwala-yusuf)
- Policy download refactor #618 (dev-gaur)
- Update mkdocs-material to 7.0.6 #615 (pyup-bot)
- Log error in LoadIacDir before continuing #613 (jlk)
- K8S Risk Category Changes #608 (Avanti19)
- GCP Risk Category Changes #606 (shreyas-phansalkar-189)
- Category flag e2e tests #605 (gaurav-gogia)
- Azure Risk Category Changes #604 (gaurav-gogia)
- AWS Risk Category Changes #603 (harkirat22)
- Bugfix/revert policies #602 (kanchwala-yusuf)
- Server mode: take file extension from uploaded file #593 (jlk)
- filepath fixes in e2e tests #591 (patilpankaj212)
- Update mkdocs-material to 7.0.5 #590 (pyup-bot)
- update helm default chart name and namespace values #589 (williepaul)
- v1.4.0 doc updates #588 (cesar-rodriguez)
- Terrascan K8s New categories and ruleRef ID changes #583 (Avanti19)
- GCP Category Changes #582 (shreyas-phansalkar-189)
- AWS new Categories #581 (harkirat22)
- New Policies for Azure & Category Updates. #580 (gaurav-gogia)
- Terrascan init and config handling refactor #576 (dev-gaur)
- Feature: add options to specify desired categories of violations to be reported #547 (gaurav-gogia)
v1.4.0 (2021-03-05)
Implemented enhancements:
- Scanning terraform plan files #407
- Adds support for junit xml output #527
- Adds e2e test scenarios for help and scan command #564
- Adds e2e tests for api server #585
- Please checkout our new Github Action!
Fixed bugs:
- Fixed a few bugs in the init command and downloading of fresh policies, including #561
- Difference in violated policies for the same terraform file #519
- false positive for AWS.Instance.NetworkSecurity.Medium.0506 #404
- accurics.gcp.IAM.122 needs to take into account the new name for Uniform bucket-level access flag #329
- fix the ‘repo already exist’ bug and improve error logging for terrascan init #552 (dev-gaur)
Closed issues:
- terrascan API server’s file scan always returns the resource config #578
- Issue on Azure DevOps Agents since 1.3.2 : failed to initialize terrascan #561
- Could not get terrascan init to work - would not download policy documents #551
Merged pull requests:
- release 1.4.0 #586 (kanchwala-yusuf)
- adds e2e tests for api server #585 (patilpankaj212)
- adds support to use ‘config_only’ attribute in api server’s file scan #579 (patilpankaj212)
- adds support to display passed rules #572 (patilpankaj212)
- Update mkdocs-material to 7.0.1 #567 (pyup-bot)
- fix filepaths and home directory lookup #566 (dev-gaur)
- adds e2e test scenarios for help and scan command #564 (patilpankaj212)
- Adds support for scanning tfplan json file #562 (kanchwala-yusuf)
- fix: renamed the json file to remove spaces #560 (harkirat22)
- fix: Changed the description message to handle the violation correctly #559 (harkirat22)
- bump versions to v1.3.3 #558 (dev-gaur)
- updated go module files #557 (dev-gaur)
- Initial changes for e2e testing framework #553 (patilpankaj212)
- Add code of conduct #545 (jlk)
- Fixes incorrect description of RDS encryption policy #542 (alex-petrov-vt)
- changes in log level and messages for load iac functions #541 (patilpankaj212)
- Update mkdocs-material to 6.2.8 #539 (pyup-bot)
- Updates docs for v1.3.2 #537 (cesar-rodriguez)
- update readme for v1.3.2 #534 (dev-gaur)
- fix - improved description for init command in help #532 (nathannaveen)
- Adds support for junit xml output #527 (patilpankaj212)
- enhancement: scan terraform registry modules as remote type #513 (patilpankaj212)
- support for terraform registry remote modules #505 (patilpankaj212)
- feature: add options to specify desired severity level of violations to be reported #501 (dev-gaur)
- Bump github.com/spf13/cobra from 1.0.0 to 1.1.1 #493 (dependabot[bot])
v1.3.2 (2021-02-03)
Fixed bugs:
- terrascan init should download new policies #521
Closed issues:
- How to get rid of “Anonymous, public read access to a container and its blobs can be enabled in Azure Blob storage. This is only recommended if absolutely necessary.” #405
- False Positive for accurics.azure.NS.161 when Security Groups Association and Subnets are defined indepently from VNet #391
- Calico is not supported as a valid Network Security for azurerm_kubernetes_cluster #376
Merged pull requests:
- Update readme for v1.3.2 #534 (dev-gaur)
- bump terrascan version to v1.3.2 #533 (dev-gaur)
- refactor init command for robust policy download checks #531 (dev-gaur)
- terrascan init will download new policies. #529 (dev-gaur)
- bugfix: Checks for security group association defined independently from vnet #526 (harkirat22)
- Update mkdocs-material to 6.2.7 #524 (pyup-bot)
- Fixed typos in docs #523 (gauravgahlot)
- Enhancement: new set of policies for AWS EC2 instance. #522 (harkirat22)
- Harkirat22/bug fix #520 (harkirat22)
- fixes #376 #518 (gaurav-gogia)
- fixes #405 #517 (gaurav-gogia)
- Policy/aws launch config #516 (harkirat22)
- add support for pod container #515 (harkirat22)
- Update mkdocs-material to 6.2.6 #514 (pyup-bot)
- Update README.md and changelog for 1.3.1 #509 (amirbenv)
v1.3.1 (2021-01-22)
Implemented enhancements:
- Support for remote modules
- Tag container image with release version #504
Fixed bugs:
- Build error on ARM MacOS
- terrascan consider source = “terraform-aws-modules/vpc/aws” as local path #418
- Failed to read module directory #332
Closed issues:
- Custom Variable Validation no longer experiemental in 0.13 #500
Merged pull requests:
- release v1.3.1 #508 (kanchwala-yusuf)
- fix dependencies that were breaking the darwin/arm64 build #507 (williepaul)
- support for terraform registry remote modules #505 (patilpankaj212)
- Readme rule supression #503 (amirbenv)
- Bump github.com/hashicorp/go-retryablehttp from 0.6.6 to 0.6.8 #496 (dependabot[bot])
- Bump github.com/hashicorp/go-getter from 1.5.1 to 1.5.2 #495 (dependabot[bot])
v1.3.0 (2021-01-19)
Implemented enhancements:
- Prints output in human friendly format #168
- Support for rule suppression using terraform comments,kubernetes annotations, cli arguments, and config file.
- New Policies for Kubernetes #480
- Tag released Docker images #398
- Add policy for checking insecure_ssl configuration for github_repository_webhook in GitHub provider #355
- Introduced support for terraform .14 and .13. Note: This will introduce some breaking changes for terraform v.12 files, even if using –iac-version v.12 flag. Notably we will no longer support multiple providers blocks, and certain references inside provisioner blocks (objects other than self, count or each, where when = destroy) . For more details see: https://github.com/hashicorp/terraform/releases/tag/v0.13.0
Fixed bugs:
- terrascan doesn’t allow registering multiple versions for an iac-type #471
- Debug resource lock #432
- terrascan panic: not a string #412
- False positive for aws rule vpcFlowLogsNotEnabled #408
- accurics.GCP.EKM.132 and accurics.GCP.EKM.131 wrong violation using disk_encryption_key #382
- s3EnforceUserACL - False Positive #359
- How to fix accurics.azure.EKM.20 #331
- Why accurics.gcp.IAM.104 suggests enabling a client certificate? #330
Closed issues:
- terraform can’t detect violations in terraform modules #468
- uniformBucketEnabled.rego referencing deprecated config #453
- Unable to run terrascan scan #446
- Terrascan doesn’t exit with error on CLI or Parsing errors. #442
- Terrascan Failure When Using Terraform 13 + Variable Validation #426
- Update policy example in documentation to use latest GitHub implementation #422
- Fix link to repo playground in policies documentation #421
- terrascan scan crashes with runtime: goroutine stack exceeds 1000000000-byte limit #406
- Typo error in the terrascan Architecture page #403
- accurics.gcp.OPS.114 should also check for cos_containerd image #395
- accurics.gcp.NS.112 suggest basic auth is enabled when is not #394
- Test coverage missing for kustomize iac-provider #379
- Why is vpcFlowLogsNotEnabled determined to be a violation? #352
Merged pull requests:
- update version to v1.3.0 #502 (kanchwala-yusuf)
- Add v13 flag option for terraform iac #499 (dev-gaur)
- Fix: potential bug added in PR #470 #497 (dev-gaur)
- Bump sigs.k8s.io/kustomize/api from 0.7.1 to 0.7.2 #494 (dependabot[bot])
- Bump github.com/mattn/go-isatty from 0.0.8 to 0.0.12 #492 (dependabot[bot])
- solves issue #382, and improved policy to relate disk with the instance #490 (harkirat22)
- solves issue #331 #489 (harkirat22)
- Update mkdocs-material to 6.2.5 #488 (pyup-bot)
- Bump go.uber.org/zap from 1.13.0 to 1.16.0 #486 (dependabot[bot])
- Bump github.com/spf13/afero from 1.3.4 to 1.5.1 #485 (dependabot[bot])
- Bump github.com/iancoleman/strcase from 0.1.1 to 0.1.3 #484 (dependabot[bot])
- Bump github.com/hashicorp/go-version from 1.2.0 to 1.2.1 #482 (dependabot[bot])
- Bump github.com/pelletier/go-toml from 1.8.0 to 1.8.1 #481 (dependabot[bot])
- Policy update 2021 01 14 #480 (williepaul)
- fix panic for list variables #479 (patilpankaj212)
- adding an else condition to relate management lock with resource group #476 (harkirat22)
- adding an else condition to relate the flow log with vpc #475 (harkirat22)
- including a check for verifying in-line policy is included #474 (harkirat22)
- adding rule to check if waf is enabled at cloud front distribution #473 (harkirat22)
- Added terraform v14 support besides v12. #470 (dev-gaur)
- support comment with rule skipping for resource and scan summary modifications #466 (patilpankaj212)
- recognize metadata.generateName #465 (acc-jon)
- Update mkdocs-material to 6.2.4 #464 (pyup-bot)
- Update README.md #463 (amirbenv)
- Deprecated gcs bucket #462 (jdyke)
- changed the description to include the vulnerable versions #460 (harkirat22)
- Fix exit code on error #458 (patilpankaj212)
- policy for CVE-2020-8555 #457 (harkirat22)
- Update README.md #456 (amirbenv)
- rule skipping for resources in k8s #455 (patilpankaj212)
- terrascan argo-cd instructions #454 (storebot)
- Adds CI/CD integration docs #452 (cesar-rodriguez)
- Bump github.com/zclconf/go-cty from 1.2.1 to 1.7.1 #449 (dependabot[bot])
- Bump sigs.k8s.io/kustomize/api from 0.6.5 to 0.7.1 #448 (dependabot[bot])
- Bump github.com/gorilla/mux from 1.7.4 to 1.8.0 #447 (dependabot[bot])
- Update mkdocs-material to 6.2.3 #445 (pyup-bot)
- deps: add dependabot support #444 (chenrui333)
- bump go to 1.15 #443 (chenrui333)
- implement scan and skip rules #441 (patilpankaj212)
- scan command refactor #436 (patilpankaj212)
- Fixes dead link to old getting started page #435 (cesar-rodriguez)
- Add support to extract rules to skip from terraform comments #434 (kanchwala-yusuf)
- bash output improvements #431 (patilpankaj212)
- APE-1319: Revamped Getting Started Section #430 (acc-jon)
- Add policy AC-K8-NS-SE-M-0188 for CVE-2020-8554 #428 (gauravgogia-accurics)
- set console mode on windows so colors render #427 (acc-jon)
- Update mkdocs-material to 6.1.7 #425 (pyup-bot)
- Update policy example in the documentation #424 (HorizonNet)
- Fix link to rego playground in policies documentation #423 (HorizonNet)
- hopefully remove test failures due to non-deterministic comparisons #420 (acc-jon)
- IMDSv1 policy: update category, description #419 (acc-jon)
- IMDSv1 check policy #417 (harkirat22)
- Add Docker image release tagging on release #410 (HorizonNet)
- Fix typo in architecture documentation #409 (HorizonNet)
- accurics.gcp.IAM.104 Fire rule when client certificate is enabled #402 (lucas-giaco)
- Update mkdocs-material to 6.1.6 #401 (pyup-bot)
- Added Unit test coverage for Kustomize V3 Iac-provider #399 (dev-gaur)
- Fixes GCP cos node image policy #397 (cesar-rodriguez)
- #394: recognize that empty values for username and password in master… #396 (acc-jon)
- Fix infinite loop on variable resolution #393 (dinedal)
- Remove demo badge #389 (kklin)
- Update mkdocs-material to 6.1.5 #387 (pyup-bot)
v1.2.0 (2020-11-16)
Implemented enhancements:
- Add support for Helm #353
- Add ‘git’ to container image, or run container as ‘root’ user by default #349
- Add policy for checking insecure_ssl configuration for github_organization_webhook in GitHub provider #339
- Rule for github_repository seems to be wrongly placed under gcp #325
Fixed bugs:
- Fail to validate when there are multiple properties with the same name in a resource #1
Closed issues:
- Deep modules location mis-proccessed. #365
- 20MB binary file included in repo now #364
- Private GitHub repositories are not recognized with version 3.0.0+ of GitHub provider #326
- Terrascan -var-file=../another dir #144
- Error in test_aws_security_group_inline_rule_open and test_aws_security_group_rule_open #138
- Intial setup after installation #136
- Add support for data sources #3
- Support from modules #2
Merged pull requests:
- Bring Go to 1.15 in Github Actions #384 (gliptak)
- Bring Go to 1.15 in Github Actions #383 (gliptak)
- fix a bug when rendering subcharts #381 (williepaul)
- Added kustomize support #378 (dev-gaur)
- Adds support for Helm v3 #377 (williepaul)
- Update mkdocs-material to 6.1.4 #374 (pyup-bot)
- properly handle nested submodules (#365) #373 (acc-jon)
- Address #365 by properly handling submodule path #372 (acc-jon)
- Update mkdocs-material to 6.1.3 #371 (pyup-bot)
- Update mkdocs-material to 6.1.2 #370 (pyup-bot)
- Allow use of multiple policy types (scan -t x,y or scan -t x -t y) #368 (acc-jon)
- Remove large binary that was included in the repo #366 (cesar-rodriguez)
- fix send request method, previously hardcoded #361 (kanchwala-yusuf)
- Add git binary to terrascan docker image, required by downloader #360 (kanchwala-yusuf)
- Adds new policies/regos for AWS serverless services #357 (cesar-rodriguez)
- Update mkdocs-material to 6.1.0 #356 (pyup-bot)
- Allow configuration of global policy config, fix some typos #354 (acc-jon)
- Feature/support resolve variable references #351 (kanchwala-yusuf)
- Add new policy for checking insecure_ssl on github_organization_webhook #350 (HorizonNet)
- Update mkdocs-material to 6.0.2 #348 (pyup-bot)
- Add support for colorized output #347 (acc-jon)
- Update mkdocs-material to 6.0.1 #346 (pyup-bot)
- Adds support for remote Terraform modules and scanning remotely for other IaC tools #345 (kanchwala-yusuf)
- fix supported providers unit test, sort the wanted result #344 (kanchwala-yusuf)
- Fix typo on AWS IAM account password policy rego name #343 (kmonticolo)
- Update mkdocs-material to 5.5.14 #340 (pyup-bot)
- Adds docs section for GitHub policies #337 (cesar-rodriguez)
- Automatically populate usage with supported IaC providers, versions, and policies #336 (kanchwala-yusuf)
- Add line about kubernetes YAML/JSON support #335 (williepaul)
- Add policy set for GitHub provider #334 (HorizonNet)
- Add check for visibility for github_repository #333 (HorizonNet)
- Add instructions for booting terrascan demo #319 (kklin)
v1.1.0 (2020-09-16)
Implemented enhancements:
- Initial kubernetes support #313 (williepaul)
- Adds different exit code when issues are found #299 (cesar-rodriguez)
- Adding terrascan to Homebrew #293
Fixed bugs:
- Oudated Docker image #294
- Error with XML output #290
- Fixed checkIpForward rule (gcp) #323 (williepaul)
Closed issues:
- Terrascan wrongly reports a accurics.gcp.NS.130 (checkIpForward) violation #320
- Allow structure output (Json) #252
- Throwing Errors when parsing nested brackets in HCL #233
- Be able to generate xml/html reports #119
Merged pull requests:
- Revert “fixed a bug in checkIpForward” #322 (cesar-rodriguez)
- Fixed a bug in checkIpForward #321 (williepaul)
- Move server command out of ENTRYPOINT and into CMD #318 (williepaul)
- Send logs to stderr instead of stdout #317 (williepaul)
- Fix template rendering bug #316 (williepaul)
- chore(docs): add homebrew installation #315 (chenrui333)
- Update badges in readme #314 (acc-jon)
- Update mkdocs-diagrams to 1.0.0 #312 (pyup-bot)
- Add support to print resource config as an output #309 (kanchwala-yusuf)
- Manage relative module path #308 (guilhem)
- Update mkdocs-material to 5.5.12 #307 (pyup-bot)
- chore(docs): fix indent of tar extraction #306 (zmarouf)
- Fixes issue template and rego capitalization #301 (cesar-rodriguez)
- Update mkdocs-material to 5.5.8 #300 (pyup-bot)
- Update about.md #298 (Upa-acc)
- Updated policies to the latest set #297 (williepaul)
- Fixes docker latest tag #296 (cesar-rodriguez)
- Typo fixes #295 (erichs)
- Update mkdocs-material to 5.5.7 #292 (pyup-bot)
- Fix xml output #291 (kanchwala-yusuf)
1.0.0 (2020-08-16)
Major updates to Terrascan and the underlying architecture including:
- Pluggable architecture written in Golang. We updated the architecture to be easier to extend Terrascan with additional IaC languages and support policies for different cloud providers and cloud native tooling.
- Server mode. This allows Terrascan to be executed as a server and use it’s API to perform static code analysis
- Notifications hooks. Will be able to integrate for notifications to external systems (e.g. email, slack, etc.)
- Uses OPA policy engine and policies written in Rego.
0.2.3 (2020-07-23)
- Introduces the ‘-f’ flag for passing a list of “.tf” files for linting and the ‘–version’ flag.
0.2.2 (2020-07-21)
- Adds Docker image and pipeline to push to DockerHub
0.2.1 (2020-06-19)
- Bugfix: The pyhcl hard dependency in the requirements.txt file caused issues if a higher version was installed. This was fixed by using the “>=” operator.
0.2.0 (2020-01-11)
- Adds support for terraform 0.12+
0.1.2 (2020-01-05)
- Adds ability to setup terrascan as a pre-commit hook
0.1.1 (2020-01-01)
- Updates dependent packages to latest versions
- Migrates CI to GitHub Actions from travis
0.1.0 (2017-11-26)
- First release on PyPI.
* This Changelog was automatically generated by github_changelog_generator
* This Changelog was automatically generated by github_changelog_generator
* This Changelog was automatically generated by github_changelog_generator